Results for 'Teslacrypt'
Teslacrypt Spam Campaign: “Unpaid Issue…”
March 18, 2016 - We have all seen the current upsurge in Ransomware attacks. It has been covered on an international scale, with new variants...
Angler EK Drops TeslaCrypt Via Recent Flash Exploit
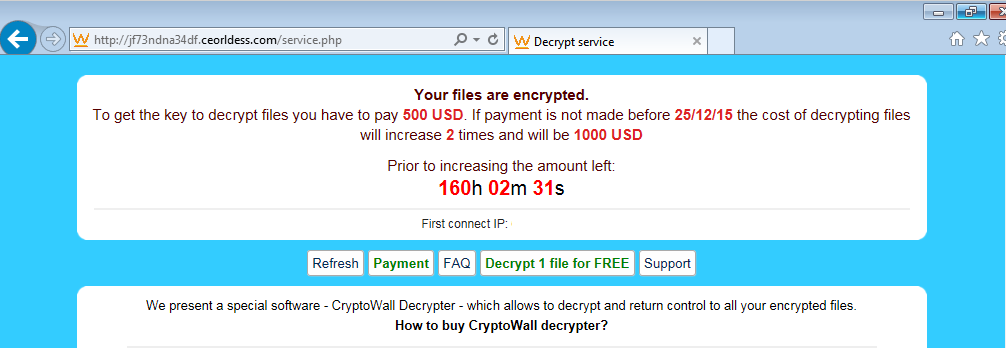
December 19, 2015 - On December 18, security company Fortinet blogged about a possible new variant of the CryptoWall ransomware distributed via spam. Around the same...
TeslaCrypt: Video game Safety 101
April 20, 2015 - TeslaCrypt is a piece of Ransomware which encrypts your data and locks it behind a “Pay up some serious cash or no...
Fonix ransomware gives up life of crime, apologizes
February 1, 2021 - Ransomware gangs deciding to pack their bags and leave their life of crime is not new, but it is a rare...
How gamers can protect against increasing cyberthreats
April 3, 2019 - A few years ago, cybersecurity scryers predicted that the video gaming industry would be the next big target of cybercriminals. Whether...
A state of constant uncertainty or uncertain constancy? Fast flux explained
December 12, 2017 - Last August, WireX made headlines. For one thing, it was dubbed the first-known DDoS botnet that used the Android platform. For...
The key to old Petya versions has been published by the malware author
July 6, 2017 - As research concluded, the original author of Petya, Janus, was not involved in the latest attacks on Ukraine. His original malware...
Malwarebytes Labs Presents: The Cybercrime Tactics and Techniques Report
March 6, 2017 - Last year was interesting for malware distribution and development. While we still experienced a flood of ransomware and immense distribution of...
A week in security (Nov 20 – Nov 26)
November 28, 2016 - Last week, we took a look at a ransomware called PrincessLocker, of which researcher Hasherezade created its decryptor. At the same...
From Locky with love – reading malicious attachments
July 27, 2016 - The common way of malware distribution, used i.e. by Locky ransomware are downloader scripts. They are spread in massive spam campaigns...