Last June 27, there was a huge outbreak of a Petya-esque malware with WannaCry-style infector in the Ukraine.
Since there is still confusion about how exactly this malware is linked to the original Petya, we have prepared this small guide on the background of the Petya family.
The origin of Petya
The first Petya ransomware was released around March 2016 by a person/group calling themselves Janus Cybercrime Solutions. This group was advertising their affiliate program, giving other criminals a chance to distribute their malware. Janus Cybercrime Solutions was represented also on Twitter by appropriate accounts, first by @janussec, and then by @JanusSecretary.
The names “Janus” and “Petya” were inspired by the James Bond movie, GoldenEye. The threat actor was consistent with the chosen theme, too—the profile picture of the linked Twitter account was from one of the characters of the movie, a computer programmer/hacker named Boris Grishenko.

Unique features
From the very beginning, Petya has been a unique ransomware because it has features that are not common for this type of malware. While most of the ransomware can only encrypt files one by one, Petya denies users access to the full system by attacking low-level structures on the disk.Petya is always installed by some dropper, which is a Windows executable (on each version of Petya the dropper is replaced with a new one).
During installation, the Petya installer overwrites the disk with Petya’s kernel and boot loader. Because of this, the affected machine boots the malicious kernel instead of the legitimate OS. On the first run, it displays a fake CHKDSK screen:
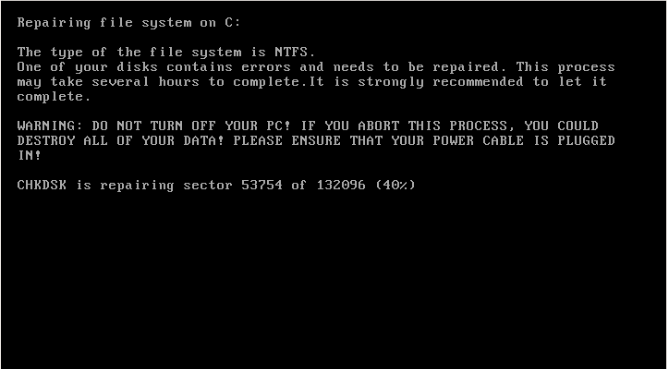
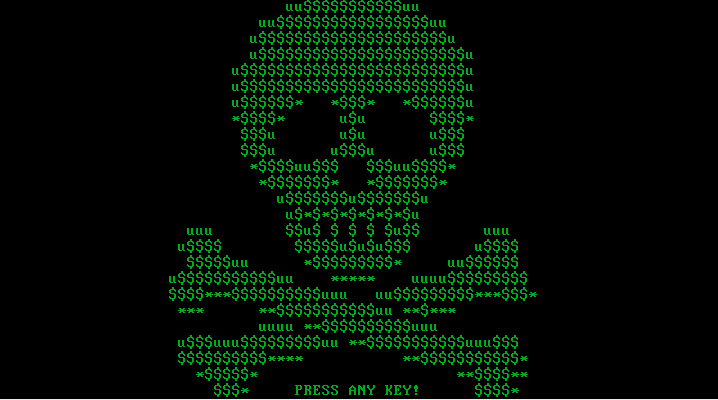
