Airdrop phishing is a really popular tactic at the moment. It emerged alongside the explosion of Web3/NFT/cryptocurrency popularity, and ensures scammers get a slice of the money pie. You may well have heard the term in passing, and wondered what an Airdrop is. Is your iPhone about to be Airdrop phished?
It doesn’t really help that the term tied up into lots of new forms of tech you might never have experienced directly. It’s one of those odd scams, doing weird things, to accounts you have no idea about.
Fret no more, because we’re going to walk you through an actual Airdrop phish example. No apes were harmed in the making of this documentary.
What is an Airdrop?
Confusingly, the term has multiple uses jostling for attention. The older, more familiar term is the one related to Apple devices. An Apple Airdrop is where Bluetooth is used to send filesto other people. If you’re not an Apple user, it’s likely you’ve only ever seen Airdrop in relation to trolling. If you’re out and about, you may walk into an unintended crossfire of memes, and in the worst case scenario, it might be objectionable unsolicited images.
In terms of security concerns specifically, research has shown how it could potentially aid spear phishingin the right circumstances. Crucially, none of these things are related to the Airdrops we’re talking about today.
What type of Airdrop are we talking about?
The Airdrops of the moment are promotional tactics aimed at cryptocurrency/Web3 people. Airdrops typically reward early adopters of certain currencies or communities. This type of reward can also be given out as no strings attached freebies to anyone who wants in on the action, and they’re great ways to keep people emotionally invested in their Web3 activities. There’s a lot of real world examples listed here.
In terms of how you receivethe Airdrop, there are a few different ways. Those early adopters may find the free Airdrop distributed to their address automatically, assuming they have some level of investment in the service giving it away. A big red flag is when a supposed Airdrop asks for funds (for a freebie?), or even worse, your login/recovery phrase.
Nobody should everbe asking for that.
Airdrops are very popular, and this is where phishing attacks come in.
Common Airdrop phishing tactics
Airdrop phish pages try to ensnare as many cryptocurrency users as possible. No matter how obscure your digital currency of choice is, or how unusual your wallet is, there’s a scam just waiting for you.
Our bogus site below is quite slick looking, complete with ticker at the top. “Claim reward bonus/Airdrop”, they implore.
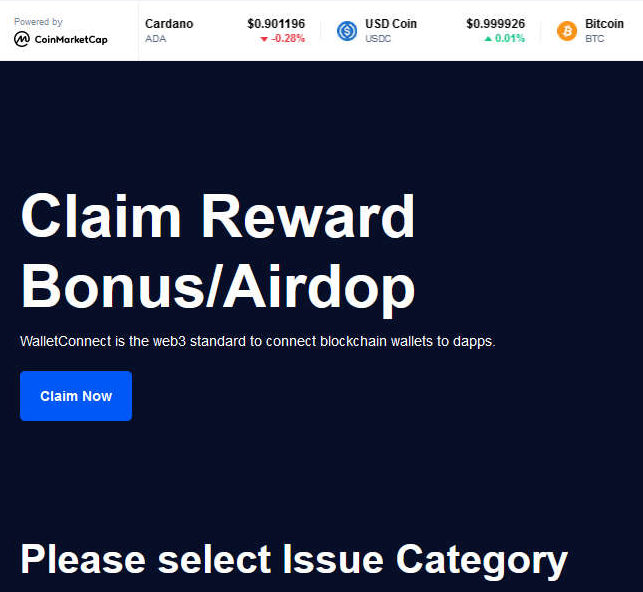
Hitting the button takes you to the select a wallet page. There is, quite simply, a ridiculous amount of wallets and services listed. MetaMask, Solflare, Binance, Digitex, Argent, the works. If you use any form of cryptocurrency wallet or service, there’s a good chance it’s on the list somewhere.

Clicking any of the wallets results in you being informed that an error has occurred. Connecting manually is what you’re now asked to do. From here, you’re asked to send them your phrase, private key, or keystore.
Hitting connect pauses the site for a second, then dumps you onto a 404 Page not found containing “sent” in the URL. At this point, it’s probably a good idea to hope the 404 is genuine and nothing has been sent to the scammers.
