“Over the years, phishing attacks have changed, as with most things, and have been segmented into different groups of variants.” –Me
If there is one thing you can say about cybercriminals, it’s that they are adaptive. As I mentioned last week, phishing attacks have evolved from just fake web pages and official looking emails to fake web pages and official looking posts and messages through social networks and online games. In fact, social networking itself has been the catalyst that spawned a whole new breed of phishing attacks and the worst part is, it’s easier now.
In this post, we will expand on our Phishing 101 series by discussing the more modern and more unique side to phishing, namely ‘Spear Phishing’ and phishing on the social media highway.
Spear Phishing Emails
Spear Phishing refers to the attempt to phish a specific user or group of users by using specific subjects which appeal specifically to the target user or referencing unique identification which provides a sense of legitimacy to the user. These kinds of attacks are usually used in conjunction with a group of targeted attacks leading to an end goal of accessing specific systems or information. While I could not obtain any spear phishing attacks used in the wild, I have created an example for you.
In the example, I have received an email from my favorite fictional game ‘StoneCraft’. The email references my ‘StoneCraft’ user name of ‘ILIKETURTLES’ and requests that I change my password on my account because of a security compromise on their end. They provide me a link to my account settings as well:
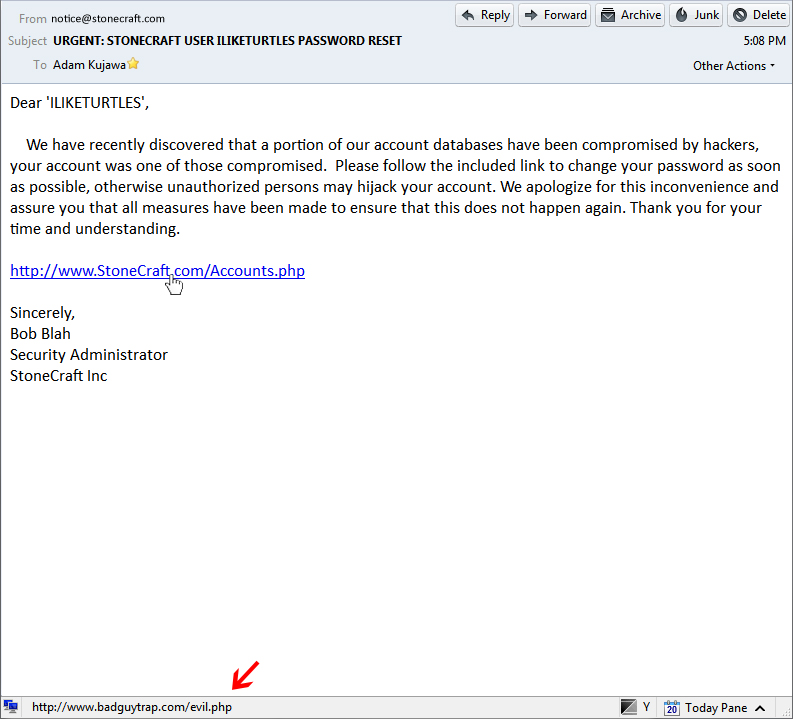
This email looks official enough, the ‘FROM’ address is listed as ‘notice@stonecraft.com’ and the sincerely block says that Bob Blah, the Security Administrator from StoneCraft Inc. is the one who sent the e-mail. If I did some background research I would discover that Bob Blah, in fact, is the listed security admin for the game. However, once I put my mouse pointer over the link, my email client informs me that the web address is not the same as the link text. If I had clicked that link, it would have taken me to a login page where I would enter my credentials:
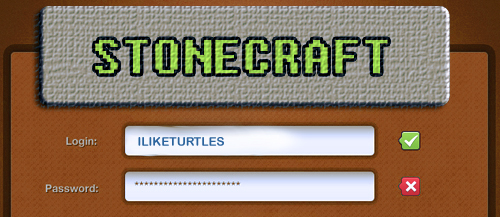
After which my credentials would be stolen and my account could be logged into by someone other than myself.
This is of course just an example of a Spear Phishing attack and many of them are not as harmless as this one, meaning that the information gathered is more than just the login credentials for an online game but credit card information, financial institution credentials or even the username and passwords for secure networks. Spear phishing is the first offensive step to obtaining restricted accesses and information.
Security Tip: While not always the most effective way of spotting a Phishing attempt, type the name of the sender into a search engine with the term “Phishing” after it and see if anything pops up, maybe someone else has already been hit by this and mentioned it on the internet.
Phishing in Messages / Social Networking
Phishing does not only refer to sending fake e-mails but also sending any kind of fake messages be it through Social Networking or through chat. The end goal is the same, using social engineering tactics to fool a user into clicking a link and giving up personal information.
Runescape Phishing
Runescape is a very popular online browser role playing video game; it appeals to a great number of gamers and has approximately 10 million active accounts per month. However, as with most popular things, there is always someone trying to exploit people for monetary gain. There is an underground market for people selling Runescape accounts or items and a commonly seen phishing attack revolves around stealing these things from legitimate users.
