We talked to Steven Burn (aka MysteryFCM), the lead of our Web Protection team and owner of hpHosts, and asked him about the strengths and possible improvements of the Malicious Website Protection module that comes with Malwarebytes Premium.
To start off, let us explain what the module does and how you can use it.
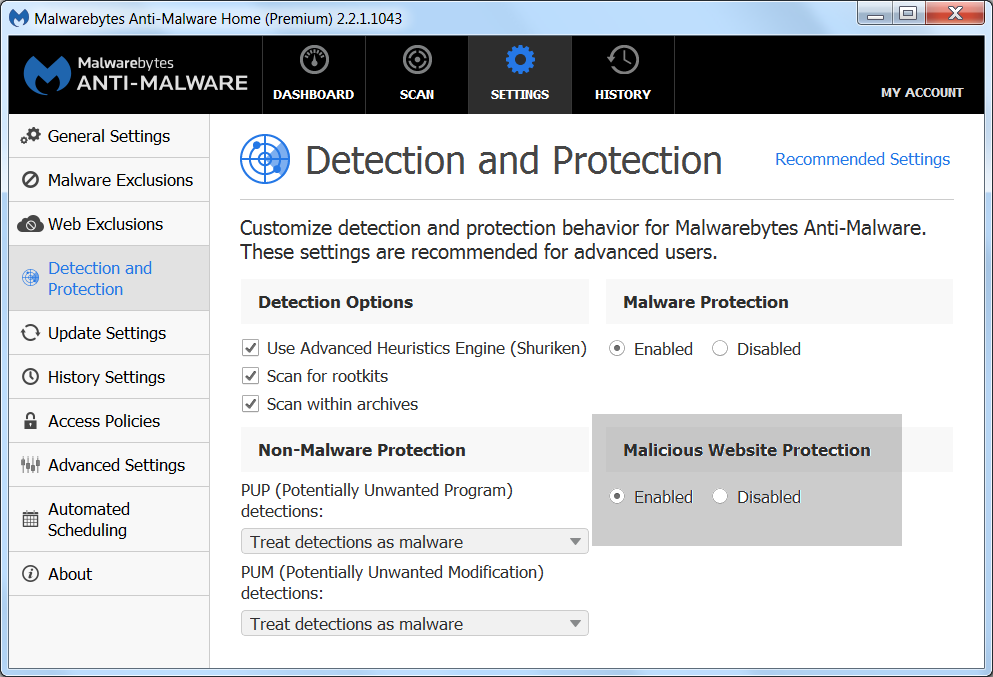
What does the Malicious Website Protection do?
The Malicious Website Protection module allows for the identification and subsequent blocking of both malicious domains and IPs by intercepting DNS queries made by everything from your browser and security/conference software to those lovely little “we’ll clean up your system, honest” pieces of up-to-no-good-software. Put simply, pretty much every application that pulls in data from the internet or something as simple as checking for updates to itself (e.g. the operating system itself).
Ordinarily, these would go from the application to your router and on to the ISP (or third party provider such as OpenDNS), depending of course, on your setup. In this case however, like a firewall, intercept these queries to identify malicious traffic that could harm your system or steal your data.
In layman terms, it blocks traffic to and from domains and IP addresses that we consider dangerous or extremely annoying. Reasons could be:
- hosting malware or PUPs
- Tech Support Scammers sites
- phishing scams
- other kinds of scams
- compromised sites
- fraud
- illegal pharma
How to use
In the highlighted area shown below, you can enable/disable Malicious Website Protection with the radio buttons.
Even if you are a careful surfer, when you are using the Malicious Website Protection, you may see this type of notification from time to time:
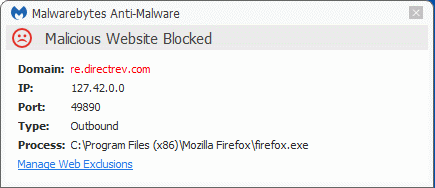
What do the items in such a notification mean?
Domain: if available, this shows the domain that was requested. If there is no domain mentioned, this usually means that the IP address was provided directly by the Process.IP: This is the IP address that the domain resolved to, and that is being blocked.
Port: This is the port on the system that was used for the contact.
Type: This shows the direction of the traffic.
Process: This is the executable (program) that tried to make the contact. If this is not a browser or another program that displays advertisements, e.g. Skype, this is potentially worrying, especially if you do not recognize the filename. You could be dealing with a Trojan or adware. If it is a browser, it is important to note whether the Domain is the site you wanted to visit or not. There could be a redirect or malicious element on the site you wanted to reach.
