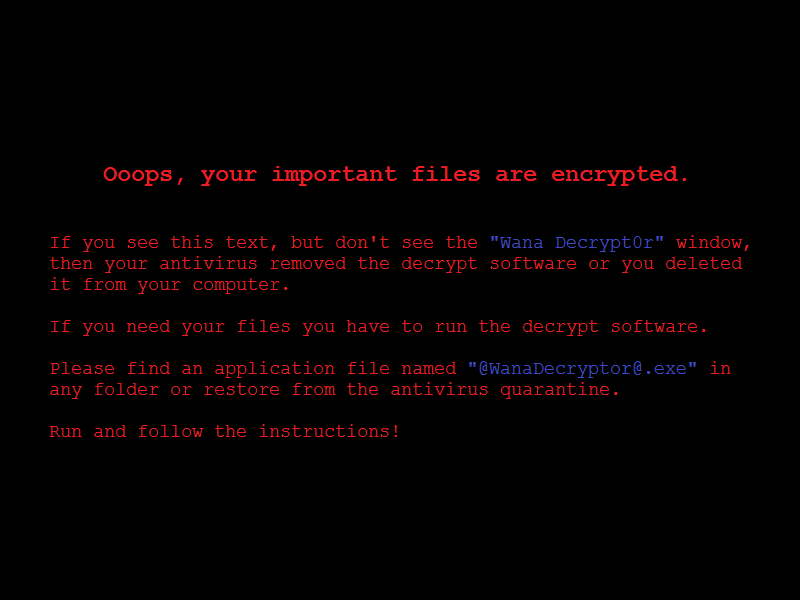
UPDATE (as of 5/18/17):
- Research has shown that the worm component of this cyberthreat does not work on Windows XP. The ransomware however does work on Windows XP. But there are other good reasons to apply the patches that Microsoft issued for EOL operating systems, because there are other SMB related exploits patched by it.
UPDATE (as of 5/17/17):
- The technical analysis was published: The worm that spreads Wanacrypt0r.
- Microsoft issued patches for Windows versions that are EOL.
- Many reports about victims not getting their files back after paying the ransom.
- Fake Twitter accounts impersonating the man from the UK that registered the first kill-switch domain.
- New variants with other kill-switch domains have surfaced, but not likely from the same authors.
Reports of two massive, global ransomware attacks are dominating the news. As workers in Europe are heading home for the weekend, ransomware is shutting down their systems. Here’s what we know so far.
Big targets
National Health Service (NHS) England, and Telefonica, one of the largest telecom providers in the world, have each given out statements indicating that their systems have been brought to a grinding halt by a ransomware that Malwarebytes detects as Ransom.WanaCrypt0r. The ransomware has also been observed hitting companies in Spain, Russia, Ukraine, and Taiwan.
Method
The ransomware is spread using a known, and patched, vulnerability (MS17-010) that came from a leaked NSA set of exploits that we reported on our blog in April. Our research shows the encryption is done with RSA-2048 encryption. That means that decryption will be next to impossible, unless the coders have made a mistake that we haven’t found yet.
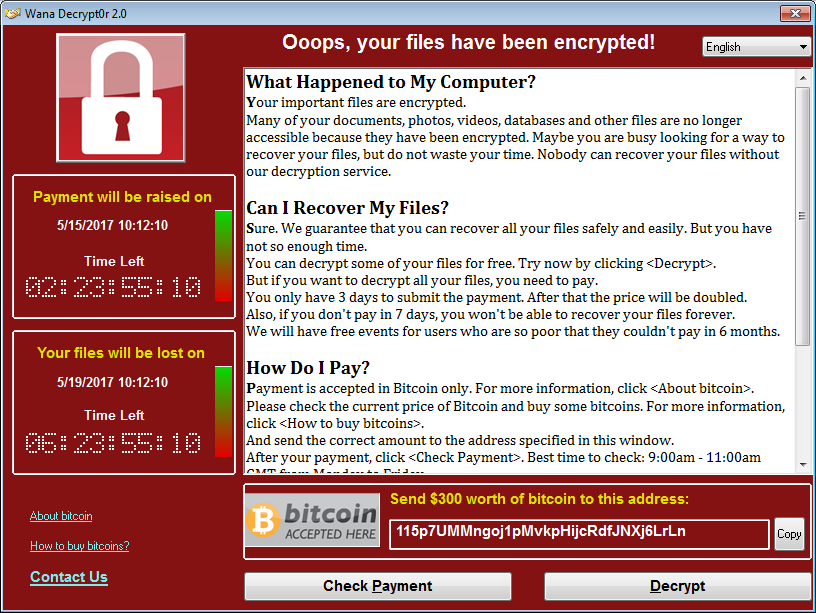
The demanded ransom of $300 per device and the potential risks to the public that come with the targets being big utility and healthcare companies seem to be in shrill contrast. We can only hope that the companies that were hit will be able to get their backups deployed quickly and can start the recovery from this cyberattack.
Protection
Consumers and businesses alike should be sure their systems and software are updated with all current patches in order to stop the spread of infection. Both our consumer product, Malwarebytes, and our business product, Malwarebytes Endpoint Security, already provide proactive protection against this threat. Malwarebytes signature-less anti-exploit technology blocks the infection vector, while our anti-malware technology blocks the payload pre-execution. Our anti-ransomware technology prevents users’ files from being encrypted and will stop any future unknown ransomware variants. Malwarebytes combines multiple security layers with the best-informed telemetry to block an attacker at every stage of the kill chain.
In addition, updating your endpoints with the latest Microsoft security patches will ensure that the infection could not spread to any of your additional systems (or possibly infect your network at all).
Recently, Microsoft also made available updates for operating systems which no longer receive security updates, like Windows XP. Please check out their article about the changes they have made and how to protect any outdated / legacy systems.
More to come
We’ll continue to update this post as news develops. We’ll provide additional technical analysis throughout the day.