On Monday, Patrick Wardle, a respected security researcher at Synack and owner of Objective-See, sent a tweet about a keychain vulnerability he had found in macOS High Sierra. As his tweet showed, it is possible for a malicious app to extract, and then exfiltrate, keychain data from High Sierra, with passwords clearly exposed in plain text.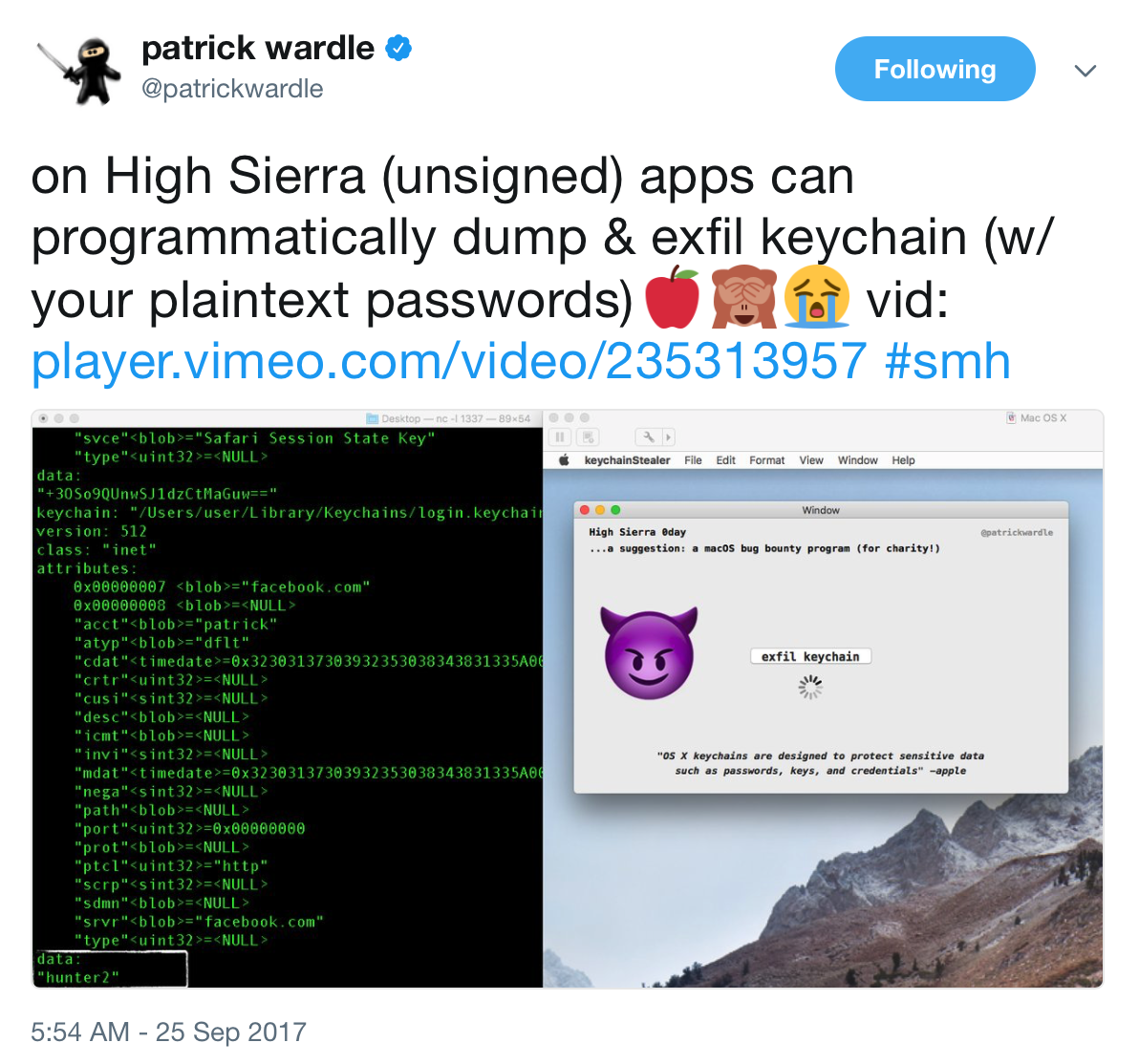
In response to some questions, Wardle has also posted some additional information in an FAQ on Patreon.
