Back in May, we classified what we believed was just another generic Android/Trojan.Dropper, and moved on. We didn’t give this particular mobile malware much thought until months later, when we started noticing it had climbed onto our top 10 list of most detected mobile malware.
Henceforth, we feel a piece of mobile malware with such a high number of detections prompts a proper name and classification. Therefore, we now call it Android/Trojan.Dropper.xHelper. Furthermore, this prominent piece of malware deserves a closer look. Let’s discuss the finer points of this not-so-helpful xHelper.
Package name stealer
The first noticeable characteristic of xHelper is the use of stolen package names. It isn’t unusual for mobile malware to use the same package name of other legitimate apps. After all, the definition of a Trojan as it relates to mobile malware is pretending to be a legitimate app. However, the package names this Trojan has chosen is unusual.
To demonstrate, xHelper uses package names starting with “com.muf.” This package name is associated with a number of puzzle games found on Google Play, including a puzzle called New2048HD with the package name com.mufc.fireuvw. This simple game only had a little more than 10 installs at the time of this writing. Why this mobile malware is ripping off package names from such low-profile Android apps is a puzzle in itself. In contrast, most mobile Trojans rip off highly-popular package names.
Full-stealth vs semi-stealth
xHelper comes in two variants: full-stealth and semi-stealth. The semi-stealth version is a bit more intriguing, so we’ll start with this one. On install, the behavior is as follows:
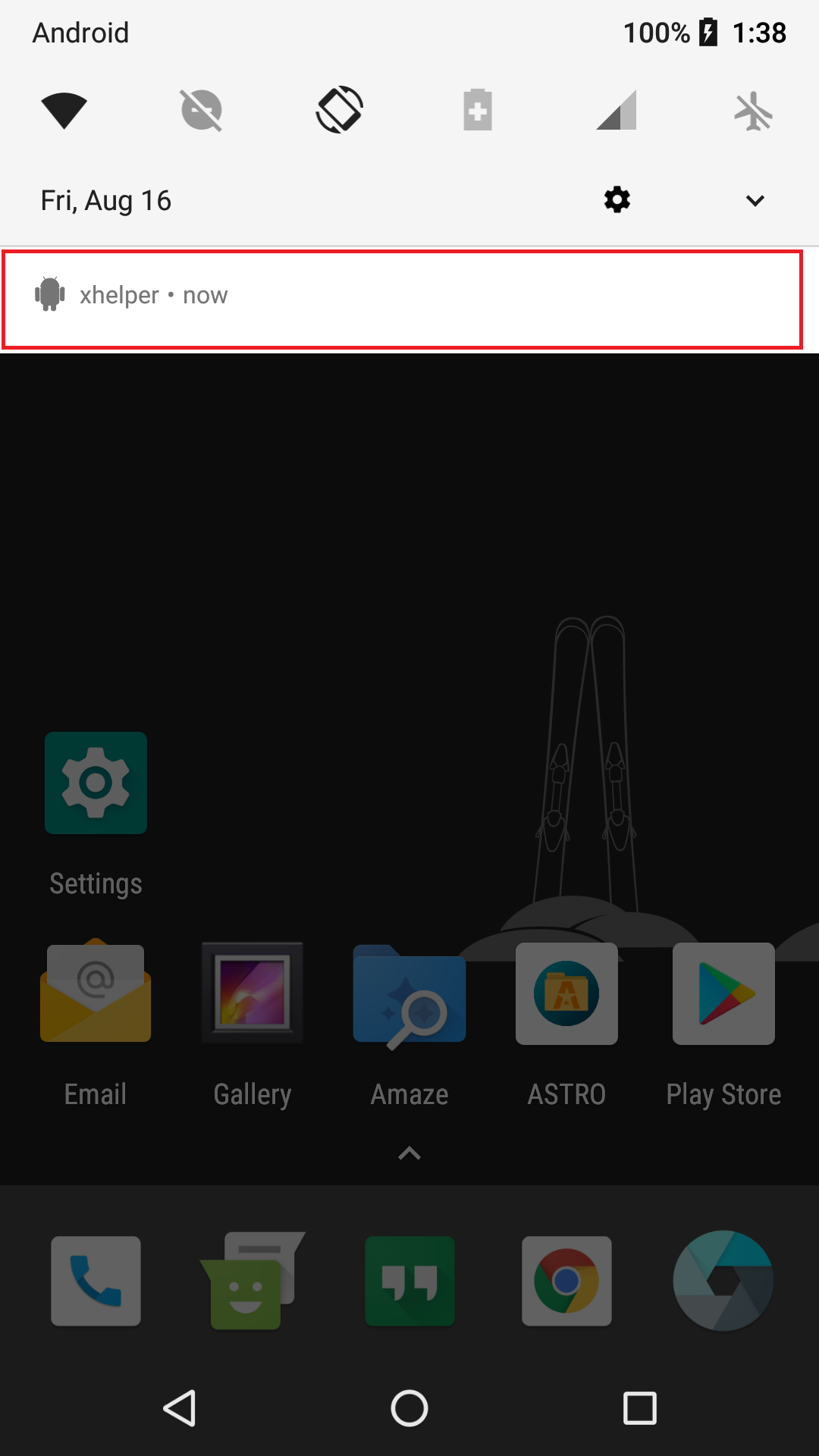
- Creates an icon in notifications titled “xhelper”
- Does not create an app icon or a shortcut icon
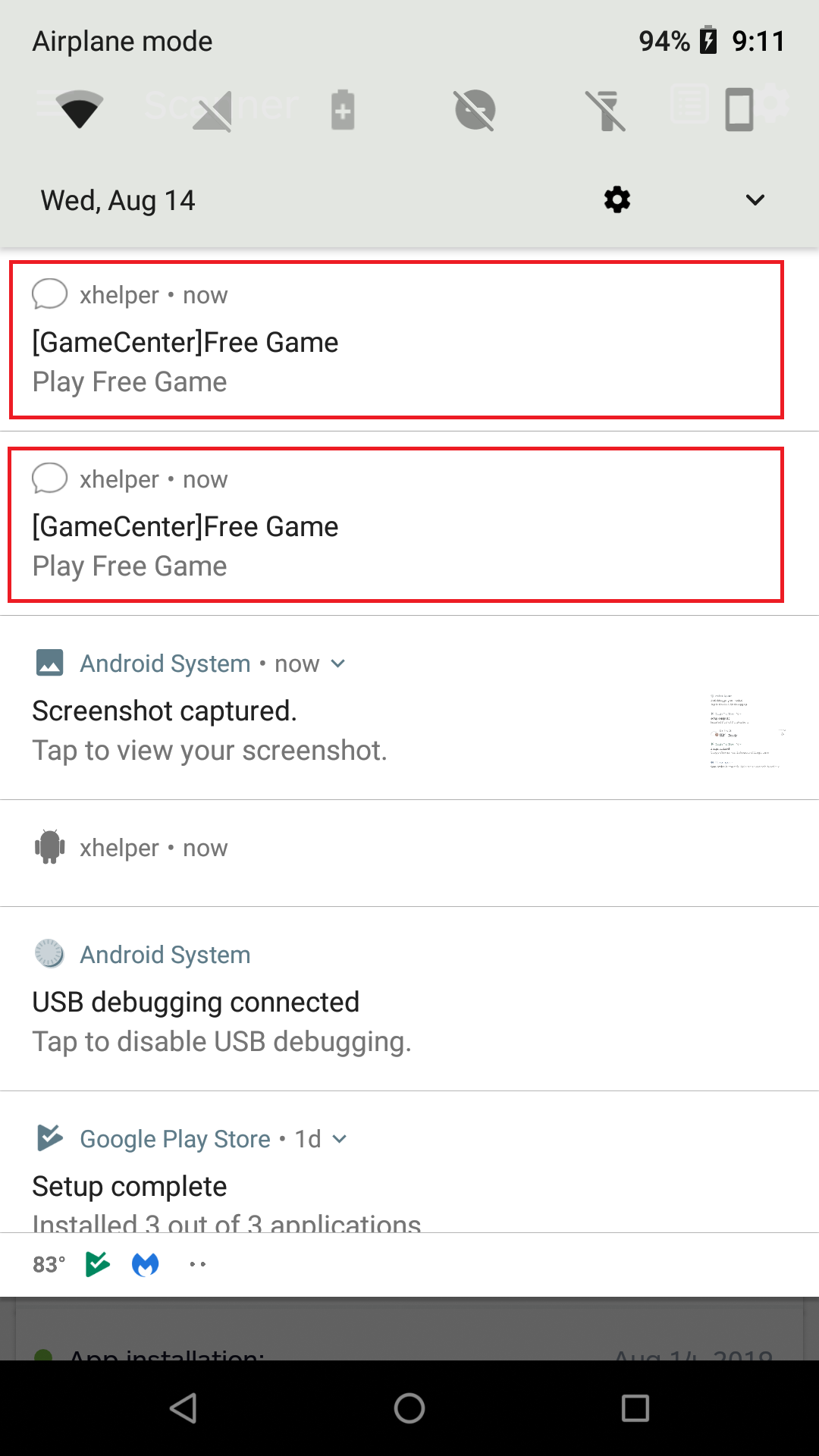
- After a couple of minutes, starts adding more icons to notifications: [GameCenter] Free Game
- Press on either of these notifications, and it directs you to a website that allows you to play games directly via browser.
