UPDATE: July 31, 2020
Months after publishing this first investigation into government-funded mobile phones, we were contacted by a concerned user about their own device—the ANS UL40. After a thorough investigation, we yet again found pre-installed malware.
UPDATE: February 11, 2020
As of this writing, UMX (Unimax) Communications has officially removed all pre-installed malware from the UMX U683CL. The latest update to their software resolves issues.
Please keep in mind that if infected with Android/Trojan.HiddenAds.WRACT, you will still need to remove it— although Play Protect does offer a prompt calling it unsafe and warning users to uninstall.
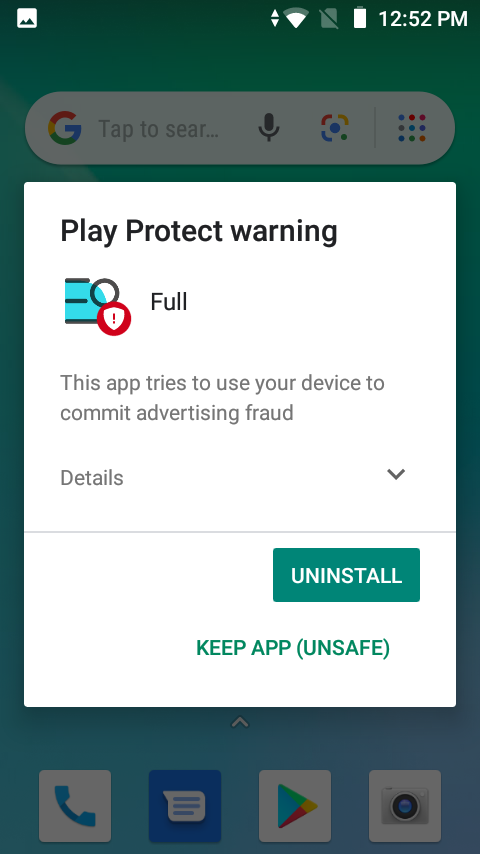
Malwarebytes for Android will also detect and remove HiddenAds.
We’d like to thank UMX (Unimax) Communications for resolving this issue, despite the fact they still refuse to take ownership. Back in January, UMX gave a public statement:
After investigating this issue, Unimax Communications has determined that the applications described in the posting are not malware…In reviewing these applications, however, Unimax Communications has determined that there may be a potential vulnerability in the Settings App library. Because of this, Unimax Communications has updated software to correct the potential vulnerability. To Unimax Communications’ knowledge, no customer data has been compromised.
How convenient that they happened to find “vulnerabilities” in the pre-installed Settings app that happened to be dropping malware. We stand by our original assertion that the app itself was malicious due its Trojan dropper capabilities—the dropping of the HiddenAds Trojan on the UMX device is indisputable.
The main goal of our post was to inform and protect users: both those who are Malwarebytes customers and those who are not. More importantly, we brought this issue to the press in order to invoke a resolution when there was no other option available to UMX customers. Therefore, although we’re glad Unimax took action so that our users and theirs could safely use their devices, we are disappointed that it took such public action to find a resolution in the first place.
UPDATE: January 10, 2020
At time of original publication, we were not yet able to replicate the malware Android./Trojan.HiddenAds being dropped on our test device, though multiple users had reported that a variant of HiddenAds suddenly installed on their UMX mobile phone.
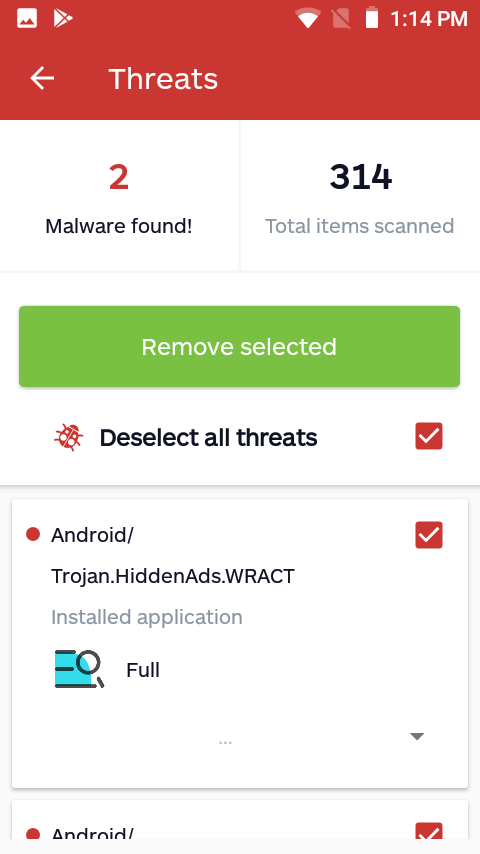
As of today, we are now able to report that our UMX U683CL test phone has become infected with a variant of HiddenAds we detect as Android/Trojan.HiddenAds.WRACT. This variant has been observed in the wild since spring 2019. It runs silently in the background and does not create an app icon. Evidence of its running in the background can be seen in the mobile device’s notifications. A notification box that changes its title name is highlighted below in red.
