It’s easy to run into mentions of the Darknet and its many ills, real or imagined. Even the late CSI: Cyber made frequent reference to the Darknet. Interest in Tor based threats is increasing to the extent that some vendors will scoop up all activity they find on Tor and provide you a nice front end to search through it at your leisure. This might lead the casual observer to assume that the darkness is a one stop shop for cyber threats, but criminals existed on the internet prior to Tor, and still do quite well for themselves without it. In fact, bad guys with good OPSEC tend to be the exception, rather than the rule. So let’s take a quick look at some unpleasant stuff and the nadir of bad OPSEC, Facebook.
We’ve blogged previously on the Scam in a Box. But more common are bad guys simply selling lock screens, phone support lead generation, or both.
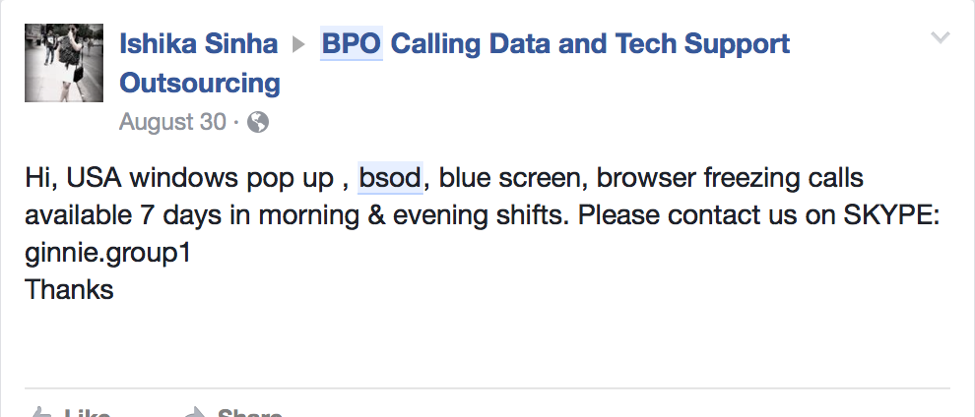
These posts are fairly common, leading some criminals to differentiate their offerings with custom tooling as follows:
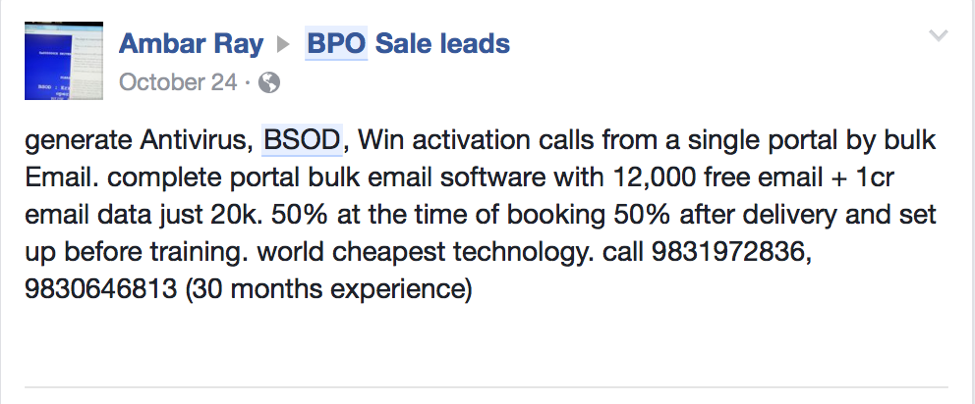
Following along the trend we’ve observed, of the higher tier scammers escalating tactics to stay ahead of enforcement measures, “Windows activation” calls are seeing a surge in popularity. The PPI, or Pay Per Install, referred to below is a great way of driving victim calls to your call center without any web based infrastructure that can be used to track you down later.
