SamSam ransomware is a custom infection used in targeted attacks, often deployed using a wide range of exploits or brute-force tactics. Based on our own run-ins with the infection, we’ve observed that attacks were made on targets via vulnerable JBoss host servers during a previous wave of SamSam attacks in 2016 and 2017.
In 2018, SamSam uses either vulnerabilities in remote desktop protocols (RDP), Java-based web servers, or file transfer protocol (FTP) servers to gain access to the victims’ network or brute force against weak passwords to obtain an initial foothold. From there, the ransomware “fun and games” begin for the authors. For everyone else, it’s chaos.
The ties that bind
A common thread tying all of these attacks together is the use of the word “sorry” in ransom notes, URLs, and even infected files. It’s made hundreds of thousands of dollars so far, and it’s caused no end of trouble in the US for cities like Atlanta.
Here’s what a typical ransom splash screen looks like:
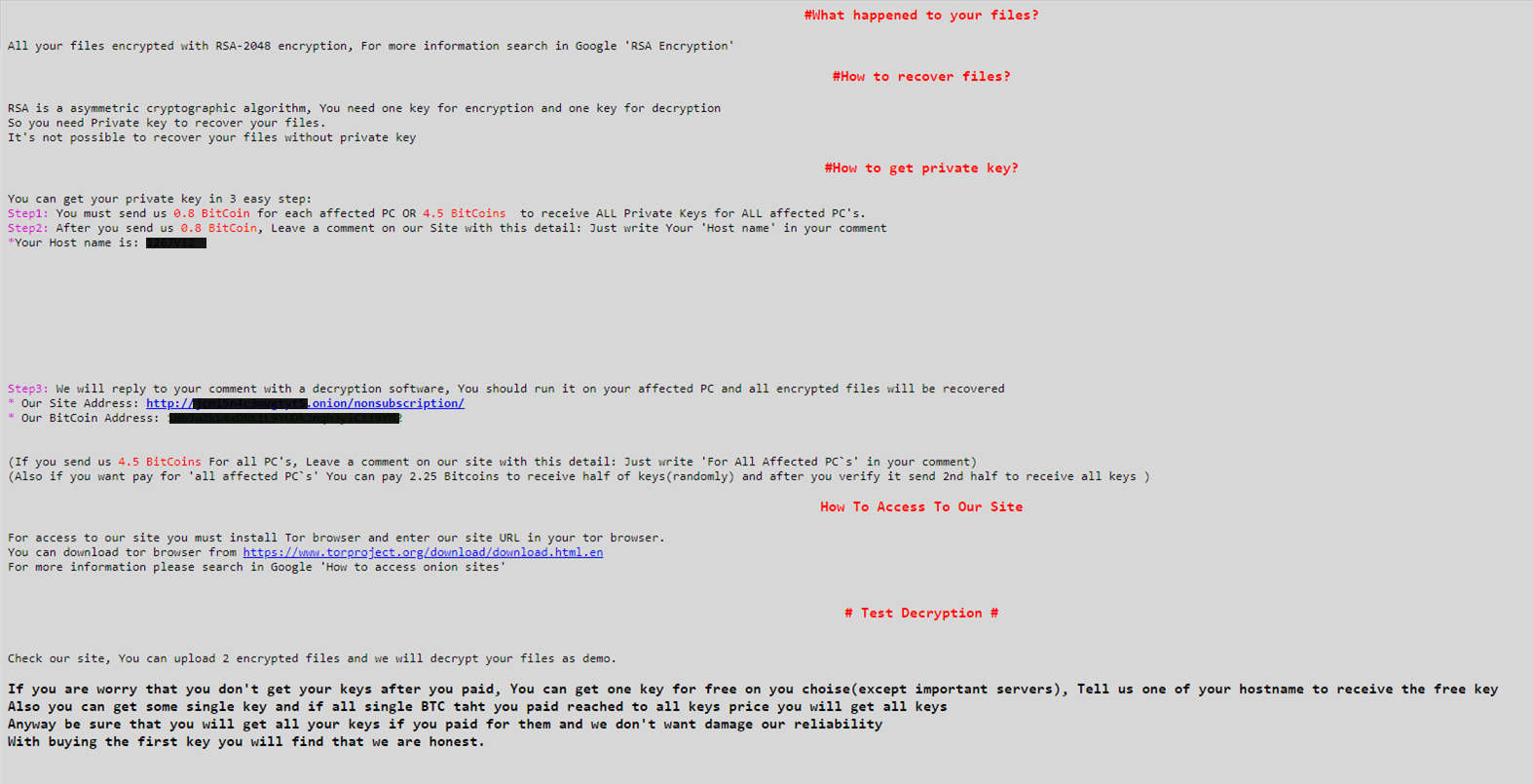
The ransom note is quite interesting, giving the option of randomly-selected file encryption (if you don’t pay the full amount). They’ll also unlock one file for free as a token of trust that they will give your files back after payment. It reads as follows:
Ransomware authors rely on the victim viewing their odd code of “honesty” as important, or else nobody would dare to pay up.