This is how the usual RuneScape phish happens:
- Hacker A decides to steal some accounts, so he sets up a fake RuneScape login page
- Hacker A goes onto RuneScape and begins announcing free items or assistance to anyone who asks
- User B decides to take Hacker A up on his offer and asks what he needs to do
- Hacker A directs User B to a login page by posting a URL into the chat
- User B navigates to this site where he is presented with a login page, he enters his credentials but nothing happens
- At the same time, the fake login page has transmitted User B’s login credentials to Hacker A who now has the ability to log-in, steal items from or sell User A’s account.
As with the other examples, here is a side-by-side of an official Runescape login page and a fake one obtained from PhishTank.com: 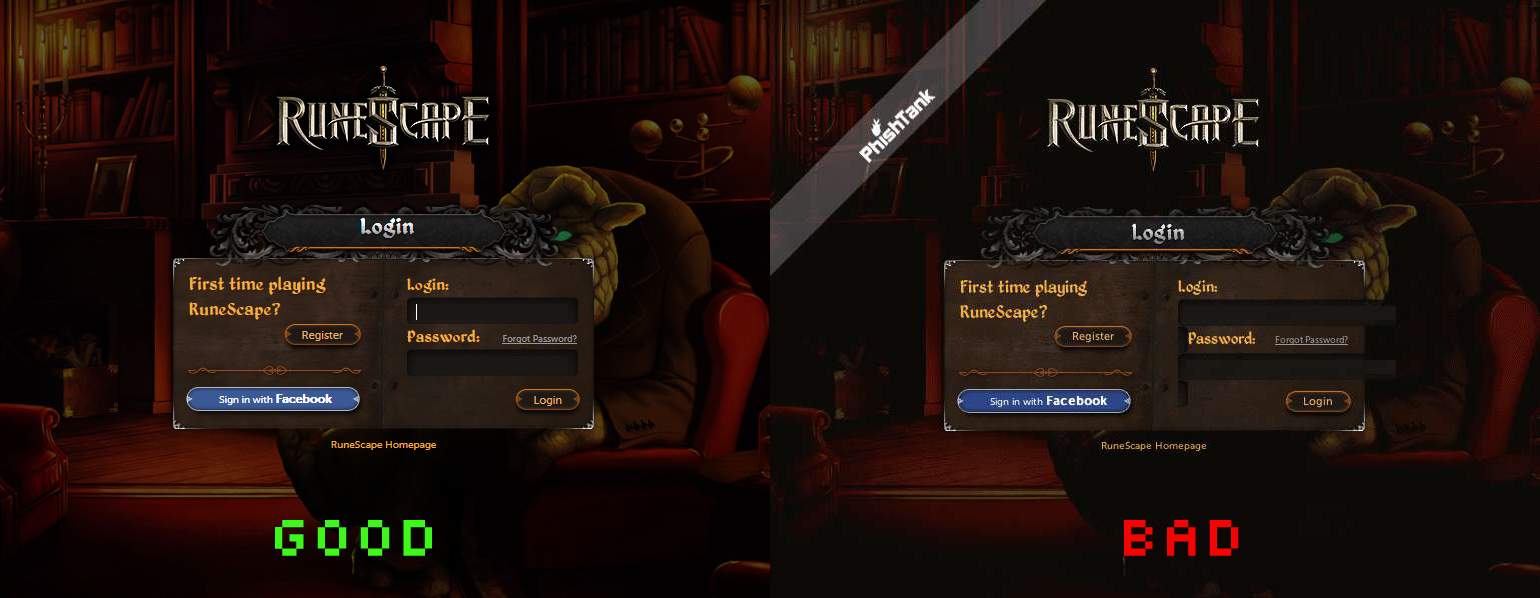
Runescape suffers from other types of phishing attacks as well, including through their Forum and of course through emails. For more information about Runescape phishing, check out their website:
http://services.runescape.com/m=rswiki/en/Phishing
Security Tip: If you come into contact with someone trying to give you a link through chat to a specific part of a legitimate website, ask them how to navigate to that section rather than clicking the link. That way you know that the page you end up on is legitimate.
