Over the years we’ve done analysis on tech support scammers to include their tactics, infrastructure, front companies, payment mechanisms, and even how they hire. But one question that comes up frequently from security researchers is how a group of criminals, who are by most accounts computer illiterate, set up tech support scams that require a hard minimum of technical expertise, troubleshooting, and maintenance? How is a criminal so oblivious as to use his real name and cellphone to register a ‘company’ website can be sophisticated enough to set up infrastructure handling ad network tracking, SEO cloaking, and payment processing? The main answers are firstly that a segment of the market for these scams genuinely believe themselves to be legitimate businesses (a sentiment that deserves its own separate blog post), and second is the Scam in a Box.
Recognizing that the best way to make money in a gold rush is to sell shovels, the more enterprising criminal underclass has set up pre fab scam packages that only require a credit card and ill intent to set up. One particular Scam in a Box, inboundpopaps.info, is a little more brazen than most.
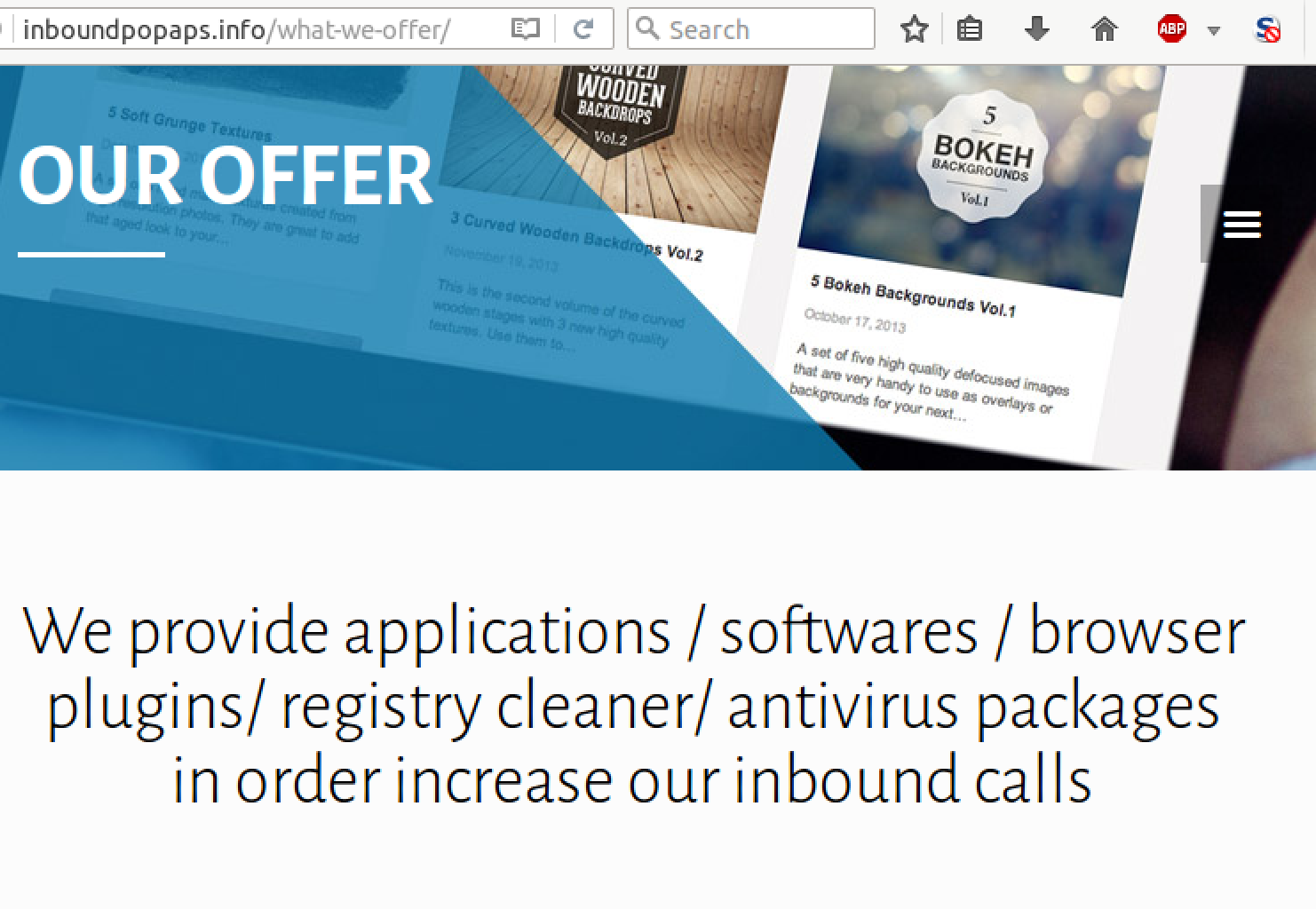
Pretty cut and dry. “We provide malicious software for fraudulent purposes.” Also notice the admission that PUPs and tech support scams go hand in hand. For more on this connection, see Pieter’s post here. Inboundpopaps is considerably more slick than most scams on the market, and even attempts to limit traffic to real, paying customers. Indian cyber criminals traditionally operate with a somewhat lower level of OPSEC and technical acumen, though, which leads to situations like the following:

The criminals are making a weak attempt to filter out window shoppers and security researchers with an overlay blocking their content.
