The latest data breach at Capital One is a noteworthy incident not because it affected over 100 million customer records, 140,000 Social Security numbers (SSNs), and 80,000 linked bank accounts. Nor was it special because the hack was the result of a vulnerable firewall misconfiguration.
Many still talk about this breach because a leak of this magnitude, which we’ve historically seen conducted by nation-state actors, was made possible by a single skilled insider: Paige A. Thompson. Thompson set a benchmark for single insider threat attacks against the banking industry—and we can expect that benchmark to be cleared.
On a more chilling note, criminal enterprises already have a market opened for corporate employees willing to trade proprietary secrets for cash as a form of “side job.” A number of these underground organizations, unsurprisingly, hail from countries outside the United States, such as Russia and China. Unfortunately for US organizations, these criminal enterprises pay really well.
Recently, Cybersecurity Insiders—in partnership with Gurucul, a behavior, identity, fraud, and cloud security analytics company—released results of its research on insider threats, revealing the latest trends, organizational challenges, and methodologies on how IT professionals prepare for and deal with this danger. Here are some of their key findings:
- More than half of organizations surveyed (58 percent) said that they are not effective at monitoring, detecting, and responding to insider threats.
- 63 percent of organizations think that privileged IT users pose the biggest security risk. This is followed by regular employees (51 percent), contractors/service providers/temporary workers (50 percent), and other privileged users, such as executives (50 percent).
- 68 percent of organizations feel that they are moderately to extremely vulnerable to insider threats.
- 52 percent of organizations confirm that it is more difficult for them to detect and prevent insider threats than detecting and preventing external cyberattacks.
- 68 percent of organizations have observed that insider threats have become more frequent in the past 12 months.
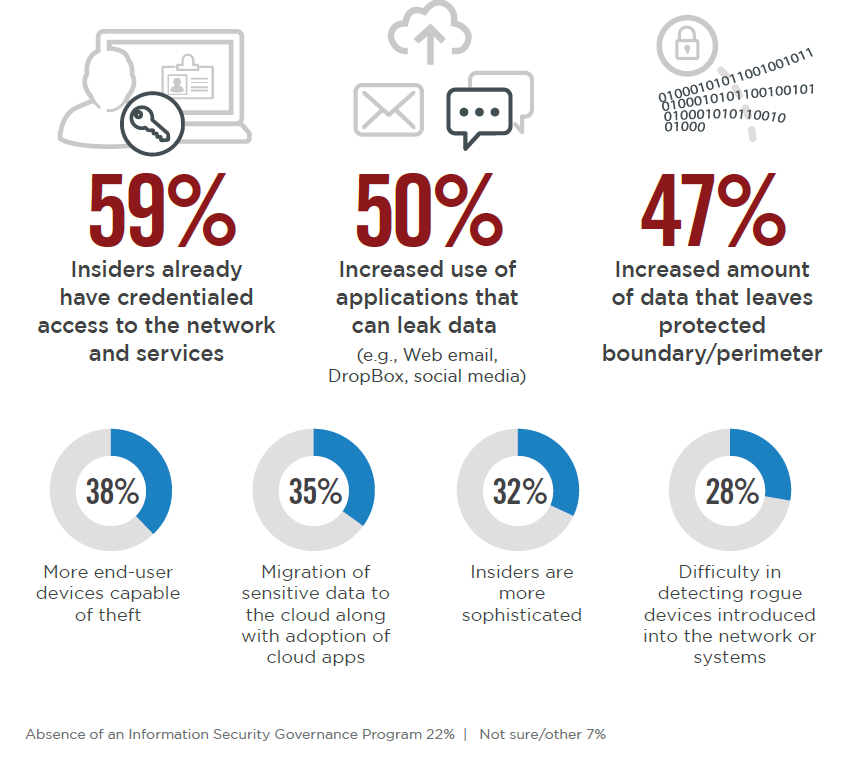
The report also states reasons why organizations are increasingly having difficulty detecting and preventing insider threats, which include the increased use of applications and/or tools that leak data, an increased amount of data that leaves the business environment/perimeter, and the misuse of credential or access privileges.
The CERT Insider Threat Center, part of the CERT Division at Carnegie Mellon’s Software Engineering Institute (SEI) that specializes in insider threats, has recently put forth a blog series that ran from October 2018 to August 2019 on the patterns and trends of insider threats. These posts contained breakdowns and analyses of what insider threats look like across certain industry sectors, statistics, and motivations behind insider incidents—and they’re quite different.
Below are a few high-level takeaways from these posts:
- The CERT Insider Threat Center has identified the top three crimes insiders commit across industries: fraud, intellectual property theft, and IT systems sabotage.
- Fraud is the most common insider threat incident recorded in the federal government (60.8 percent), finance and insurance (87.8 percent), state and local governments (77 percent), healthcare (76 percent), and the entertainment (61.5 percent) industries.
- All sectors consistently experienced an insider incident perpetrated by trusted business partners. Typically, it ranges between 15 to 25 percent across all insider incident types and sectors. This should be an eye-opening statistic, especially for SMBs, as research suggests that they partner more with other businesses over hiring employees.

Insider threats on the spotlight—finally!
The National Counterintelligence and Security Center (NCSC) and the National Insider Threat Task Force (NITTF), together with the Federal Bureau of Investigation, the Office of the Under Secretary of Defense (Intelligence), the Department of Homeland Security, and the Defense Counterintelligence and Security Agency declared September as National Insider Threat Awareness Month, and it launched this year.
The goal of the annual campaign is to educate employees about insider threats and to maximize the reporting of abnormal employee behavior before things escalate to an insider incident.
“All organizations are vulnerable to insider threats from employees who may use their authorized access to facilities, personnel or information to harm their organizations—intentionally or unintentionally,” says NCSC Director William Evanina in a press release [PDF], “The harm can range from negligence, such as failing to secure data or clicking on a spear-phishing link, to malicious activities like theft, sabotage, espionage, unauthorized disclosure of classified information or even violence.”
We have tackled insider threats at length on several occasions on the Malwarebytes Labs blog. Now is always the right time for organizations to give this cybersecurity threat some serious thought and plan on how they can combat it. After all, if businesses are only concerned about attacks from the outside, at some point they’ll be hit with attacks from the inside. The good news is organizations won’t have to wait for next September to start dealing with this problem today.
The CERT Insider Threat Center offers a list of common-sense recommendations for mitigating insider threats that every cybersecurity, managerial, legal, and human resource personnel should have on hand. The Center also showcases a trove of publications if organizations would like to go deeper.
We’d also like to add our own blog on the various types of insiders your organization may encounter and certain steps you can take to nipping insider risks in the bud. We also paid closer attention to workplace violence, a type of insider threat that is often forgotten.
Stay safe! And remember: When you see something, say something.










