Ransom.WannaCrypt

Short bio
Ransom.WannaCrypt is Malwarebytes detection name for a ransomware application that will encrypt files on a victim machine and demand payment to retrieve the information. Ransom.WannaCrypt has self-propagatingcapabilities via SMB exploits. Ransom.WannaCrypt appends the extension .WCRY to in encrypted files and demands a payment of $300 – $600 in Bitcoin for decryption.Ransom.WannaCrypt can communicate via encrypted Tor channels with command-and-control (C&C)servers controlled by the attackers.
Symptoms
Ransom.WannaCrypt may run silently in the background during the encryption phase and not provide any indication of infection to the user. Ransom.WannaCrypt may prevent the execution of Antivirus programs and other Microsoft Windows security features and may prevent system restoration as a means to solicit payment. Ransom.WannaCrypt may display a warning after successful encryption of the victim machine.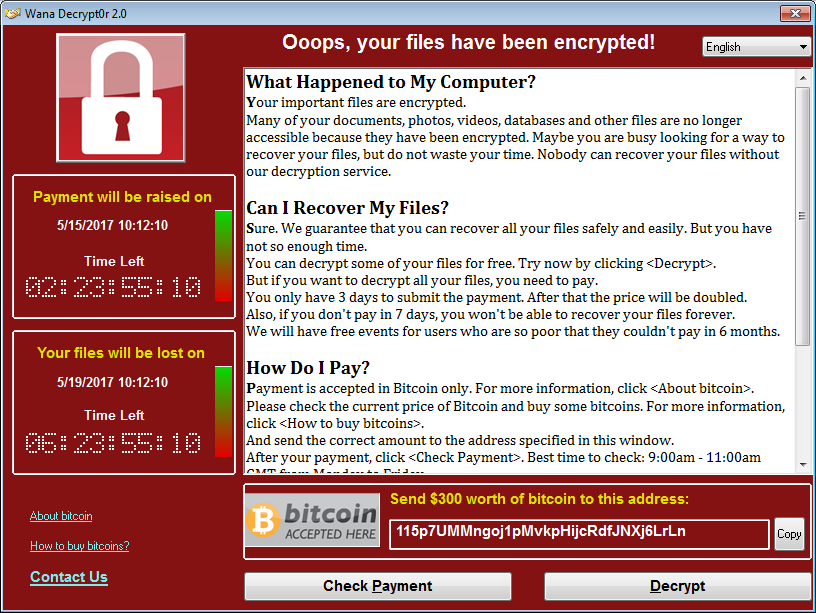
Type and source of infection
Ransom.WannaCrypt has a unique propagation methodology and is not distributed via malicious spam email or exploit kit. Ransom.WannaCrypt is spread by taking advantage of a vulnerability in Microsoft’s Server Message Block (SMB) protocol. The vulnerability has been widely known as EternalBlueand was released as part of the collection tools reportedly stolen by ShadowBrokers. Once successful exploitation of a vulnerable system occurs, Ransom.WannaCrypt looks for other vulnerable PC’s and attempts to automatically spread itself to any computer found.
Aftermath
Systems affected by ransomwareare rendered unusable due to files that are typically used for regular operations being encrypted.Affected users who choose to pay the threat actors behind ransomware campaigns in exchange for access to data may find that they don’t get their files back. There is also no sure way to know that threat actors will honor their end of the deal after paying the ransom.Affected users who chose to pay the threat actors may also find themselves likely targets for future ransomware campaigns.Data held hostage that wasn’t given back to users or deleted after the ransom has been paid can be used by threat actors either to (a) sell on the black market or (b) create a profile of the user they can use for fraud.
Protection
Malwarebytes protects users from Ransom.WannaCrypt by using Anti-Ransomware and Anti-Exploit technology.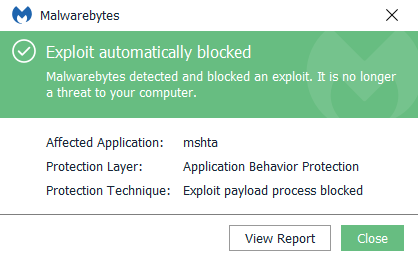
Home remediation
Malwarebytes can detect and remove Ransom.WannaCrypt without further user interaction.
- Please download Malwarebytesto your desktop.
- Double-click MBSetup.exeand follow the prompts to install the program.
- When your Malwarebytes for Windowsinstallation completes, the program opens to the Welcome to Malwarebytes screen.
- Click on the Get started button.