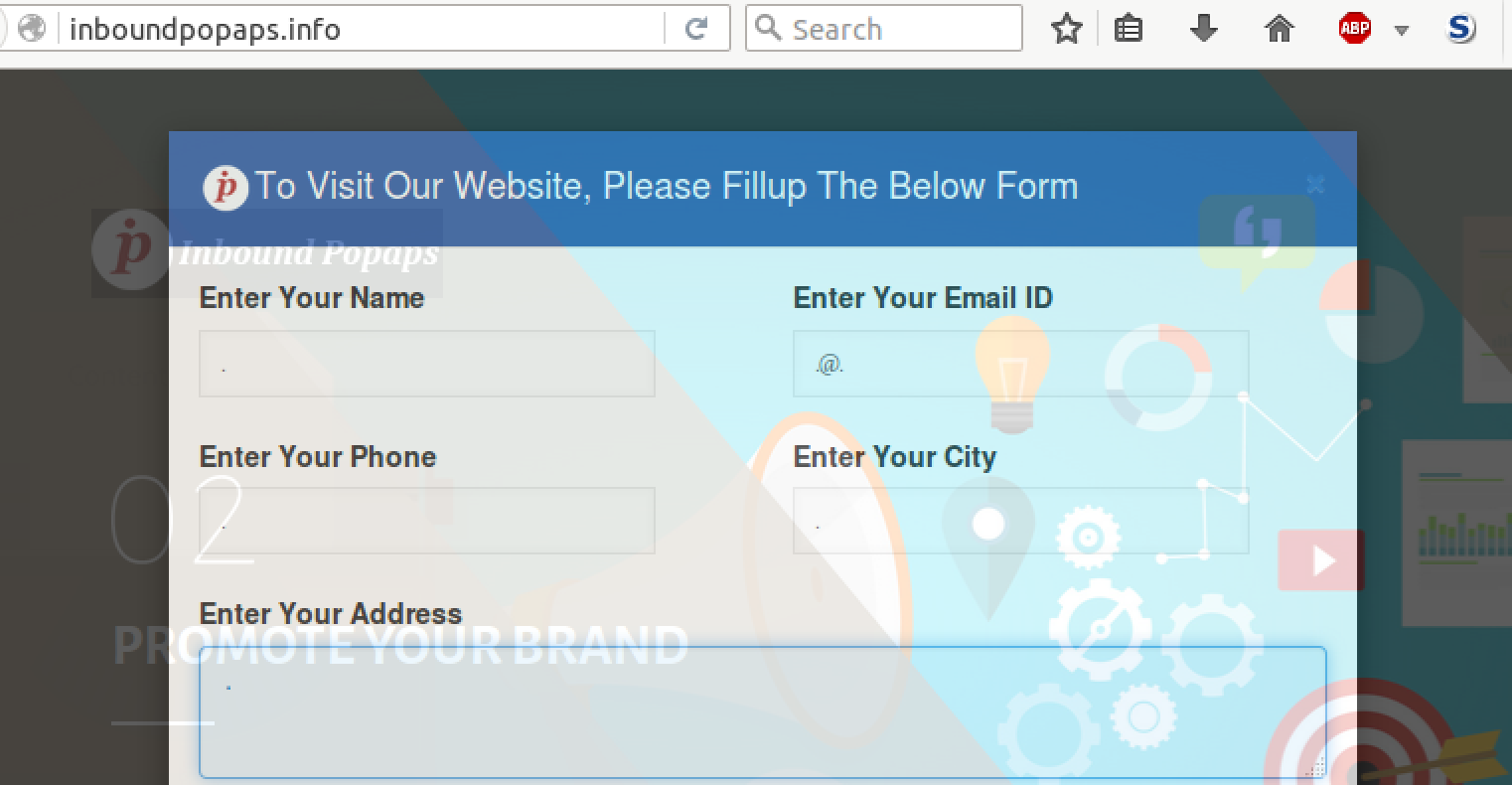

Some readers wonder why non-English speaking threat actors will include amateurish language mistakes like that in the above screenshot. Surely you would present a better image by using a native language without fluency issues? Not quite the case. English fluency often requires formal education, and can therefore connote a certain sophistication level that a local dialect would not. Further, more developed