The new season of the incredibly popular video game Fortnite is upon us, and so too are the scams. It’s no surprise that con artists would jump on this bandwagon, eager to peddle their fakeouts.
Only this time, scammers had something a little more dangerous in mind than your typical low-level surveys and downloads that never actually materialize. Among all the gluttony of scams there hid a malicious file ready to steal data and enumerate Bitcoin wallets, for starters.
How did we find it? First, we sifted through a sizable mish-mash of free season six passes, supposedly “free” Android versions of Fortnite, which were leaked out from under the developer’s noses, the ever-popular blast of “free V-Bucks” used to purchase additional content in the game, and a lot of bogus cheats, wallhacks, and aimbots.
Here’s the current state of YouTube, for example:
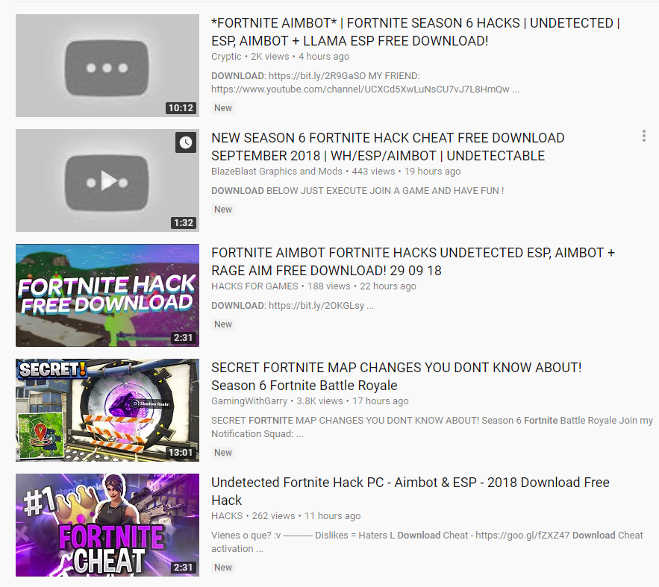
Click to enlarge
These videos can drive huge numbers: Here’s one that’s been pulled down, but managed to rack up 120,000 views before the hammer fell:
Click to enlarge
Almost all of the scam tomfoolery followed the typical survey route, as expected. But buried in all of this was a nasty little slice of data theft malware disguised as a cheat tool.
