Thanks to a tip from a friend, we came across a fake online scanner that abuses the good name of Avast.
The idea to get you to visit this site is by waiting for someone to make a typo and end up at facebooksecuryti(dot)com.
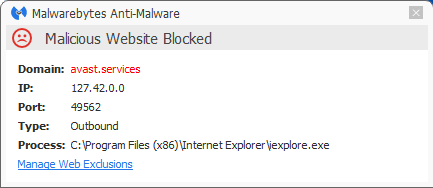
The site shows a picture of a pornographic nature just long enough to redirect you to the fake online scanner at avast(dot)services.
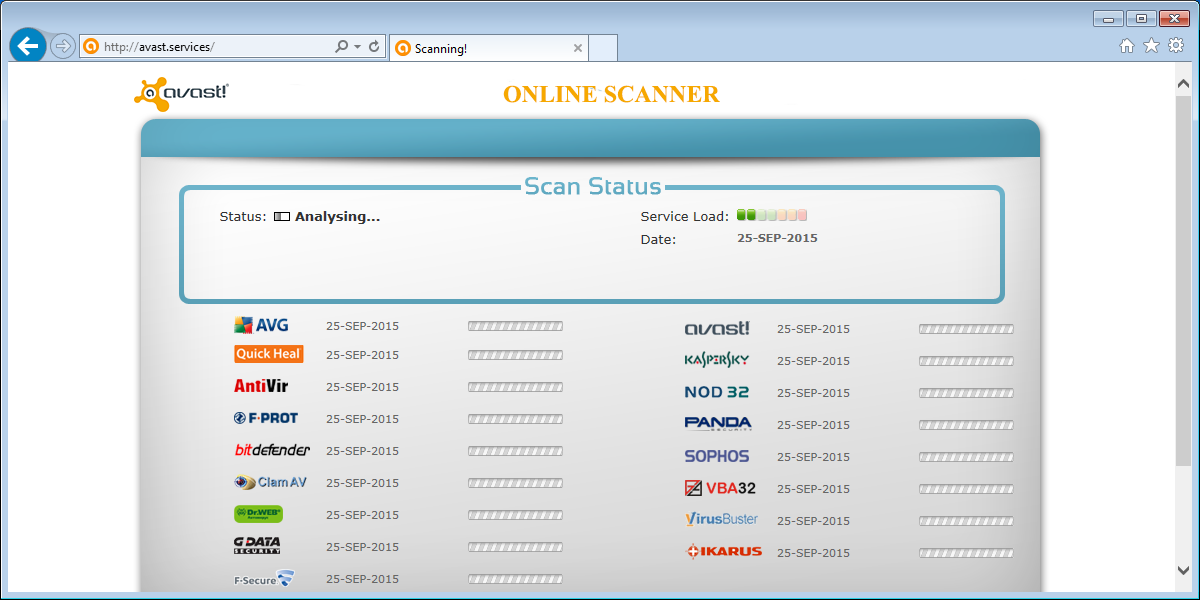
The scanner page looks a bit like Jotti’s malware scan, and they have quite a few logos in common.

The fake scanner will end up showing you that there is only one antivirus that can find a problem which is …. you guessed it, avast! A bit predictable given the name and the logo of the site.
This is where we hope that our readers would get very suspicious. A security software company offering to scan your computer using the scanning engines of competitors would be strange enough, but I’m sure if anyone did they would make it a fair competition and not declare themselves the one and only solution every time.
