Apple quietly added detection of something called “KeRanger” to the XProtect anti-malware definitions in OS X on Saturday.
It was revealed on Sunday by Claud Xiao of Palo Alto Networks that KeRanger is the first real Mac ransomware, and it’s not just theoretical. It’s in the wild.

According to Xiao, the Transmission app – a BitTorrent client – was infected to include this ransomware. The infected app was distributed from the official Transmission website, but with a different code signature than the normal one previously used to sign the Transmission app, implying that the app itself had been modified and re-signed by the attacker (although this has not yet been confirmed).
The modified copy of Transmission includes a file named General.rtf, which is actually an executable file rather than the rich-text document it pretends to be. When the app is launched, this file is copied to a file named kernel_service in the user Library folder (which is hidden by default on recent versions of OS X).
This kernel_service process remains running in the background, and creates additional files named .kernel_pid and .kernel_time in the user Library folder. The latter of these files contains a timestamp, which is used to identify when 3 days have passed.
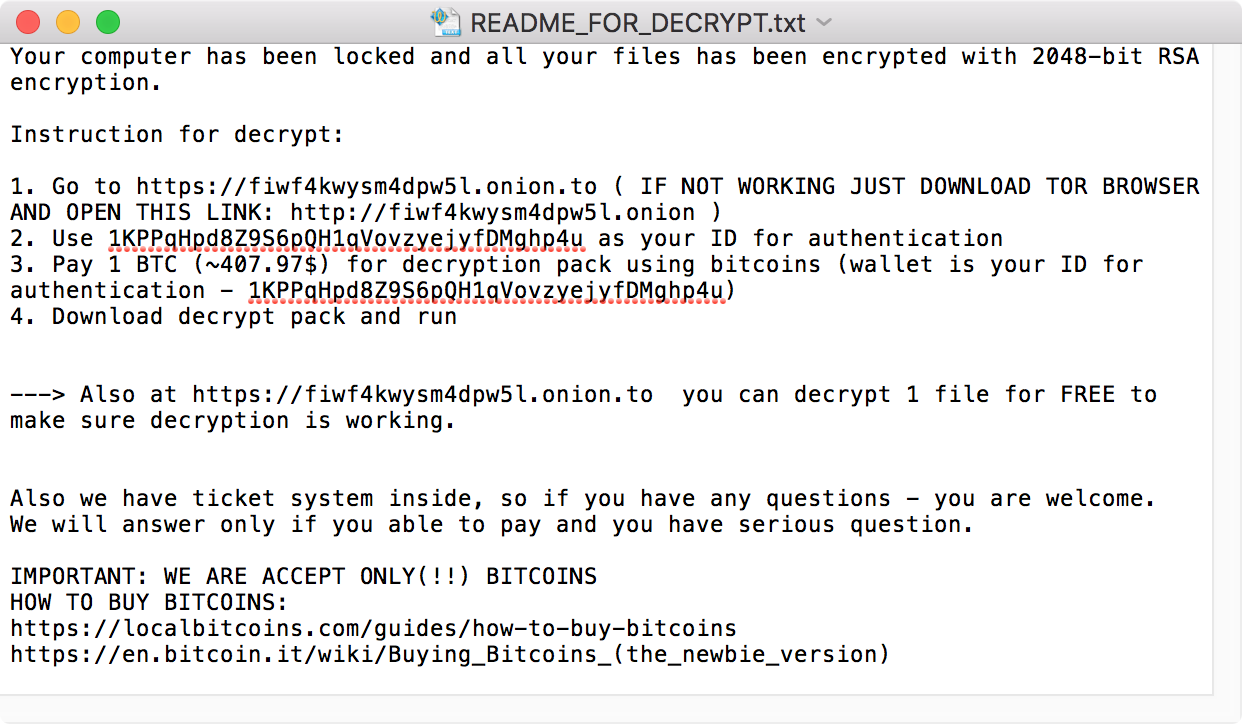
After 3 days, the malware “detonates” and begins encrypting files. According to Xiao, it will encrypt everything in the /Users folder, as well as files having common document extensions found in the /Volumes folder (in other words, files that are on connected external hard drives, servers, etc). In each folder where files have been encrypted, a file named “README_FOR_DECRYPT.txt” is created, containing instructions for how to pay for a decryption key.
The fact that this malware will encrypt external drives and connected network volumes means that it could encrypt backups, including Time Machine backups stored on a Time Capsule. Worse, there is code in the app – though unused at this time, according to Xiao – in a routine called “_encrypt_timemachine”. This means that your backups, which you would want to keep intact in the event of a ransomware infection, may also fall victim to this malware.
Interestingly, there appears to be no persistence mechanism to this malware. The kernel_service process will remain running, but if you restart the computer, it does not start back up automatically. You must re-open the infected Transmission app in order to re-activate the process.
Apple has both added detection of this malware to XProtect and revoked the developer certificate used to sign the malicious copy of Transmission. This means that new infections should not be possible without an update of the malware. However, it’s important to note that if you have already run the infected copy of Transmission on your Mac, this will not prevent you from opening it again… your Mac will consider it safe at this point, since it has been successfully opened previously. That means this doesn’t help users who are already infected and who have a 3-day timer counting down.
Some people may be tempted to pay the ransom to get back their files. However, it’s important to understand that this is an extremely bad idea. In the Windows world, paying the ransom sometimes results in getting a key that can successfully unlock the files. However, it also can result in sending money to the hackers and getting nothing in return, or receiving a key that doesn’t actually work properly because the ransomware was poorly-written.
If you have downloaded the Transmission app recently, you should delete the app and restart your computer. This should prevent re-activation of the malware.
You can also detect and remove this malware with Malwarebytes Anti-Malware for Mac. Keep in mind, though, that any files that get encrypted before removal will be lost (unless they have been backed up and the backups are still intact).
Also, keep in mind that this is not the first time that Mac users have been infected following the download of a torrent client, though always in the past such infections have only been adware. Think carefully before dealing with torrents in the future.