Some sites target users of one wallet only. Here’s one targeting MetaMask users, asking for their recovery phrase:
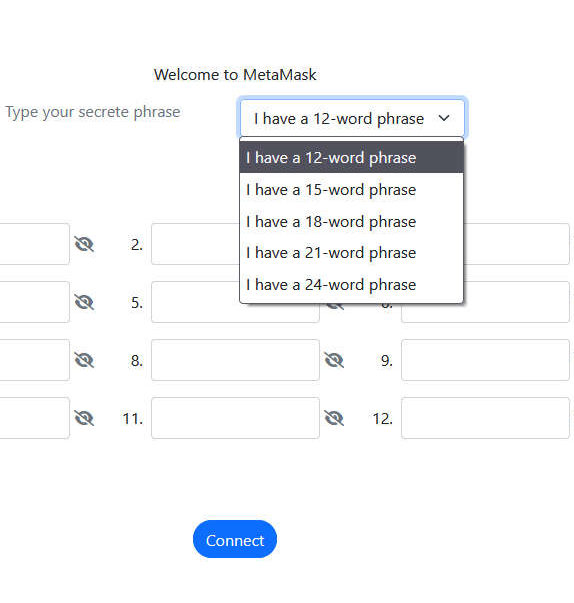
As MetaMask’s official support says:
The ape themed Airdrop phish
Apes are, of course, the hottest draw in town where Airdrop phishing is concerned. Just recently, close to $3m worth of Ape NFTs were stolen via an Instagram compromise. Anything ape related is a giant dollar sign in the sky for fraudsters, and the variety of fake pages out there reflects this.
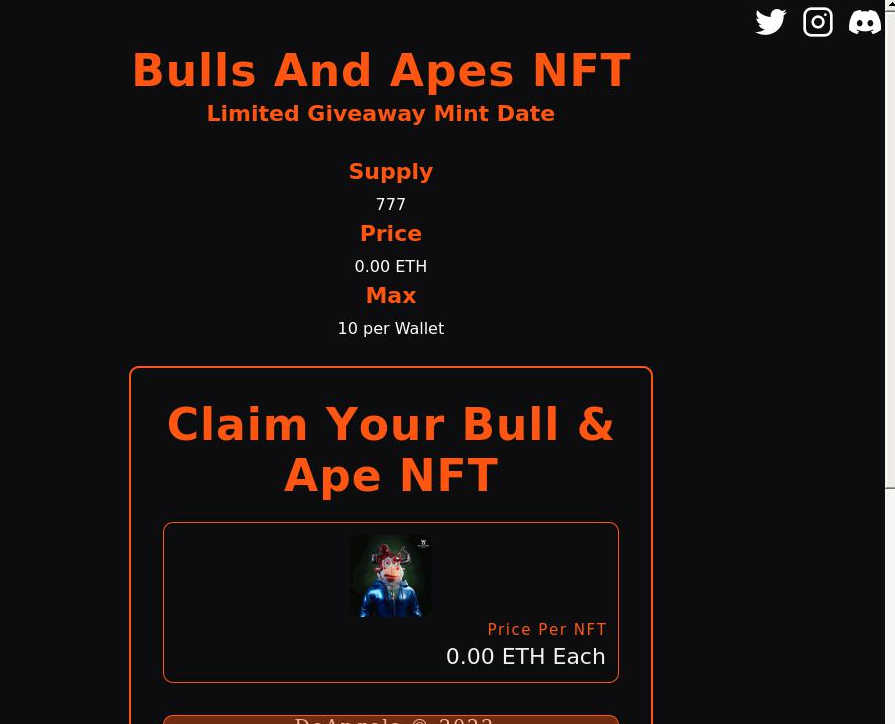
This particular site asked visitors to claim up to 10 Bull & Ape NFTs, then asked for a variety of password/recovery phrases. The supposed T&C page leads to a 404, and the cookies and privacy policy pages go to pages from an unrelated wallet app. Does this reallysound like something you want to hand over your recovery phrase to?
The “Connect your wallet” Airdrop phish
This is where a scam site checks to see if you have a wallet installed, and if not, tells you to install one and then connect it to the site.
