Let’s face it. We live in a completely different security world from a decade ago and the kinds of threats we face have taken a new form. This time it’s ransomware. Over the course of just a few years, this threat has evolved from an annoying pop-up to a screen freezer that utilizes disturbing imagery to a sophisticated malicious program that encrypts important files.
New technologies are popping up all the time that combat the ransomware issue, however most (if not all) require active protection before you get infected. But what do you do if your company has already been infected? This article aims to help those who have been hit with encrypting ransomware and are faced with either paying or losing files.
Why is ransomware such a problem?
Ransomware has become a huge problem for businesses because it has been so widely adopted by the bad guys. Why? This is “Game Over” malware, meaning that, at least in the criminal’s eyes, once a user gets infected, there is no recovery option other than paying the ransom. Also, victims actually pay the ransom directly to the criminal, cutting out any need for middlemen or having to sell piles of stolen credit card information on darknet forums.
It works, it’s easy, cost-effective and profitable, which is essentially the driving force of new technology since the beginning of time.
It’s likely that the future of ransomware will include things like blackmail (threats to post trade secrets or company intel online or releasing customer information), more aggressive infection and AV evasion techniques, and better target identification—all techniques that we know how to combat. However, while the news of how to stop the malware is spreading, millions of people are still going to get infected because they didn’t get the memo soon enough.
Real world scenarios
It’s not difficult to wrap your brain around how ransomware could do serious damage to businesses. But how, exactly, do CISOs and other security executives deal with the infection and its aftermath? Let’s take a closer look at three different potential ransomware infection scenarios.
Let’s say there are three types of business leaders who deal with computer systems—whether that’s a small business owner or a high-level security official at an enterprise company. Each of these leaders have different opinions about computer security. They can be defined as follows:
- The prepared one
- The reactionary one
- The ignorant one
Now don’t get me wrong. I am not using ignorant as an insult, but rather a factual descriptor of someone who doesn’t know or understand cybersecurity. To be honest, some of the stuff in this industry is hard to wrap your brain around, especially for those who aren’t entrenched.
So our three leaders have different points of view when it comes to security and a little later, I am going to describe how each of these people actually deal with a ransomware infection. But first, how do these guys get infected and what kind of data are they going to lose?
Prepared
Our first leader, the prepared one, likes to think that she has done everything in her power to mitigate an attack. She keeps her system up-to-date, utilizes security software and provides employee training on how to avoid things like phishing attacks. Unfortunately, one of the employees visited a popular and well-respected website that was dealing with a malicious advertising attack. The attack launched a zero-day drive-by exploit on a work system. The exploit installed a brand-new family of ransomware, meaning that many types of security software would be unable to protect the system.
This method, while pretty unlikely, can circumvent many security solutions currently in place. And while it won’t take long for the security industry to start detecting and preventing this type of attack, our business leader has had her customer database encrypted by cybercriminals asking for lots of money.
Reactionary
Our next leader thinks that only gullible and ignorant people get infected with malware, and that by avoiding obvious bad places and deleting obvious phishing emails, he can protect his business from a threat. In some cases, he is right. Many threats can be avoided through user education; however, not all of them, and certainly not the ones that cause the most damage.
So without concern, the leader allows his employees to conduct work, check social media and install software on work computers. Then one day, an employee gets an invoice from a local vendor she uses, same as she does every month, but this time, the email address is spoofed and the invoice is actually a script which neuters any security software and downloads malware. Suddenly, that employee has been infected, and since security software has been disabled, all mapped drives get encrypted, basically stealing thousands of dollars of information in just a few minutes.
Ignorant
Our final leader just doesn’t know enough about computers. He has a few terminals set up in his shop, but they are all using either trial security software, or whatever was cheapest at the time. The leader hears about all of these cyberattacks on the news but has no idea how to protect his business. He shrugs it off as not that important—after all, the media does tend to exaggerate, right?
Well in some cases yes, but in others, they downplay a threat. Either way, the leader suffers from what is known as “security fatigue” or the lack of concern that arises after one is bombarded with news about breaches, malware, hackers and other cybersecurity issues. Once security fatigue sets in, the overwhelmed feelings turn to apathy. Our leader is avoiding learning more about protecting his business because he is “over it.”
Unfortunately for the leader, one of his employees downloaded a malicious torrent online, thinking it was a movie, and decided to watch it on a company system during his lunch break. Now, all of the networked systems in the shop are encrypted, but the most damaging is a folder that keeps all his business secrets, such as recipes for a secret sauce or blueprints.
Three disasters, three options
So our leaders are all infected with ransomware, each one having been hit in different ways and each losing various kinds of data. Now what are they going to do? While these three each have a different stance on how to deal with cybersecurity before the infection, they also have different methods for handling the aftermath of the attack. You can use these as well if you happen to find yourself in their shoes.
Option 1: Backups
Our prepared business leader had the foresight to keep regular backups of her customer database, which means that after infection, all she had to do was clean the systems using recently-updated security software and then restore the backup. Only a day’s worth of data was lost.
Now the thing to be concerned about when it comes to backups is your system accidentally identifying a change in a file and deciding “Hey, I need to upload this!” which in turn means that you are now polluting your backup with encrypted data. So make sure you keep some kind of file history enabled in your backup solution so you can revert to a previous backup if necessary. Also, utilize off-site and/or cloud backups rather than storing everything on a network drive, since many ransomware families are capable of reaching through mapped connections and connected drives to encrypt files outside of the victim HD.