Facebook Phishing
Facebook and other social networking sites are the perfect place for phishing attacks since they allow popular topics and posts to be spread to multiple users. Add this to the willingness of people to become friends with or subscribe to, random people based on how much they enjoy the persons post. The examples I will show you are of real world posts by fake users attempting to get two things:
- A broader base of users to spread their Spam or phishing attacks to
- People to click on their spam or phishing attacks
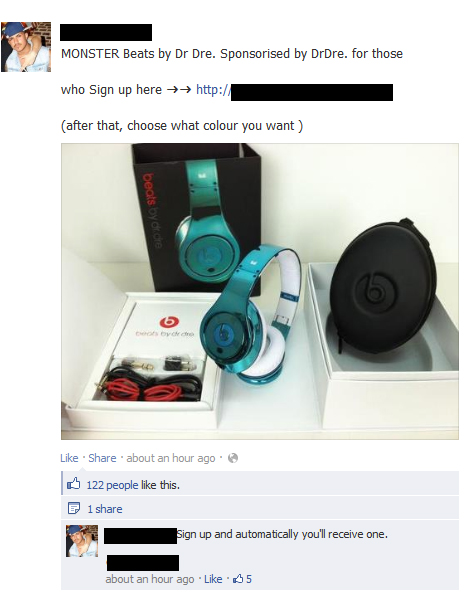
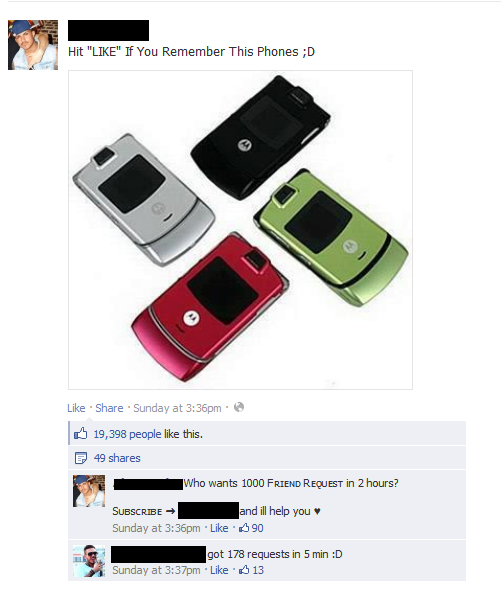
The first image shows a spam or phishing attempt which would lead users, under the guise of being given free merchandise, to a website to provide personal information. Once this information is stolen, it now belongs to the attacker. The second image shows the kind of tactics used by these attackers to spread their messages to a greater group of people by posting things like “Hit ‘Like’ if you remember This Phones ;D”. If you notice, at the time this screenshot was taken, the post had already received over 19k likes and been shared 50 times. In addition, the comments attached to this post advertise assistance in gaining more friend requests and even a fake account which backs up the previous comments assurances.
The above post, with all the likes it has received, would be reposted to the Facebook walls of thousands of users by popularity and sharing between friends. It would be so easy for one of these posts to lead users to a “Facebook Login” page where they would reveal their user login credentials and possibly other sensitive personal information.
Don’t think that Facebook is alone in this type of attack, any social networking forum has the same problems including Google+ and especially Twitter. Here is an example:
A new type of botnet emerges that has the capability to take over the Twitter account of the infected user. In doing so, it propagates by posting links to malicious web pages that download the same bot implant on other systems. Let’s say that the malware spreading web page only infects every 10th visitor with malware and does nothing for the rest, to avoid detection by malicious link detection services. The bot implant itself changes and morphs on a regular basis to avoid detection and eventually has infected 25,000 systems. At this point, a single post is made by one of the bots mentioning some interesting topic and linking to a site which uses the same method of user infection. All of the other 24,999 bots favorite or re-tweet this one post and it gets so much attention that legitimate users who did not detect any malicious intent begin to spread it as well. Soon enough you have a huge infection which spread from one single infected system.
Albeit this is a ‘worst-case scenario’ but the trusting nature of the average Facebook, Twitter or YouTube user makes it possible for cybercriminals to exploit them with a higher success rate than that of the traditional phishing attempts.
Security Tip: It’s fun to agree with things and show your approval for posts and comments but you can do your part to keep other users safe by not clicking’ Like’ or sharing the post of someone who you do not know or trust. Even if you are the only one who doesn’t share it, that could be thousands of potential victims you just saved.
How can you protect yourself?
To reinforce what I advised last week:
Phishing Attacks can fail by simply keeping an awareness of computer security practices in your mind whenever you check your email, read Facebook posts or play your favorite online game. Here is a list of a few of the most important tactics to keeping your information safe:
- Don’t open e-mails from senders you are not familiar with.
- Don’t ever click on a link inside of an e-mail unless you know exactly where it is going.
- To layer that protection, if you get an e-mail from a source you are unsure of, navigate to the provided link manually by entering the legitimate website address into your browser.
- Look out for the digital certificate of a website
- If you are asked to provide sensitive information, be sure to check and make sure that the URL of the page starts with ‘HTTPS’ instead of just ‘HTTP’
- This is important not only for securing yourself against phishing attacks but also, ‘HTTP’ can be intercepted by hackers watching your network connection.
- If you suspect the legitimacy of an e-mail, take some of its text or names used in it and type it into your search engine to see if any known phishing attacks exist using the same methods.
- Obtain ‘Password Manager’ tools which can auto-fill login information for you, if you navigate to a page which you had been to before, the fields should be filled in. If they are not, you may be on a phishing page.
Conclusion
This second part of the series went over the dangers of Spear Phishing and phishing in social media, while not seen as often as the classic phishing email method; it is none the less on the rise. However, most social networking sites are taking a proactive stance against these types of attacks by developing and implementing new types of security applications which stop malicious posts before they get out of control. Though, historically, as the technology becomes more secure and the normal methods of attack are phased out, new and more dangerous ones emerge and they always will. The best protection against becoming another victim of these types of attacks is to be suspicious of every post, tweet, video and link you come across and make sure you know with a high amount of certainty that you can trust the source.