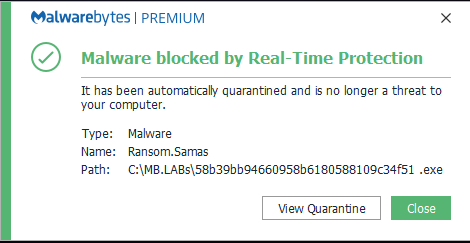
I should also mention, before we go any further, that we do protect against this specific threat, which we detect as Ransom.Samas:
The SamSam group have been making waves since late 2015, causing trouble in 2016, and starting to regularly increase the cost of their ransom in 2017. Colorado and Atlanta have both had run-ins with SamSam recently, as you may have seen from ongoing news coverage.
One would think SamSam has been around long enough for organizations to be able to deal with it effectively, but it’s still here, and still locking up machines in targeted attacks.
You can trace SamSam’s first2018 appearance in back to January. There’s “persistent” and then there’s SamSam.
January: Sorry, not sorry
Hospitals, city municipalities, and many more from Indiana to New Mexico were all struck down by SamSam in varying degrees of severity. A hospital in Indiana, in particular, was reduced to working with pen and paper in stormy weather. They decided to pay the ransom and get systems back up and running, given the cost of the fix was more than the ransom. This is an organization that had backups in place, unlike many other ransomware victims. All the same, by attacking a service offering life-saving treatment to patients, staff were left with few options.
Though you’ll find conflicting advice on paying the ransom, and while appreciating that every case is different, we generally advise not to do it. By handing over the cash, you’re giving the green light to the hackers to carry on doing it. If it works the first time, why not the second or third?
This is the already fraught situation healthcare professionals and departments responsible for day-to-day management of city services find themselves in as we head into February.
February: Slow traffic blues
In February, the Colorado Department of Transportation had to shut down 2,000 (non critical) systems as they, too, were hit by a SamSam outbreak. Bitcoin was once again what the hackers were after; the CDT decided that they weren’t going to pay up, but restore their backups instead.
March: Atlanta ransomware resurgent
All of the worst problems of SamSam effectively rolled into one large pile of misery for the city of Atlanta, who had a serious case of the SamSam blues:
https://platform.twitter.com/widgets.js
They were faced with the prospect of paying $6,800 per machine to unlock the encrypted files, or a cool $51,000 to recover everything across all compromised computers. As to how the attackers got in, one researcher noted a potential EternalBlue route:
https://platform.twitter.com/widgets.js
Regardless of the method used, the big problem here is that 10 days after initial infection, they were still struggling to get back to full strength, with no less than five out of 13 departments hit in the original malware blast. Just like the Indiana hospital staff were forced to use pen and paper, so too were law enforcement in Atlanta—and they also lost some police records in the bargain.
Note that three city council staffers had to work on a “clunky personal laptop.” So now we’re introducing personal machines onto a network dealing with potentially sensitive data, already hammered by opportunistic malware infections. One hopes that the machine had at least been checked for infections or potential vulnerabilities, but it would be surprising if the already busy IT staff checked if the employee had installed all security patches.
You could say the ransom was “only” $51,000—except the ransomware authors pulled the payment page and left Atlanta carrying the can. Ultimately, the SamSam outbreak cost the city of Atlanta a terrifying $2.6 million dollars to set a $50k infection right.
It isn’t just fixing some computers. There’s everything from forensics and insurance to extra staff and crisis comms to consider. This is the very real cost of attempting to recover from an infection—and that’s while trying to offer public-facing services potentially impacted by the attack.
Fighting ransomware
Ransomware may be experiencing a drop in popularity but make no mistake—the impact can be horrendous. As a reminder, here are some ways local governments and other organizations can fend off these attacks:
- Backups are essential, and help to reduce some of the impact from a ransomware attack. A word of caution: your backups have to be logical and easy to implement if needed. All too often, organizations throw everything into a jumble of files and folders, with duplication galore and no real instructions as to where everything should go.
- Staff training. It’s arguable that the automated systems in place should stop attacks long before reaching the human component of your network, but giving staff a crash course in security basics is always a good idea.
- Spam filtering for email-based attacks (fake PDF invoices, booby-trapped Word documents insisting you enable Macros and the like).
- Disable unnecessary exposed services facing the Internet, a time-honored way in for ransomware infections everywhere.
- Change default/easy-to-guess passwords on all of your systems and services (not just the “important” ones, because ultimately someone will find their way in on the supposedly unimportant ones instead).
- Choose your vendors wisely.
SamSam: not gone, and not forgotten
Money makes the world go round, and for SamSam their currency of choice is Bitcoin. Make no mistake, business is good; they’re estimated to have racked up around $850,000 in profit and they show no sign of slowing down. Consider that their estimated $850k profit is still nowhere near the cost of recovery for the City of Atlanta alone, and then take into account how much cleanup has cost for everyone else affected so far.
No matter your reason for being online, and regardless of which industry you operate in, I think we can all agree warding off an attack such as the ones above should be foremost in your mind when allocating a budget to security threats. SamSam isn’t going away anytime soon, and unfortunately the same can be said for other infections waiting to strike. It only takes one moment of inattentiveness, and you could be faced with some difficult decisions indeed.
Thanks to Marcelo for screenshots and additional information.










