Update (06/13/2016): Still no sign of Angler EK activity since late June 6th PST. In the meantime, the actor known as ihateclowns/SadClowns traditionally associated with Angler was particularly active on the week-end, with malvertising attacks on adult sites all leveraging Neutrino EK.
Update (06/11/2016): Security researcher Kafeine has just published a comprehensive post about this major development with Angler EK. It may be too early to say, but this would be as big as the downfall of Blackhole.
Original Post:
We have seen an uptick in drive-by downloads via the Neutrino exploit kit in the past few days. In fact, this is true for various paths to infection and also confirmed by others such as Brad Duncan who saw Neutrino deliver CryptXXX via the pseudo-Darkleech and EITest campaigns.
Case in point, the recent large malvertising campaigns we wrote about are still going on but rather than using Angler EK to infect victims, we see the Neutrino exploit kit instead.
The following is a malvertising incident we caught on Yahoo!. As in previous cases, the rogue advertiser uses a shadowed domain to host the ad banner and malicious code. It’s worth pointing out that threat actors are using some of the open source OpenX ad serving code to profile their victims.
Disclosure timeline:
- 06/08/2016: Yahoo is informed via email
- 06/08/2016: Yahoo acknowledges receipt of our email
- 06/09/2016: Rogue subdomain goes offline
- 06/10/2016: Blog post about this incident is published
:
- Publisher (Yahoo Taiwan): tw.yahoo.com
- Yahoo ads: s.yimg.com/rq/darla/2-9-9/html/r-sf-flx.html
- Fraudulent advertiser: watch.pnwpga[.]com/www/delivery/spcjs.php?{redacted}
- Open redirect: p.rfihub.com/cm?forward=http://hiapi.t1arealize[.]top/blackness/aHVuY2hz
- Neutrino EK landing: ufysefs.t1arealize[.]top/almost/1605620/unhappy-career-health
- Neutrino Flash Exploit (CVE-2016-4117): hiapi.t1arealize[.]top/1977/11/19/pant/member/symbol-twist-beach-victory-wait-jail.html.swf
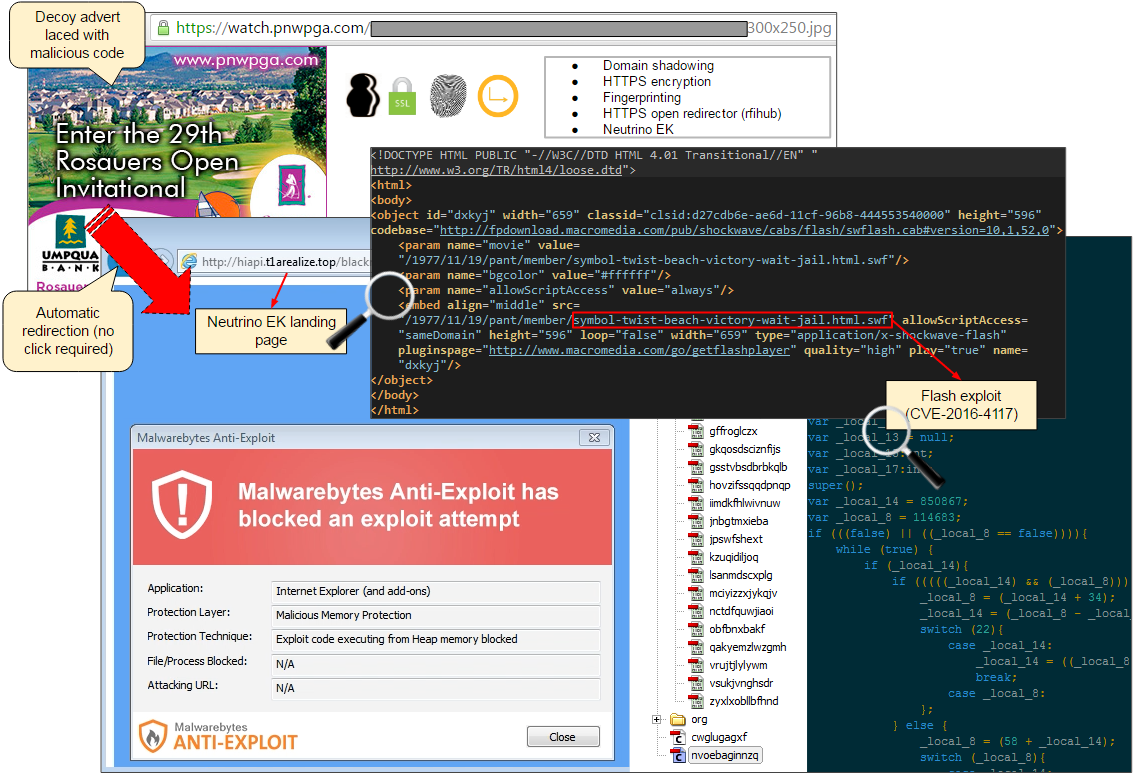
Neutrino has been dropping ransomware lately, mainly CryptXXX but we have also seen it drop Cerber. At the moment, both Angler and Neutrino can exploit Flash Player up to version 21.0.0.213. This switch between the two is not new but this very noticeable change in activity remains intriguing. After all, without Angler the exploit kit landscape just isn’t the same.