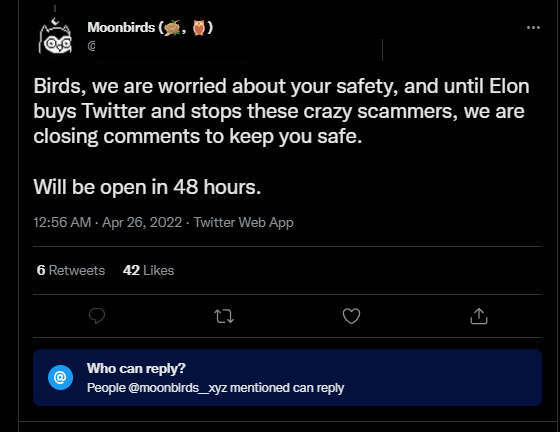
Here’s an account with 60k followers, claiming to be the Moonbirds project offering up an NFT airdrop:

When people started calling out the tweet, they locked people’s ability to reply under the guise of “safety” so nobody else could highlight the scam.
This is the genuine Moonbirds account. Note the verified status, which the imposter lacks:
Below, you can see my already installed MetaMask extension opening in the top right corner when I click the “Connect Wallet” button on the fake Airdrop page.
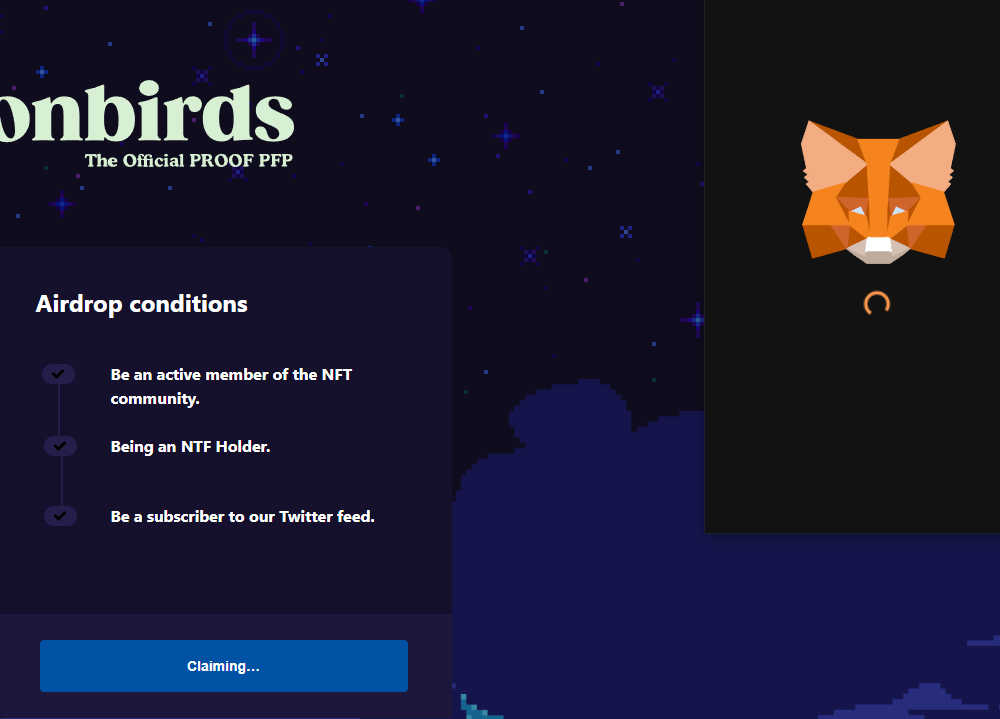
Connecting your wallet to Decentralised Applications (Dapps) is common. What you need to be careful of is connecting to rogue sites. If you start granting permissions, or signing transactions, you may find your wallet draining of funds. It’s up to you to ensure that you don’t simply say “yes” to everything a site asks you. From the MetaMask FAQ:
Be careful about which Dapps you connect to, and what permissions you give them.
Certain types of transaction require granting a Dapp permission to access your funds–infinite amounts of your funds.
In fact, there have been cases of Dapps being created specifically with the intent to defraud users and steal all of their funds once they’ve granted this kind of access.
Where Airdrops are concerned: safety first, every single time
Nobody needs the stress of losing all their digital currency because of phishing, no matter which form it arrives in. Whether it’s websites asking for recovery phrases or Dapp style sites connecting wallets, be very careful what you do with your wallet. You almost certainly won’t get a second chance if things go wrong.