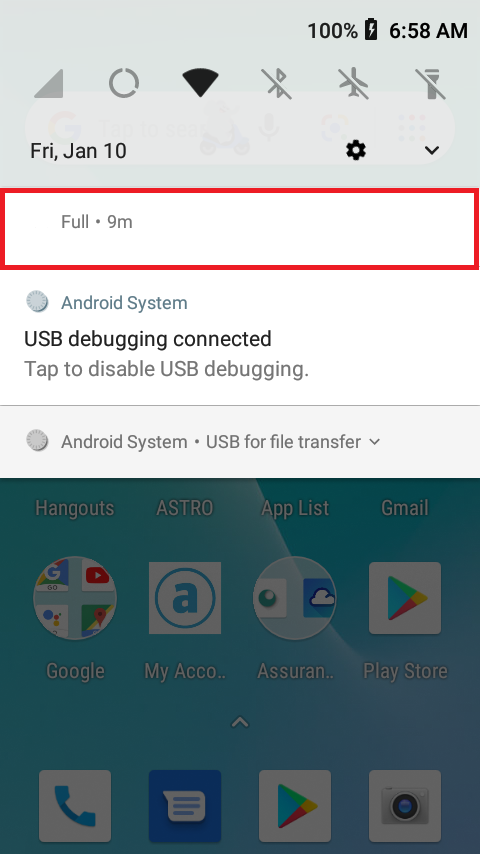
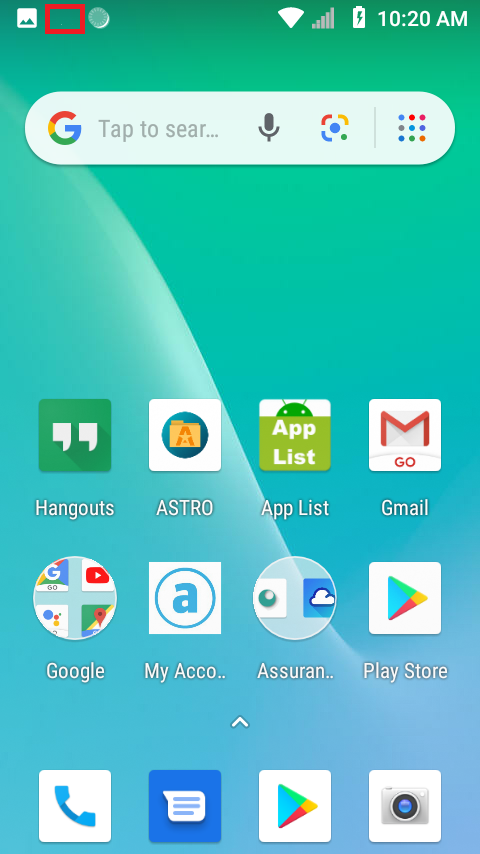
The notification bar cannot be swiped out in notifications. It stubbornly remains running in the background.
Fortunately, there is a way to find and uninstall this app. If you press and hold the notification, it will give the option to go to MORE SETTINGS.