This announcement set off a firestorm of articles on a variety of sites, which unfortunately caused a lot of FUD (fear, uncertainty, and doubt). In at least one case, I saw an article saying to hold off on installing High Sierra until this bug is fixed. It seems that many of these articles were written based solely on the contents of that tweet, but there is much more to be said.
It’s important to understand that the idea that people should wait to install High Sierra because of this bug is a very bad one, for multiple reasons.
First, as Wardle points out in his FAQ, this bug also affects Sierra and probably affects El Capitan as well. For all we know, it may go back further than that… only testing older systems can say for sure. So, you’ve probably got the vulnerability already anyway, whether you upgrade to High Sierra or not.
Second, installing updates and upgrades is an extremely important thing to do to keep yourself secure. If you don’t update, you don’t get important security fixes. If you skip upgrading to High Sierra because of one vulnerability (which you’re already vulnerable to anyway), that may mean that you will continue to be vulnerable to other issues that may have been fixed in High Sierra, but not in Sierra.
Keep in mind that the Mac fix for the extremely serious Broadpwn vulnerability was, apparently, only applied to macOS Sierra 10.12.6. So the old common knowledge that Mac security fixes go into the last three systems (El Capitan, Sierra, and High Sierra) does not seem to still be true, if it ever really was.
Third, let’s pretend for a moment that this was a vulnerability only affecting High Sierra. If you skip High Sierra, that implies that you think doing so makes you safe from keychain theft. Think again.
Consider, for example, the issue described in a blog post by Brenton Henry, in which a combination of an Apple tool and an AppleScript could be used to extract the contents of the keychain. Although the script used in Henry’s post does not work as-is on macOS Sierra, it can be modified to work (although some social engineering would be needed to get the user to give “assistive access” to the script).
Further, this is a known vulnerability. That means that any script kiddie capable of doing a Google search and find an updated script would be able to implement it; it’s not that hard to do. Nobody knows yet how the vulnerability found by Wardle works, only that it exists.
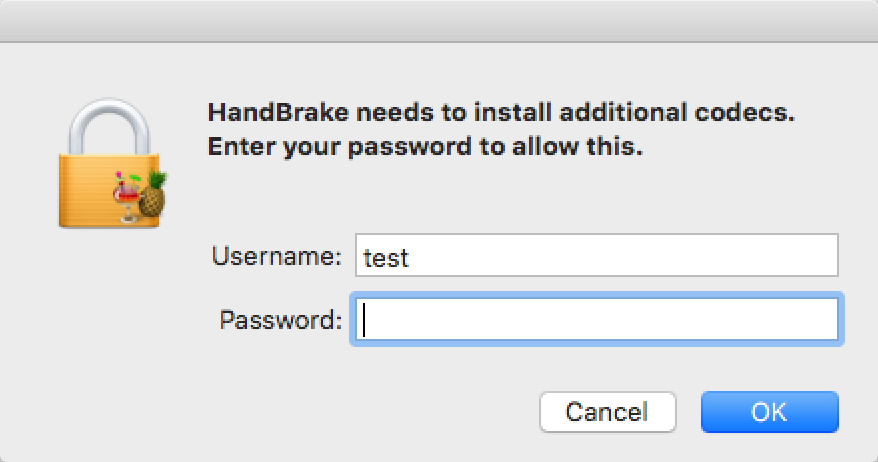
As another example, think about the compromise of the HandBrake app in May, which led to systems being infected with the Proton malware. In that case, Proton was able to successfully trick the user into providing their password, and then exfiltrated that and their keychain files (among other things), which could be unlocked using that same password in most cases.
There was also the case of an interesting sample of the Dok malware one of our researchers received in a junk e-mail, which used an open-source Python remote access tool (RAT) that had the capability to exfiltrate the keychain and convincingly phish a user’s password.
These last two examples would work on any system, including High Sierra since they involve theft of both the user’s password and the keychain files.
Don’t get me wrong, this is a very bad vulnerability, and Apple should fix it as soon as possible. However, it’s not a world-ending catastrophe, nor is it a good reason to avoid installing High Sierra. There will always be vulnerabilities. Keeping your system and your software up-to-date is one of the best ways you can cope with them.