Instead of checking the disk, in reality, it encrypts the Master File Table (MFT) with Salsa20. This way, the ransomware makes the disk inaccessible. When encryption is finished, two screens are displayed: a blinking skull followed by the ransom demand. This is how affected system screens look like in the first version of Petya:
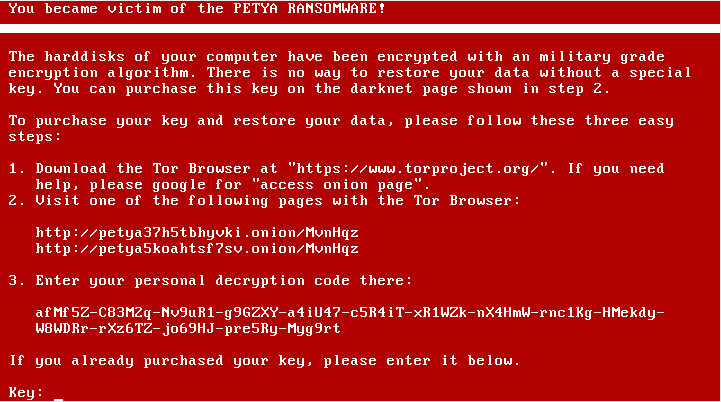
Official releases
So far, there are 4 releases of Petya ransomware by its original author, Janus:Recently, Janus released the master key that can unlock all official versions described above. You can read more about it in this blog post.”>
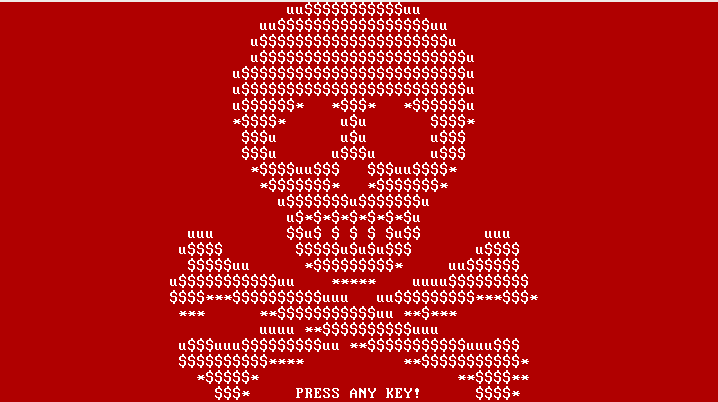
These Petya releases can be identified by the theme colors. We’ve put together a small gallery below:
Red Petya
Green Petya
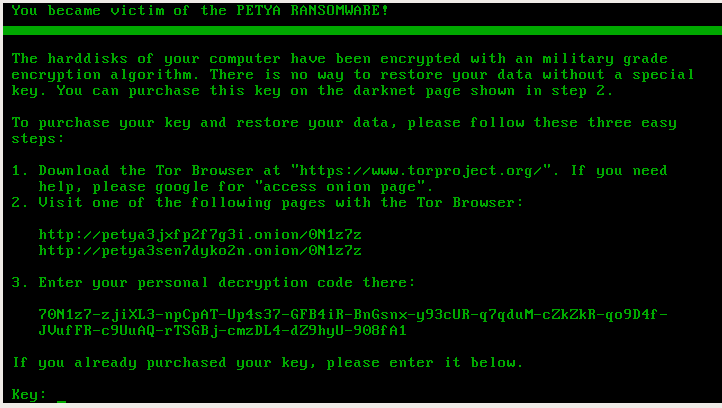
GoldenEye
“>

GoldenEye was the latest official release of Petya and was last seen around December 2016.
Unofficial releases (pirated versions)
Since Petya is powerful, other cybercriminals have been attracted to use it. However, not all of them want to join the affiliate program and pay its creator. Similar to legitimate software, Petya has pirated versions. So far, we observed two unofficial releases:
- PetrWrap – uses Petya’s low-level component as well as patched Petya’s DLL, wrapped by a new loader. It’s based on Green Petya.
- EternalPetya – also called NotPetya, ExPetr, etc. The malware based on GoldenEye, used in the attack on Ukraine. The high-level layer (PE file) has been rewritten.
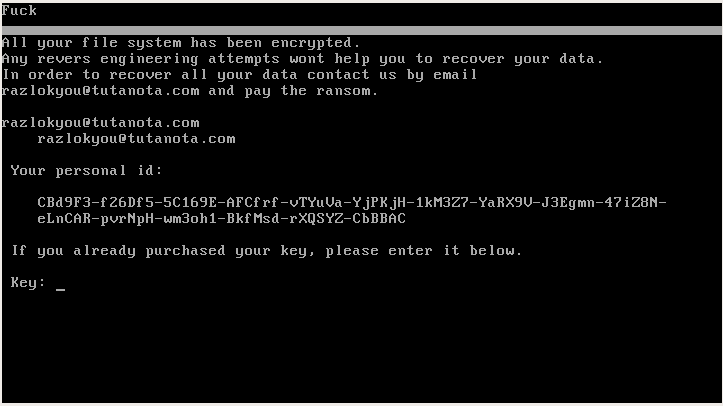
The pirated versions can be identified by the modified look. In both cases, the original Petya’s skull has been removed.