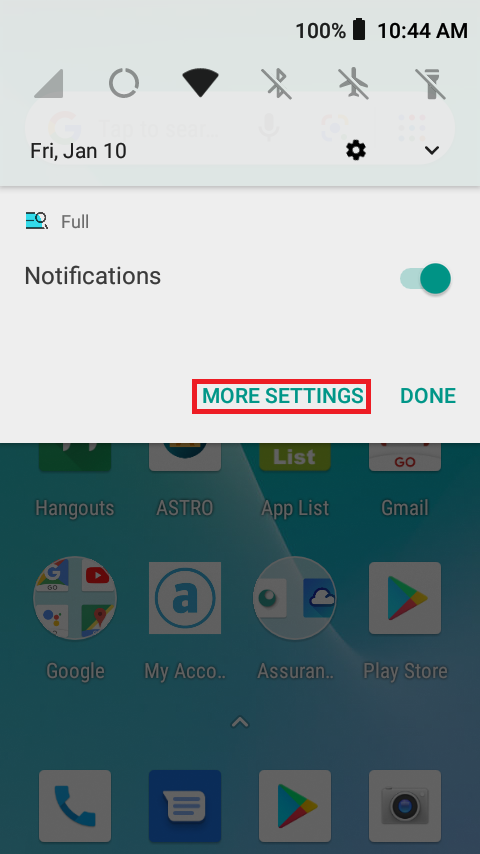
After clicking MORE SETTINGS, it will take you to the app’s notification settings. From there, press the app’s icon at the top.
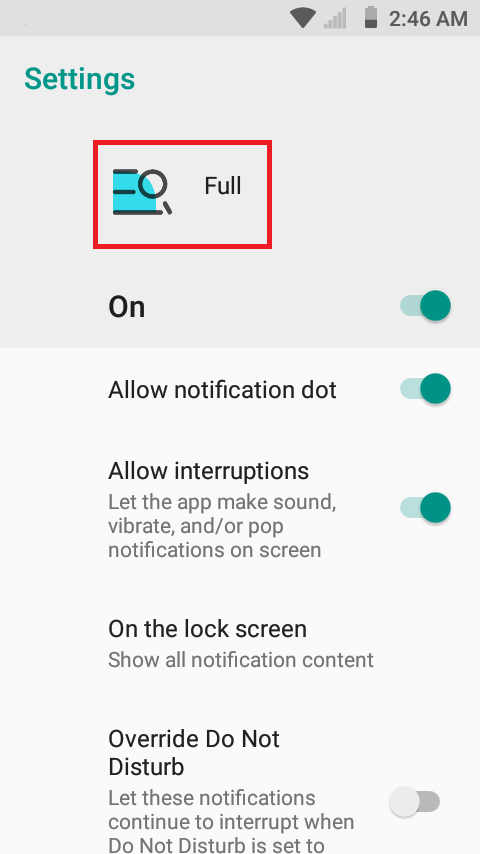
Lastly, it will take you to the app’s App info, where you can uninstall.
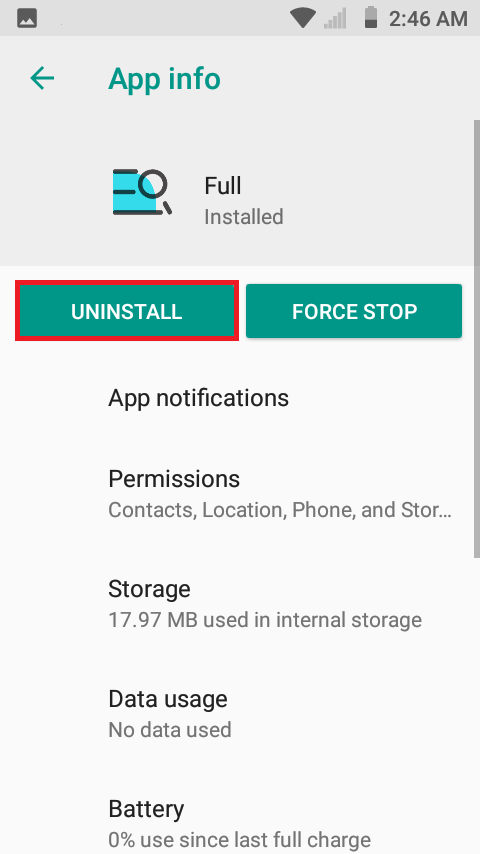
Of course, Malwarebytes for Android takes care of this as well.
************************************************************************
A United States–funded mobile carrier that offers phones via the Lifeline Assistance program is selling a mobile device pre-installed with not one, but two nefarious applications. Assurance Wireless by Virgin Mobile offers the UMX U683CL phone as their most budget conscious option. At only $35 under the government-funded program, it’s an attractive offering. However, what it comes installed with is appalling.
Not just malicious, but pre-installed
In October 2019, we saw several complaints in our support system from users with a government-issued phone reporting that some of its pre-installed apps were malicious. We purchased a UMX U683CL to better assist our customers and verify their claims.
We informed Assurance Wireless of our findings and asked them point blank why a US-funded mobile carrier is selling a mobile device infected with pre-installed malware? After giving them adequate time to respond, we unfortunately never heard back. Here’s what we discovered.