criminal markets are quite happy to collaborate with scammers in other nearby countries, making a commonly spoken third language like English quite handy. But lets get some more details about what this particular Scam in a Box has on offer:
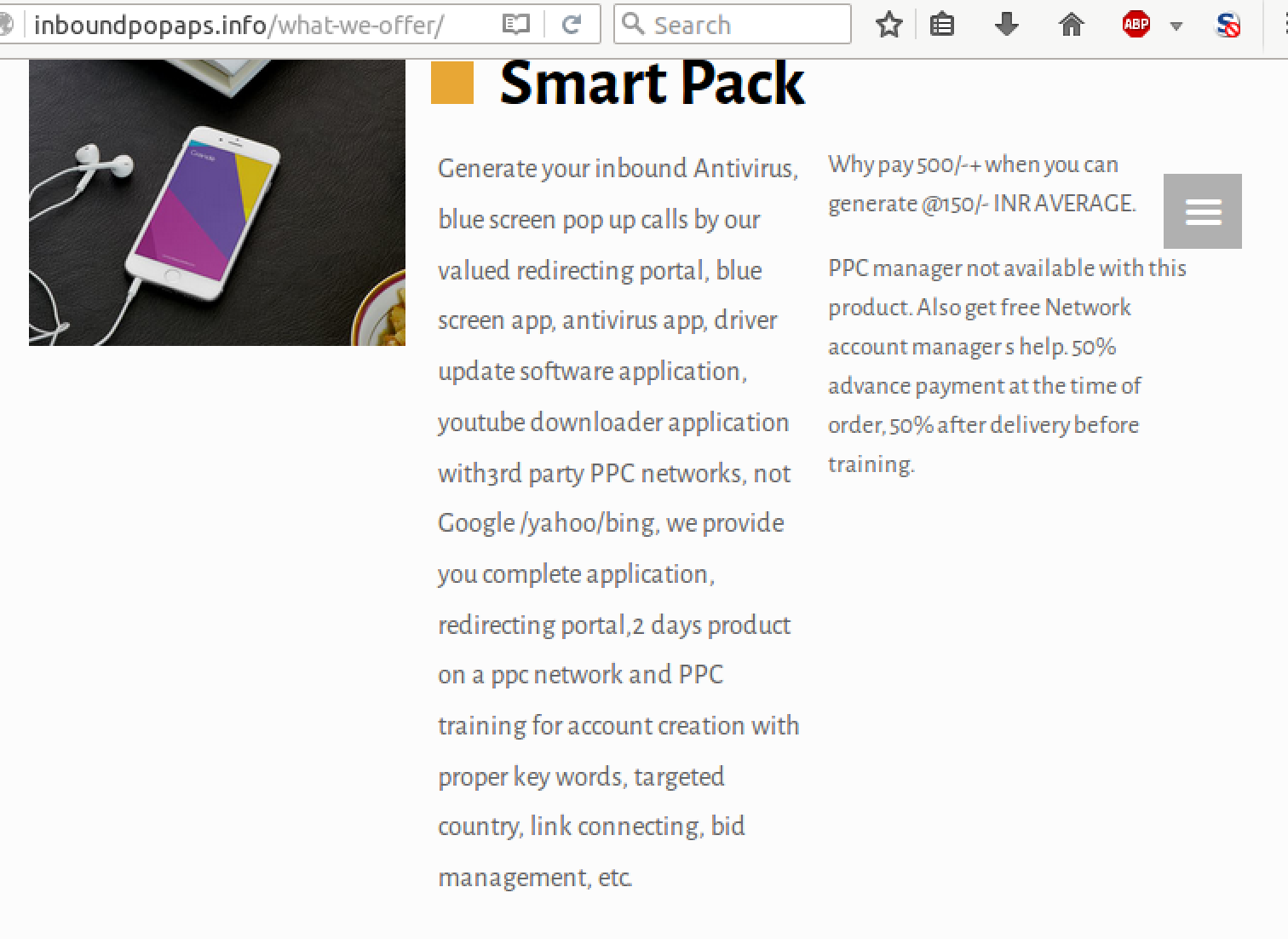
Very comprehensive. This is essentially an offer to generate browser lock screens of the sort discussed here, and monetize the traffic via some off-brand ad networks.
