Email spoofing basically comes down to sending emails with a false sender address. This can be used in various ways by threat actors. Obviously pretending to be someone else can have its advantages especially if that someone else holds a position of power or trust with regards to the receiver.
Why spoof the sender address?
Although most well-known for phishing purposes, there are actually several reasons for spoofing sender addresses:
- Hiding your true identity, although if this is the only goal it can be achieved easier by registering anonymous mail addresses.
- Easy to rotate. If you are spamming, you are bound to be blacklisted quickly. If you’re able to switch sender addresses, who cares?
- Pretending to be someone the receiver knows. This can be used to ask for sensitive information or just plain orders to transfer funds.
- Pretending to be from an organization the receiver has a relationship with. Phishing attempts to get hold of bank login details etc. are the most common example.
- To give the sender a bad name. Sending out insults or other messages that put the so-called sender in a bad light.
- Identity theft. Being able to send messages in someone’s name can be the start of an identity theft procedure.
Countermeasures
Since the email protocol SMTP (Simple Mail Transfer Protocol) lacks authentication it used to be extremely easy to spoof a sender address. As a result, most email providers have become experts at intercepting spam before it hits your inbox. But wouldn’t it be much better if they were able to stop it from being sent in the first place? Well, there have been a few attempts to enforce rules that could accomplish this:
- SPF (Sender Policy Framework): this checks whether a certain IP is authorized to send mail from a given domain. This method uses records that tell receiving mail servers whether an IP is on the list for the sending domain. Unfortunately using SPF lead to many false positives and the rules are applied loosely at best. So this still leaves the work to the receiving server.
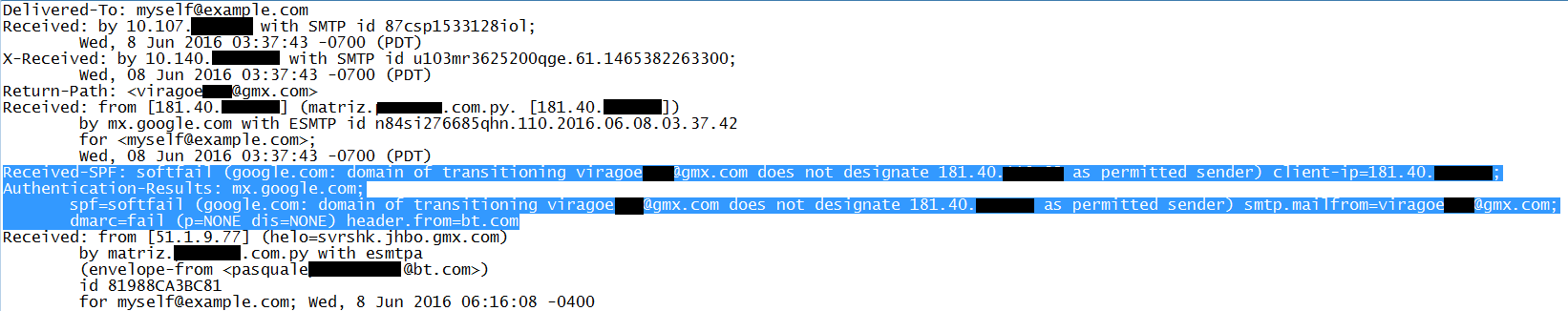
- DKIM (Domain Key Identified Mail): this method uses a private and a public key fetched by a Mail Transfer Agent (MTA). These are compared and only if it is a match the mail will be sent on. But DKIM only signs the specified parts of the message, the message can be forwarded and the signature will still match. This is called a replay attack.
- DMARC (Domain-based Message Authentication, Reporting, and Conformance): this policy gives a sender the option to let the receiver know whether its email is protected by SPF or DKIM and what actions to take and who to report to when dealing with mails that fail authentication. This takes away the doubt on the receivers end, but unfortunately DMARC is not very widely used.
How are they able to pull it off?
The easiest way to spoof mails is if the evil-doer finds a mail server that has an open SMTP (Simple Mail Transfer Protocol) port.
As stated before, SMTP itself lacks authentication so servers that are poorly configured in this way are prey to abusers. And there is nothing that can stop a determined attacker from setting up his own email server.
Having done that there is – freely available – software that will allow you to use any sender address you like. The receiver would have to check the full headers of the mail to find out whether the mail came from the “real sender” or if it was spoofed. This takes some knowledge and time, that you probably do not want to spend on every incoming mail. In these cases however replies go to the actual handler of the email address and not the attacker.
That is why, in cases like CEO/CFO fraud you will often see that the attackers registered a domain very similar to the one of the company they were trying to trick.
A difference in the domain that could be easily missed by the intended victim, like for example ma1warebytes.org. That will enable them to get any replies from their victim in case they were asked for more information or confirmation.
Links
A countermeasure to email sender address spoofing
Email Authentication: How SPF, DKIM and DMARC Separate the Wannabes from the Real Stuff
Pieter Arntz