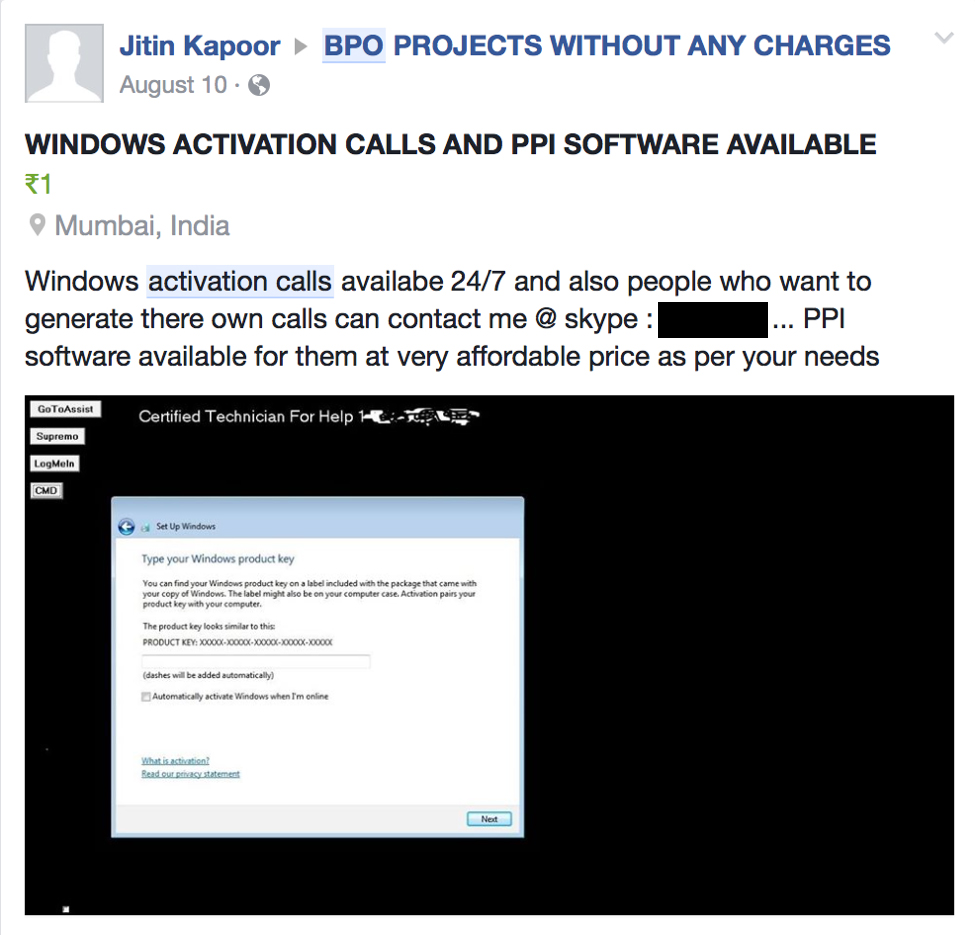
But what about ad networks cracking down on tech support scams? What about popular search engines disallowing third party tech support sites in their rankings at all? How could such a thriving criminal marketplace exist under these conditions? Well, it largely doesn’t. A significant portion of these postings are themselves scams, designed to take a criminal’s money in exchange for a non-functional product, or sometimes nothing at all. Here’s a post linked from a public Facebook profile.
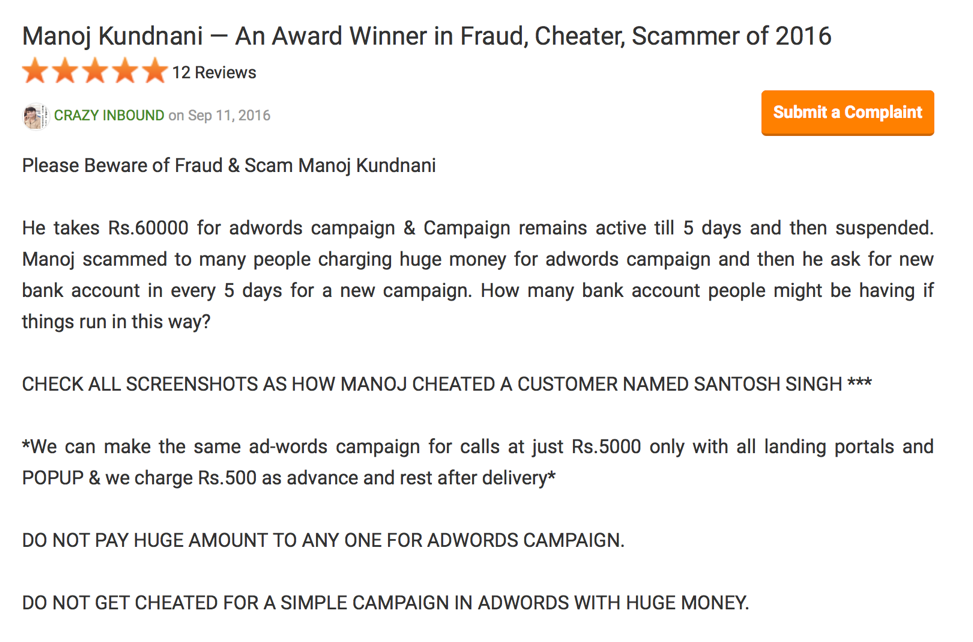
Things wrong with this picture:
- Google adwords banned these sorts of campaigns years ago.
- The poster doesn’t seem to understand why you might need to rotate account details when promoting something harmful/illegal.
- 500 is about 7.50 USD. If Rs.60000 was insufficient to evade Google counter-fraud measures, it seems improbable that the price of a cup of soup could buy you better service.
- The poster included his name and contact information at the bottom of the post. (not pictured)
Why is this sort of thing trivially easy to find? To hazard a guess, most large platform content security monitoring is done algorithmically, with a weighted list of phrases and words that elevate items to a human analyst. Doing so with tech support scams runs a huge chance of false positives flagging legitimate outsources services centers. In all probability, a human security analyst never sees any of these posts and therefore can’t act against them.
So to sum up, tech support scams have a robust tooling and infrastructure market, out in the open with no obfuscation whatsoever. Some scammers will specify Indian clients only as a crude way of vetting, but most don’t. They operate profitably and with impunity, based largely on a belief that distance from the United States makes them untouchable. Also, based on the frequency and vehemence of “BPO Scammer” posts, a not-insignificant minority seem to believe that what they’re doing isn’t actually illegal. Suffice it to say, Malwarebytes disagrees.