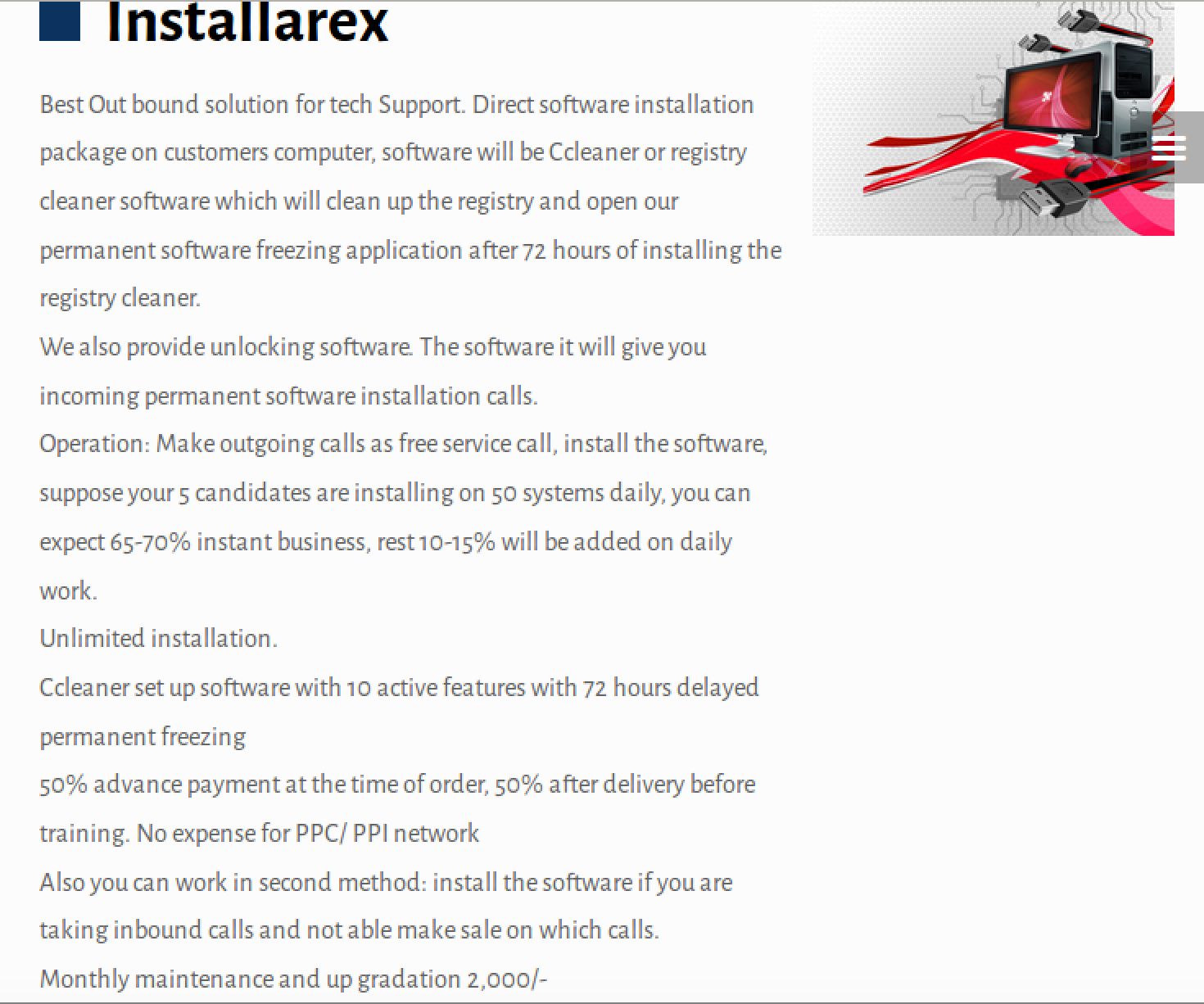
Our next step up is PUPs that hide locking software that will render your computer unusable, along with training to infect users most efficiently. Most notable here is “also you can work in second method: install the software if you are taking inbound calls and not able make sale on which calls.” In other words, if you don’t buy their ‘services’ they’ll wreck your computer. Fortunately, this type of locking software tends to be amateurish and easily defeated. (Check out Pieter’s post linked above for more on that.)
Lastly, we see offers for fake mobile apps, along with training on how to sneak them into assorted app stores. This is intriguing as mobile tech support scams aren’t extremely common. Unfortunately, as much as we’d love to “Ask For Price”, that link simply reloads the page. The blurb for windows lockers quotes the monthly maintenance as 2000 IND per month, which equates to about $30 USD. Given that price is for one of the more resource intensive scams, one might presume the others are even cheaper.
Scams in a Box like these are relatively common, but are rarely this brazen. More frequently, middlemen will advertise in thinly disguised terms on Linkedin and Facebook, where prospects will be redirected to Whatsapp to close the deal. Some will even stipulate “No North American customers” as a crude filter to keep security researchers and law enforcement out. But with the rush of money available with tech support scams, and search engine actions against tech support ads, some of the threat actors in the field have decided to quit getting their hands dirty, and start selling shovels to the miners still in the game. While PUPs still provide great cover for all sorts of nasty activity, we can expect these sorts of services to continue unabated.
For more on Malwarebytes’ hard line on PUPs, check out this post.