If you have the forethought to properly utilize backups, bully for you! You are the ransomware authors’ worst nightmare. If everyone followed your example, ransomware would be dead by now.
Option 2: Decryption
Our second leader didn’t think he would ever be infected with ransomware because, in his words, “Only ignorant people get infected.” Joke’s on him: He got spear phished!
Now the reactive measure to most malware infections is basically downloading some kind of security software, running a scan and removing the threat. In many cases, this works because other forms of malware need to install, reach out to a remote server to get commands, and then exfiltrate data or launch a DDoS attack, which is a time-consuming process that you can stop by simply removing the malware.
Ransomware isn’t that nice. If you get hit once, your files are encrypted and there is nothing you can do about it—or so many people think. Thanks to the diligent efforts of our information security community, there are actually many decryptors available online. This software, when matched with the correct ransomware family, can decrypt files for free.
There is, however, a problem. Not all ransomware families have had decryptors created for them, and in many cases, people are unable to create decryptors because the ransomware is utilizing advanced and sophisticated encryption algorithms. Then, even if there is a decryptor, it’s not always clear if it’s for right version of the malware. You don’t want to further encrypt your files by using the wrong decryption script.
However, lots of security companies are coming together to create more decryptors, in fact one of those multi-group efforts is at NoMoreRansom.org. These efforts make it easier for folks infected with encrypting ransomware to get their files back without the need to pay. In many cases, you can identify and confirm the family of ransomware you are dealing with by looking closely at the ransom note.
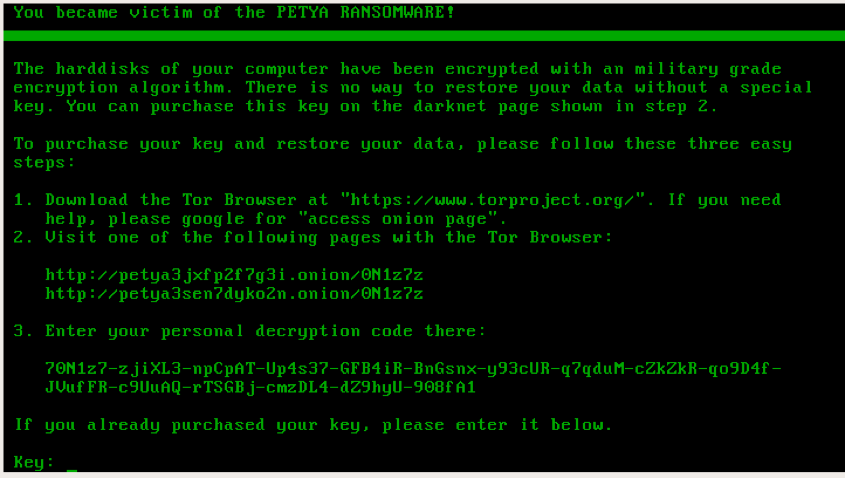
In the above example, you can see the ransom note actually tells you that it’s Petya ransomware. However, when the note doesn’t call attention to its ransomware family name, you can look at the extension name of your encrypted files.
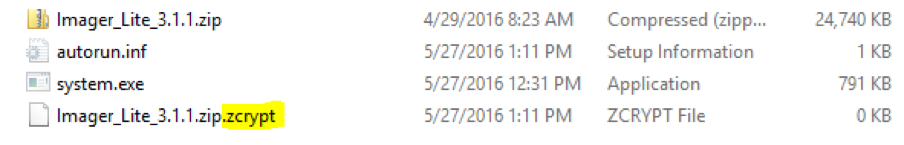
Notice in the below screenshot that an encrypted file has been renamed with the extension “.zcrypt” which is the name of this ransomware family.
If the ransom note doesn’t tell you its family name and there is no extension added to your encrypted files, then look for some unique value, string of words or numbers in the code that could be used, with the assistance of a search engine, to identify what you are dealing with.
EDIT: You could also skip all of this if you head over to ID Ransomware by the Malware Hunter Team and upload the ransom note or one of your encrypted files and it will tell you exactly what you are dealing with.
After that, you can either enter the name of the ransomware and ‘decryptor’ into a search engine and you should hopefully find some good results.
Option 3: Negotiate
Let’s say that you didn’t have the foresight or means to create regular backups of your data. Let’s also say that you have encountered a ransomware family that either doesn’t have a decryption algorithm available or you don’t have the technical means to utilize such a tool. If any of these are true, it’s likely you would be in the same boat as our third leader.
So in this case, rather than pay a king’s ransom to get all your files back, you can pay a smaller amount by identifying a particular system or set of files that you need more than others, then negotiating with the attacker using whatever e-mail address might be listed on the lock screen or, in some cases, the support page for the ransomware. At the end of the day, the bad guys just want to get paid, which means that historically they have been open to negotiating and returning a few files for a smaller amount of profit.
To be absolutely clear, I do not endorse or support paying cybercriminals the ransom. However, it has to be understood that for some folks, the loss of files would be far more damaging than just paying the ransom fee.
Conclusion
So there you have it, the three methods, outside of utilizing modern anti-ransomware security software to prevent infection, that can help you recover from a ransomware attack. They might not be absolute solutions, but anything is better than losing valuable data to cybercriminals. Maybe knowing how disappointing the recovery methods are for a ransomware attack will motivate some folks to actually use proactive protection and anti-ransomware technology, which remains the best option for fighting ransomware infection—not allowing the malware to encrypt your files in the first place.