- These websites seem harmless, but surely the malware authors are collecting pay-for-click profit on each redirect.
The full-stealth version also avoids creating an app icon or shortcut icon, but it hides almost all traces of its existence otherwise. There are no icons created in notifications. The only evidence of its presence is a simple xhelper listing in the app info section.
Digging deeper into the dropper
Mobile Trojan droppers typically contain an APK within the original app that is dropped, or installed, onto the mobile device. The most common place these additional APKs are stored is within the Assets Directory.
In this case, xHelper is not using an APK file stored in the Assets Directory. Instead, it’s a file that claims to be a JAR file, usually with the filename of xhelperdata.jar or firehelper.jar. However, try to open this JAR file in a Java decompiler/viewer, and you will receive an error.
The error is the result of two reasons: First, it’s actually a DEX file, which is a file that holds Android code unreadable to humans. To clarify, you would need to convert a DEX file to a JAR file to read it. Secondly, this file is encrypted.
Considering that the hidden file is encrypted, we assume that the first step xHelper takes upon opening is decryption. After decryption, it then uses an Android tool known as dex2oat that takes an APK file and generates compilation artifact files that the runtime loads. In other words, it loads or runs this hidden DEX file on the mobile device. This is clever workaround to simply installing another APK and obfuscates its true intentions.
What’s in a DEX
Every variant of xHelper uses this same method of disguising an encrypted file and loading it at runtime onto a mobile device. In order to further analyze xHelper, we needed to grab a decrypted version of the file caught during runtime. In this case, we were able to do so by running xHelper on a mobile device. Once it finished loading, it was easy to export the DEX file from storage.
However, even the decrypted version is an obfuscated tough nut to crack. In addition, each variant has slightly different code, making it difficult to pinpoint exactly what is the objective of the mobile malware.
Nevertheless, it’s my belief that its main function is to allow remote commands to be sent to the mobile device, aligning with its behavior of hiding in the background like a backdoor. Regardless of its true intentions, the clever attempt to obfuscate its dropper behavior is enough to classify this as a nasty threat.
High probability of infection
With xHelper being on our top 10 most detected list, there is a good chance Android users might come across it. Since we added the detection in mid-May 2019, it has been removed from nearly 33,000 mobile devices running Malwarebytes for Android. That number continues to rise by the hundreds daily.
The big question: What is the source of infection that is making this Trojan so prominent? Obviously this type of traffic wouldn’t come from carelessly installing third-party apps alone. Further analysis shows that xHelper is being hosted on IP addresses in the United States. One was found in New York City, New York; and another in Dallas, Texas. Therefore, it’s safe to say this is an attack targeting the United States.
We can, for the most part, conclude that this mobile infection is being spread by web redirects, perhaps via the game websites mentioned above, which are hosted in the US as well, or other shady websites.
If confirmed to be true, our theory highlights the need to be cautious of the mobile websites you visit. Also, if your web browser redirects you to another site, be extra cautious about click anything. In most cases, simply backing out of the website using the Android’s back key will keep you safe.
Stay safe out there!