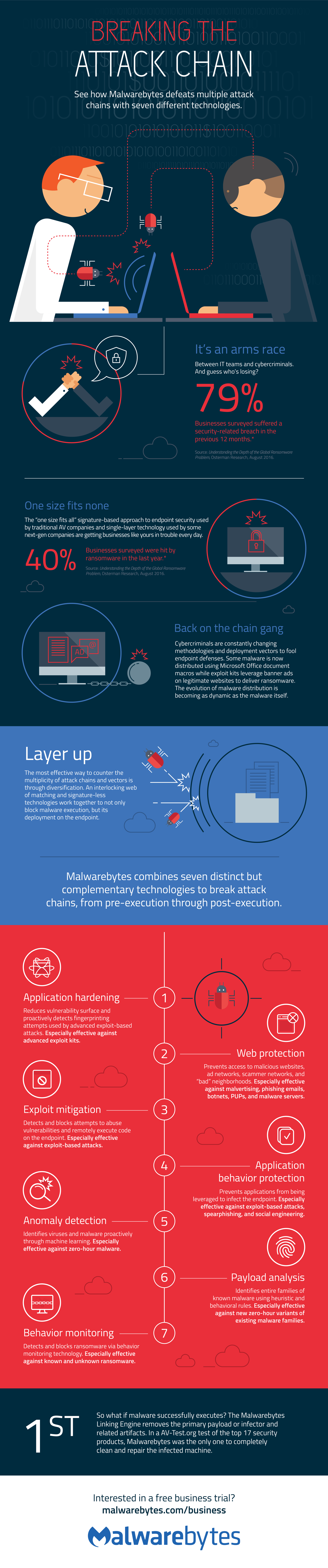
The attack chain. It’s a term used often in infosecurity. Also known as the kill chain, it was originally used as a military concept to describe the structure of an attack. It serves the same function in cybersecurity, where various methods of malware infiltration, deployment, and execution are outlined. To break the attack chain, then, means to preempt the attack.
This is of obvious significance to business owners, who’d much rather avoid expensive and time-sucking breach cleanups with programs that prevent attacks altogether. But breaking the attack chain is not as simple as it used to be.
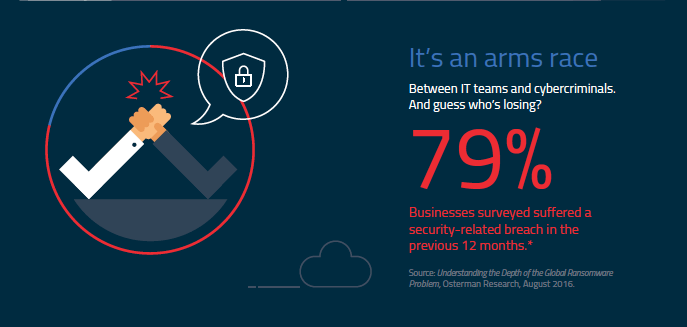
Cybercriminals are constantly changing methodologies and deployment vectors to fool endpoint defenses. The attack chain is evolving and multiplying, out-thinking traditional, signature-based endpoint security. In fact, nearly 80 percent of businesses have suffered a security-related breach in the last year.
That’s why businesses need to evolve their endpoint protection strategy, using a multi-layered approach to stop malware deployment and execution in multiple attack chains. In the following infographic, we’ve outline how Malwarebytes does just this, using seven different, complementary technologies.
Click here for the full PDF version.