- Click Scan to start a Threat Scan.
- Click Quarantineto remove the found threats.
- Reboot the system if prompted to complete the removal process.
Take note, however, that removing this ransomware does not decrypt your files.The third-party decryptor for Ransom.WannaCrypt known as Wanakiwican be downloaded here.
Business remediation
How to remove Ransom.WannaCrypt with the Malwarebytes Nebula console
You can use the Malwarebytes Anti-Malware Nebula console to scan endpoints.
Nebula endpoint tasks menu
Choose the Scan + Quarantine option. Afterwards you can check the Detections pageto see which threats were found.
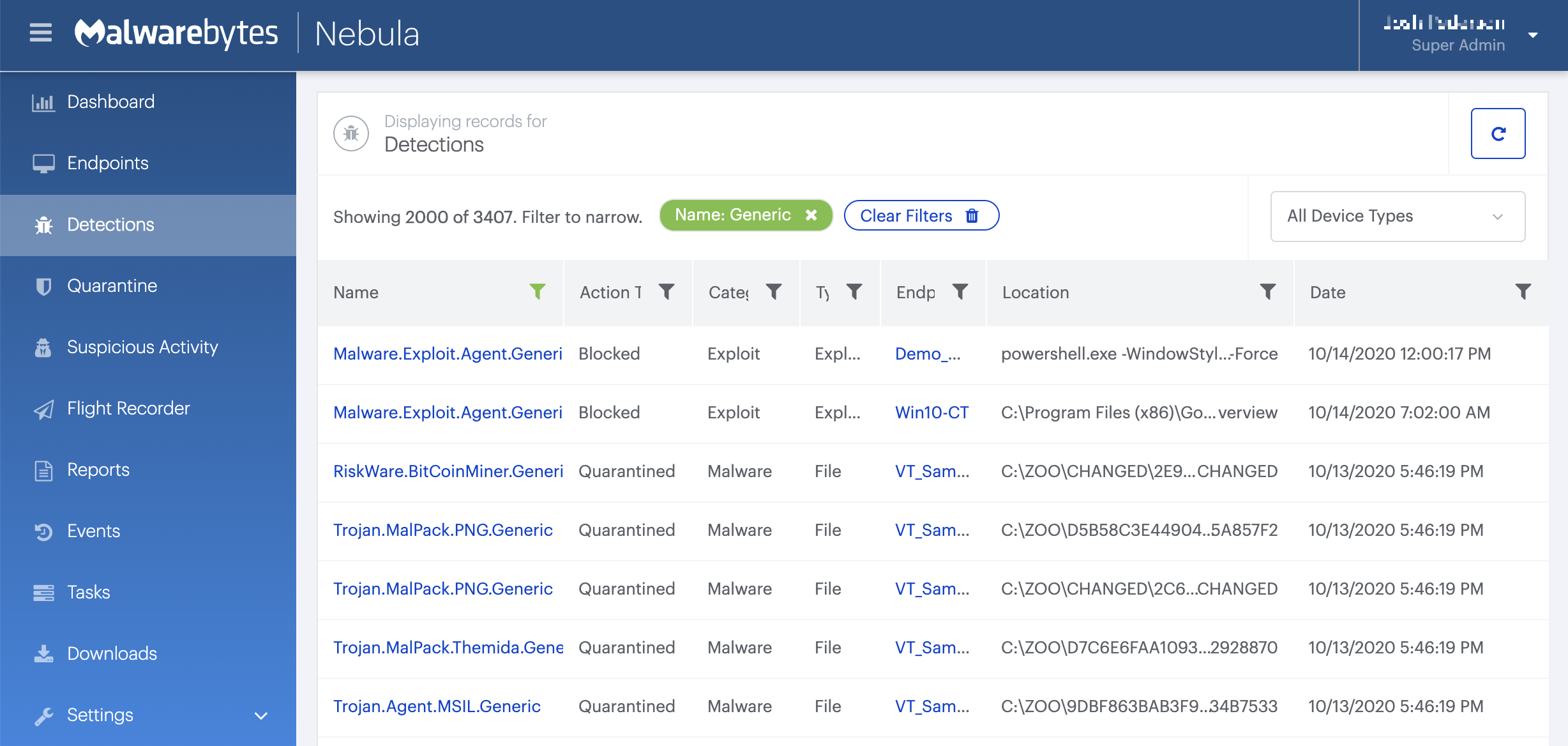
On the Quarantine pageyou can see which threats were quarantined and restore them if necessary.