Memes are weird things and weren’t always about lolcats or frogs or whatever the latest terrible image macro doing the rounds happens to be. I quite like this line from Wikipedia on said subject:
Proponents theorise that memes are a viral phenomenon that may evolve by natural selection…Memes that propagate less prolifically may become extinct, while others may survive, spread, and (for better or for worse) mutate.
The plot of The Ring is pretty much the concept of a meme made deadly – pass on this cursed videotape within 7 days, or you die horribly.
How far will you go to save yourself?
Well, our old friend 2016 is here to ask that question one more time, because ransomware authors have decided to tweak their victim’s get out of jail method. Don’t have the funds to obtain an unlock key? No problem – just infect two people and you’re back in business (assuming they pay up to unlock their own files). It’s all gone a bit pyramid scheme, hasn’t it?
Interestingly, the time limit to regain your files is the same as the time limit imposed on potential victims of Sadako: seven days.
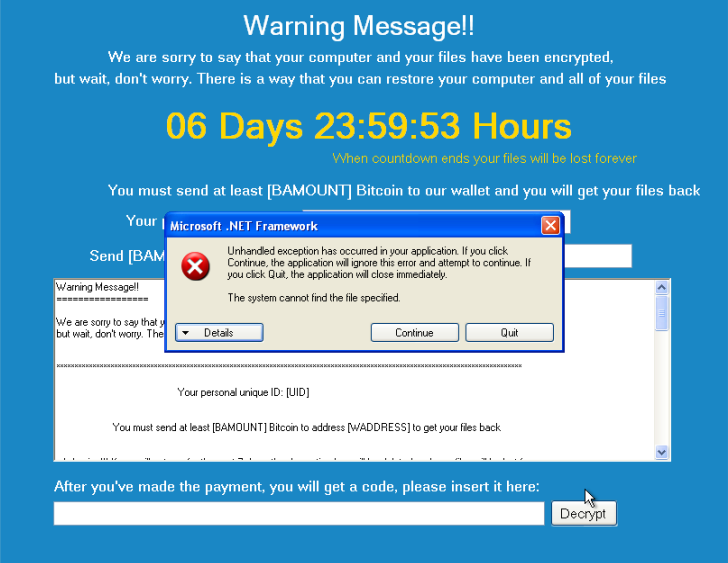
The only way that could be creepier is if they’d released this during Halloween.
Named after the well known BitTorrent client Popcorn Time, this file goes one step further than most in a mission to make some money. It encrypts files in the usual places – Documents, Music, Pictures and Desktop – and targets pretty much every file extension under the sun. After encryption, the splash screen explaining what’s happened claims the creators are from Syria and that money generated from the ransomware will be used for “food, medicine, and shelter”.
At this point, the choices available boil down to randomly entering a key to unlock the files (not a good idea, as there is mention in the source code that incorrect key entry may eventually result in automatic file deletion), or to play the game and begin the process of infecting other people, in the hopes of obtaining an unlock key.
Note that it isn’t enough to infect another person – you have to hope they pay the ransom too, or they don’t count as a notch on your tally of victims.
All of this only works on the assumption that the ransomware authors will actually provide an unlock key and that is certainly up for debate. It’s also probable that victims won’t want to risk friendships so they’ll end up trolling for random victims in chat rooms, social media and other fish in a barrel locations. In other words, like common or garden script kiddies going about their daily business.
What a mess!
As Graham Cluley mentions, you don’t want to risk getting into trouble with the law because you decided to save yourself by torching the data of others. Should you fall victim to a piece of ransomware, don’t give up hope – many of these files are poorly coded and in many cases, members of the security community, independent researchers, security firms, and more besides manage to come up with decryption tools.
Meanwhile, users of Malwarebytes 3.0 will find we detect this as Ransom.FileCryptor.
Christopher Boyd