PetrWrap
EternalPetya
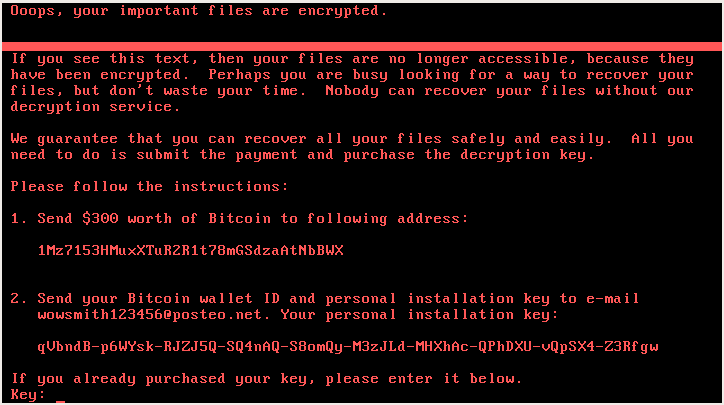
While PetrWrap was a fully-functional ransomware, EternalPetya seems unfinished or broken on purpose because the Salsa key that used to encrypt the MFT cannot be recovered. Once encrypted, data cannot be decrypted, even by the malware authors.
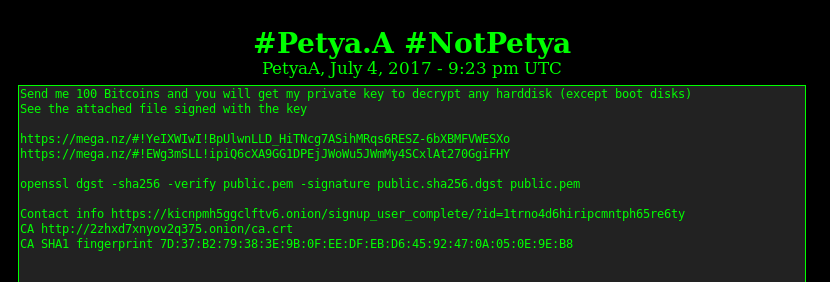
Same as the original GoldenEye, EternalPetya encrypts also files with the selected extensions before attacking the MFT. Files are encrypted using different algorithms and keys than the MFT (RSA + AES, while the MFT is encrypted using Salsa20). On July 4, the distributors of EternalPetya raised the ransom demand and offered to sell the private RSA key that can potentially help in unlocking encrypted files but not the MFT. Below is the message from the attackers [source]:
Copycats
In addition to malware based on the original Petya, copycats also have started to appear. They have nothing in common with Petya’s code, they only try to imitate its look or some of its features. Some examples areConclusion Ransomware piracy is becoming common and this triggers more problems to the victims. Often, the authors of such pirated malware don’t care to give the data back. They just use the reputation of known ransomware to scam victims into paying. In addition to the described cases, we have also encountered several versions of pirated DMALocker, wherein some of the variants corrupt the data that make recovery hard or even impossible.”>
Petya is a powerful malware. And to make things worse, it is also very easy to modify and repurpose. Even if the official line of Petya has been discontinued, we can expect the pirated versions to still be around.
This was a guest post written by Hasherezade, an independent researcher and programmer with a strong interest in InfoSec. She loves going in details about malware and sharing threat information with the community. Check her out on Twitter @hasherezade and her personal blog: https://hshrzd.wordpress.com.