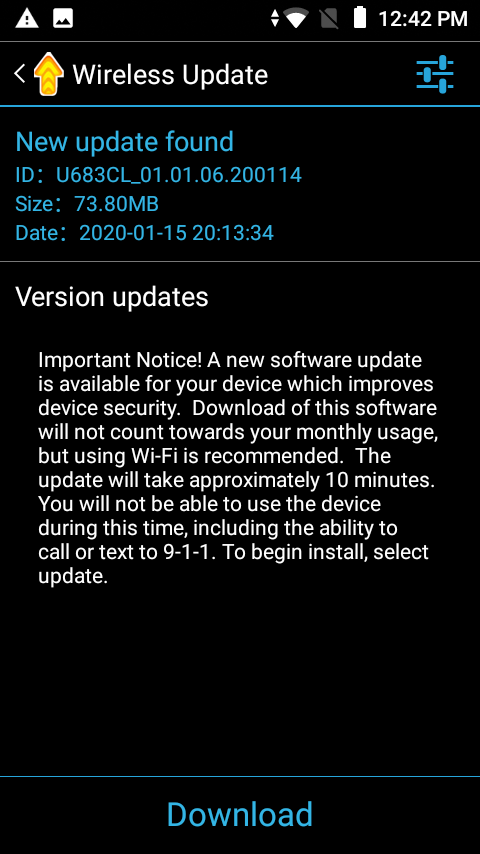
The first questionable app found on the UMX U683CL poses as an updater named Wireless Update. Yes, it is capable of updating the mobile device. In fact, it’s the only way to update the mobile device’s operating system (OS). Conversely, it is also capable of auto-installing apps without user consent.
Thus, we detect this app as Android/PUP.Riskware.Autoins.Fota.fbcvd, a detection name that should sound familiar to Malwarebytes for Android customers. That’s because the app is actually a variant of Adups, a China-based company caught collecting user data, creating backdoors for mobile devices and, yes, developing auto-installers.
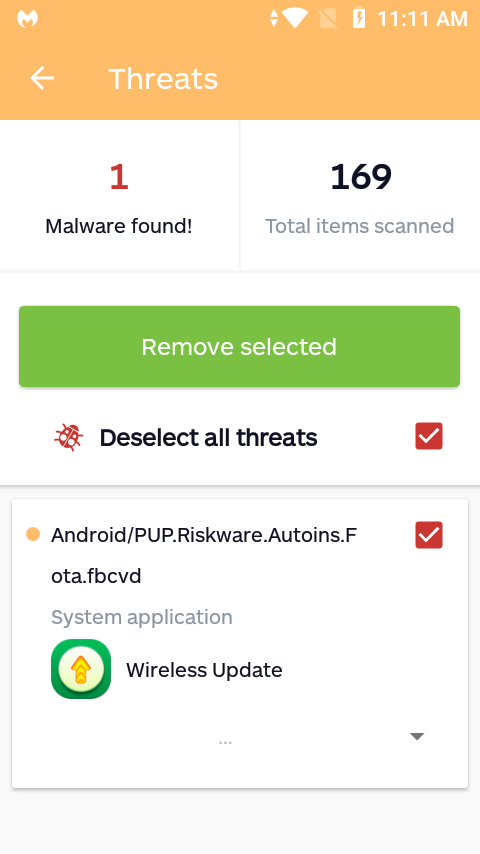
From the moment you log into the mobile device, Wireless Update starts auto-installing apps. To repeat: There is no user consent collected to do so, no buttons to click to accept the installs, it just installs apps on its own. While the apps it installs are initially clean and free of malware, it’s important to note that these apps are added to the device with zero notification or permission required from the user. This opens the potential for malware to unknowingly be installed in a future update to any of the apps added by Wireless Update at any time.
Not just pre-installed, but unremovable
It’s with great frustration that I must write about another unremovable pre-installed app found on the UMX U683CL phone: the mobile device’s own Settings app functions as a heavily-obfuscated malware we detect as Android/Trojan.Dropper.Agent.UMX. Because the app serves as the dashboard from which settings are changed, removing it would leave the device unusable.