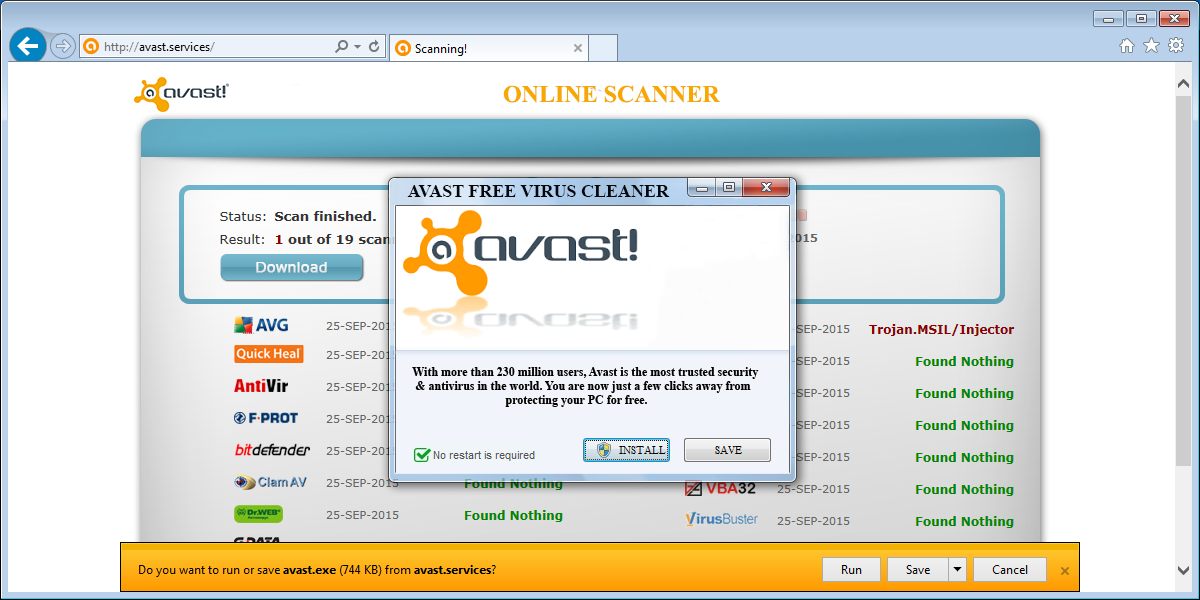
It immediately offers you the options to “Install” or “Save” the file Avast.exe which is obviously not the installer for the actual Avast antivirus software.
What the installer really does is drop an information stealing Trojan in several places on the victims system and point to them from two startup locations.
One is a Run key for the current user pointing to a file in a temporary “System Restore” folder, f.e.
[HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun] "SYSTEM RESTORE"="REG_SZ", "C:Users{user name}AppDataLocalTempSYSTEM RESTORErundll32.exe"The second one is set as a Scheduled Task like this one
Task: {E8F70B70-DDBF-4059-BEA2-09ADAE1A9061} - System32TasksUpdateWindows System32 => C:Users{user name}AppDataLocalTempvbc.exe 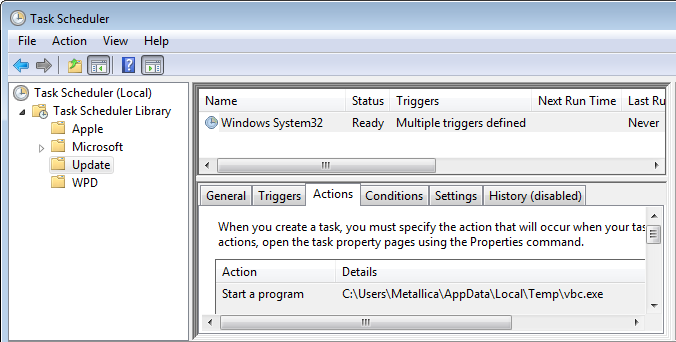
The files where these startups point to are both copies of the Avast.exe we were prompted to download, so running either of them will put any missing ones back in place.
This type of Trojan can be used to gather information on the victims’ computer and encrypt it. The encrypted information will be sent to the operator, who can determine which kind of information will be gathered from the compromised system. In this case the encrypted data was stored in the file
C:Users{user name}AppDataRoamingImminentLogs{date} Malwarebytes Anti-Malware Premium blocks both the redirecting site and the fake scanner site.
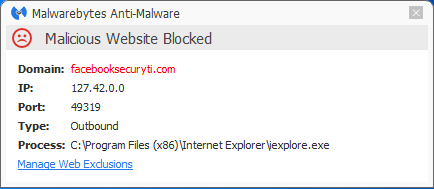
The files involved are detected as Trojan.InfoStealer.Generic and Stolen.Data
Thanks to our friend at hpHosts for the tip.
Pieter Arntz