Offering up a malicious file under the pretense of a cheat is as old school as it gets, but that’s never stopped cybercriminals before. In this scenario, would-be cheaters suffer a taste of their own medicine via a daisy chain of clickthroughs and (eventually) some malware as a parting gift. Shall we take a look?
Setting the scene
The YouTube account offering this scam up has a little over 700 subscribers, and the video in question already had more than 2,200 views the day after being uploaded.
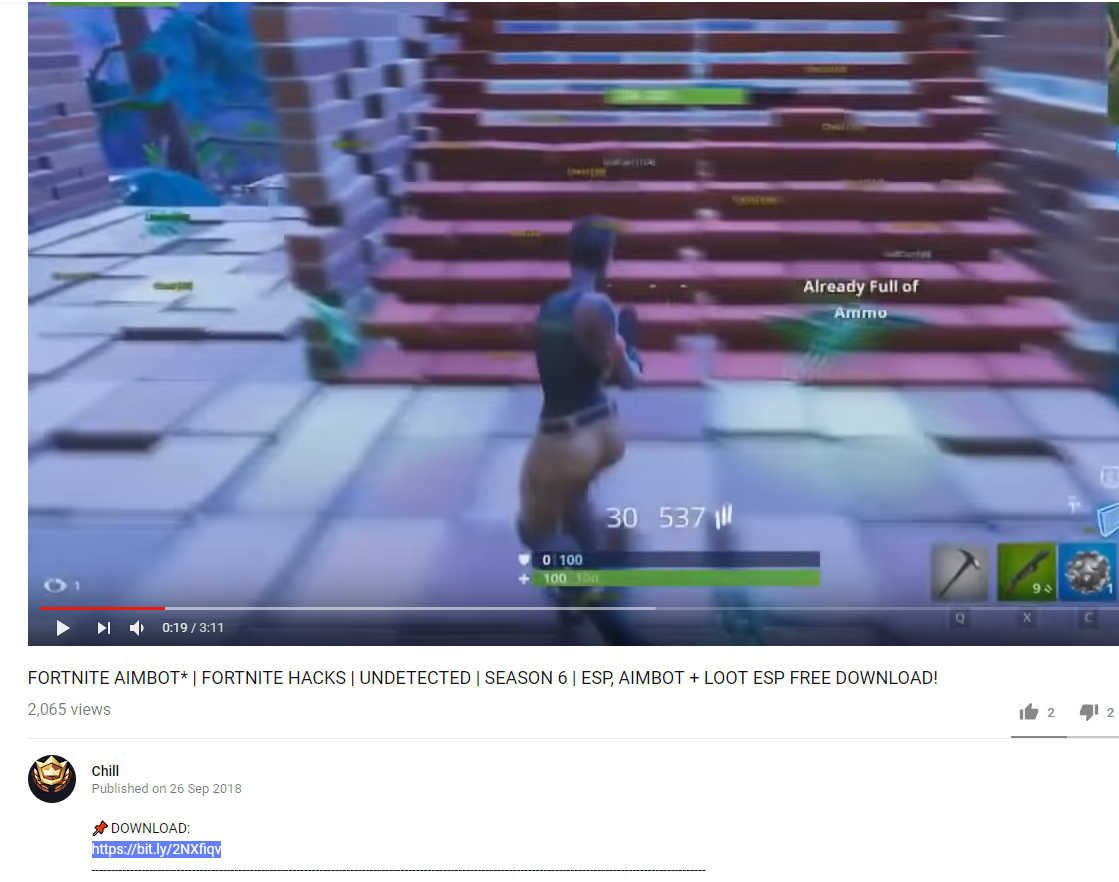
Click to enlarge
Clicking the link sends potential victims to a page on Sub2Unlock. This site differs from typical survey pages, where you’d normally click offers or fill in questions to obtain a theoretical reward. Instead, it asks you to hit subscribe on the social portal of the person sending you there in the first place. So there’s one difference, right off the bat.
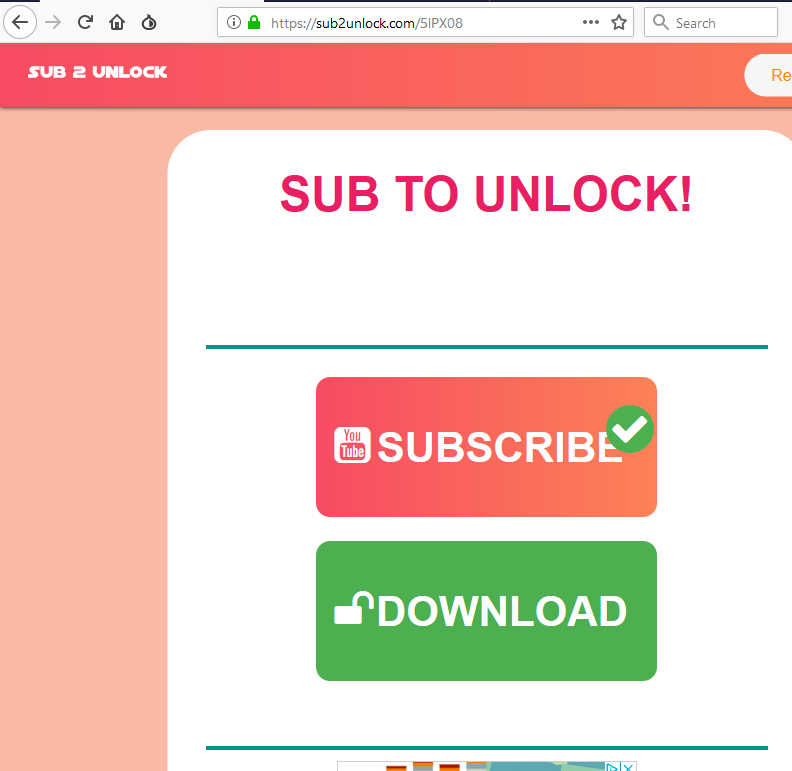
Click to enlarge
Another interesting difference is that any initial survey page requires you to physically complete a survey before progressing. Without doing this, you can’t gain access to a download link.