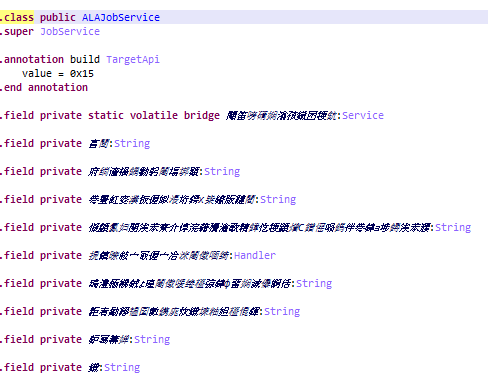
Android/Trojan.Dropper.Agent.UMX shares characteristics with two other variants of known mobile Trojan droppers. The first characteristic is that it uses the same receiver and service names. The receiver name ends with ALReceiver and the service name ends with ALAJobService. These names alone are too generic to make a solid correlation. But, coupled with the fact that the code is almost identical, and we can confidently confirm a match.
The only difference between the two codes are their variable names. The more discernible variant of this malware uses Chinese characters for variable names. Therefore, we can assume the origin of this malware is China.
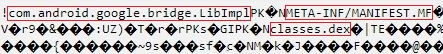
The second characteristic it shares is containing an encoded string within the code. Decoding this string reveals a hidden library file named com.android.google.bridge.LibImp.
Let’s take some time to look at how the code flows while decoding com.android.google.bridge.LibImp. It first grabs the encoded string and decodes using Base64 decoding.
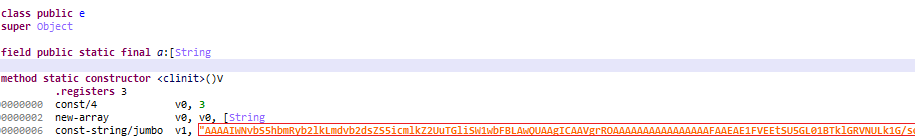
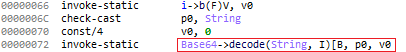
It then loads the decoded library into memory using DexClassLoader.
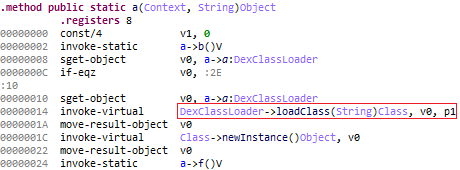
After the library is loaded into memory, it then drops another piece of malware known as Android/Trojan.HiddenAds.
Although we have yet to reproduce the dropping of additional malware ourselves, our users have reported that indeed a variant of HiddenAds suddenly installs on their UMX mobile device.
The malware origin
In addition to the malware being of Chinese origin, it’s noteworthy to mention that this UMX mobile device is made by a Chinese company as well. This could simply be a coincidence rather than explicit malcontent—we cannot confirm if the makers of the device are aware there is Chinese malware pre-installed.

No current resolution
Although we do have a way to uninstall pre-installed apps for current Malwarebytes users, doing so on the UMX has consequences. Uninstall Wireless Update, and you could be missing out on critical updates for the OS. We think that’s worth the tradeoff, and suggest doing so.
But uninstall the Settings app, and you just made yourself a pricey paper weight. We do offer an attempt to remediate such pre-installed malware in our blog: The new landscape of pre-installed mobile malware: malicious code within. See section: Attempting to remediate.
Pre-installed malware getting worse, as foreshadowed
As I have highlighted in this blog and blogs past, pre-installed malware continues to be a scourge for users of mobile devices. But now that there’s a mobile device available for purchase through a US government-funded program, this henceforth raises (or lowers, however you view it) the bar on bad behavior by app development companies.
Budget should not dictate whether a user can remain safe on his or her mobile device. Shell out thousands for an iPhone, and escape pre-installed maliciousness. But use government-assisted funding to purchase a device and pay the price in malware? That’s not the type of malware-free existence we envision at Malwarebytes.
Final words on UMX U683CL
Having an actual UMX U683CL in my hands, I can tell you it is not a bad phone. It feels solid in hand and runs smoothly. Sure, it’s not the fastest mobile device, but it’s a fully capable smart phone. In general, without the malware, this device is a good option for anyone on a budget.
It’s important to realize that UMX isn’t alone. There are many reports of budget manufactures coming pre-installed with malware, and these reports are increasing in number. Although I don’t have the answer to this widespread issue, I can say that US citizens using the Lifeline Assistance Program and many others on a tight budget deserve more. Stay safe out there.
Correction: An earlier version of this blog listed the UMX model as U686CL. The correct model is UMX U683CL. We apologize for the confusion.