Manage Web Exclusions
If you are sure that the contacted domain is safe or you want to visit a site despite the warning, the exclusion option allows you to do that without having to disable the protection entirely.
In the notification you will see a link labeled Manage Web Exclusions. Clicking that link will take you to this screen—
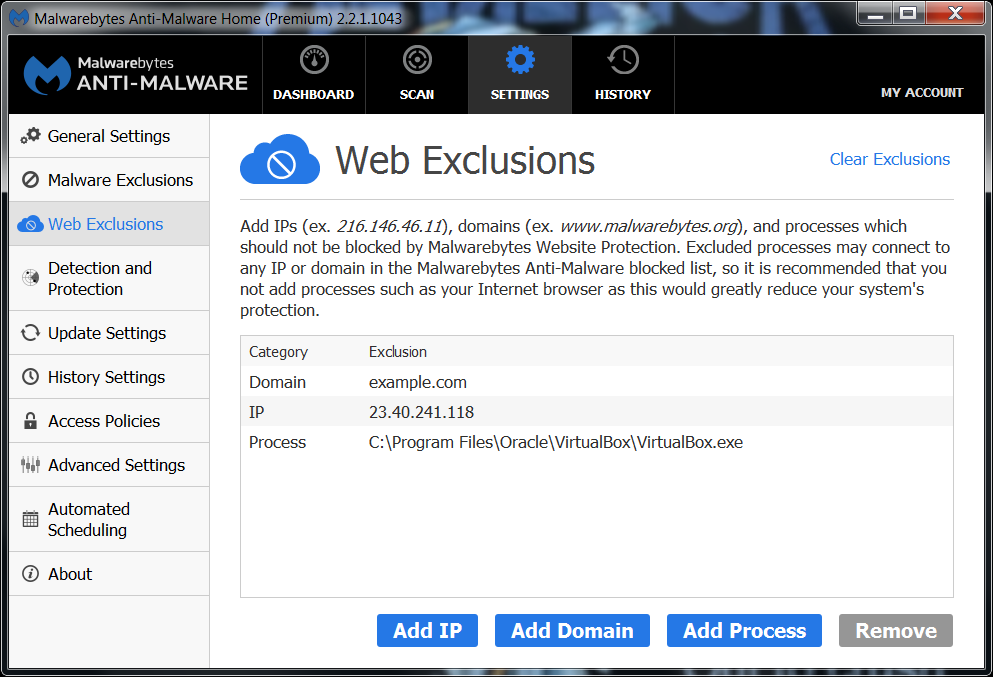
—which you can also reach by clicking Settings > Web Exclusions in the program.
The screen offers you 3 types of exclusions:
- by IP
- by Domain
- by Process
If you really feel you need to utilize this option we advise you to be as restrictive as possible. So, if that works, use the “Add Domain” before you use the “Add IP” and try to avoid giving a Process free play at all times, because some malware is capable of injecting malicious code into trusted processes.
Reasons why your browser could be causing alarms
If the Process is your browser, this does not necessarily mean that there is an infection. There could be something wrong with the site you are visiting or one of the advertisements it’s displaying. This happens to the most reputable sites sometimes. Only if you don’t have a browser window active and you still see blocks that tell you the browser process is responsible, there is reason for concern.
Questions for Steven Burn
Q: If someone notices that his site is blocked and he feels this is unjust, what is the best way to proceed?
Contact us, either via support, the forums or indeed, email – though checking their site/server first would be advised.
Author’s note: It is surprising how often people don’t realize that their site has been compromised or otherwise abused by threat actors.
Q: Is it true that some sites are impossible to block with the software as it now is? And are there any plans to change that?
This is indeed true. Some sites can’t easily be blocked without resulting in serious disruption of our customers visiting related, but not malicious, sites. In these cases (which are few) we work directly with both the offending site’s host and even law enforcement to get it taken down as quickly as possible.
Q: If I find them annoying, is there a way to turn off the notifications without disabling the protection?
Disabling notifications can be done under “General Settings,” but it’s not recommended.
Q: Is there a place online where I can find out why a certain Domain/IP is blocked?
hpHosts, VirusTotal, Scumware, abuse.ch, amongst a plethora of others. We don’t currently provide specifics via those we’ve got public (e.g. hpHosts) as these are held on internal only systems.
Pieter Arntz (Many thanks to Steven Burn for his input and help)