Here, we had no validation taking place during our testing. Clicking the subscribe button simply opened up the YouTube channel’s subscribe page but nothing checked to ensure we’d actually subscribed. All we had to do at this point was go back to the Sub2Unlock site and click the download button.
From here, gamers are whisked away to a site located at
bt-fortnite-cheats(dot)tk
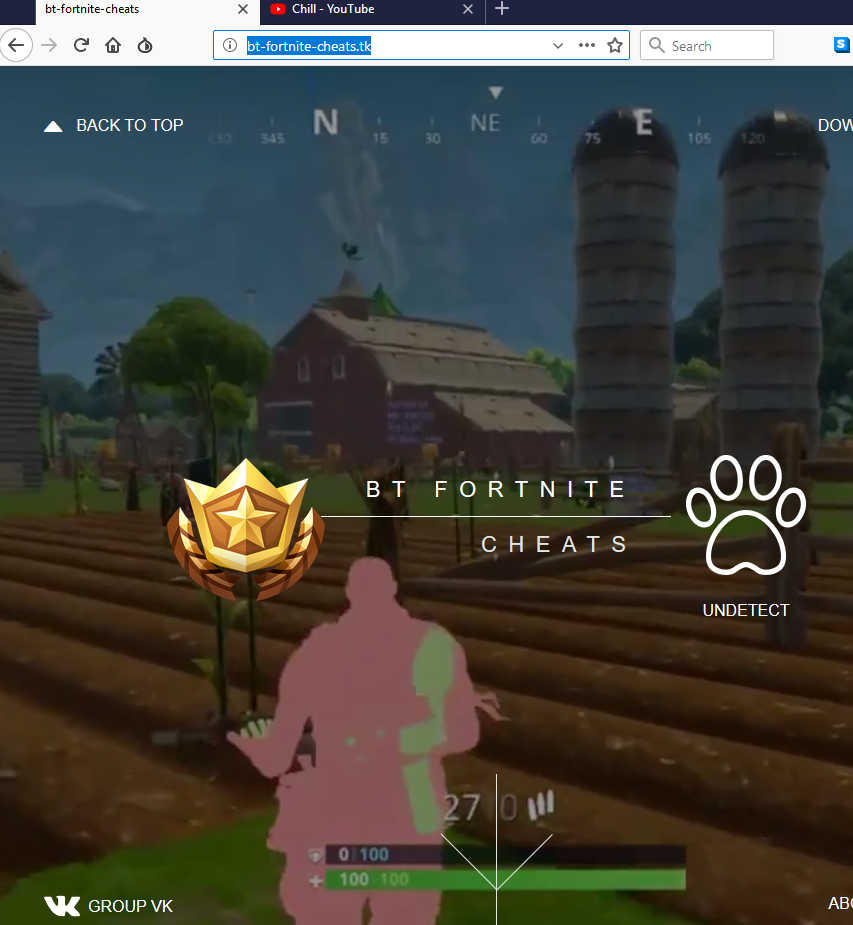
Click to enlarge
This site is a fairly good-looking portal claiming to offer up the desired cheat tools, and it stands a fair chance of convincing youngsters of its legitimacy. A little bit more button clicking, and potential victims are taken to a more general download site containing what appears to be an awful lot of files alongside a wide range of adverts.
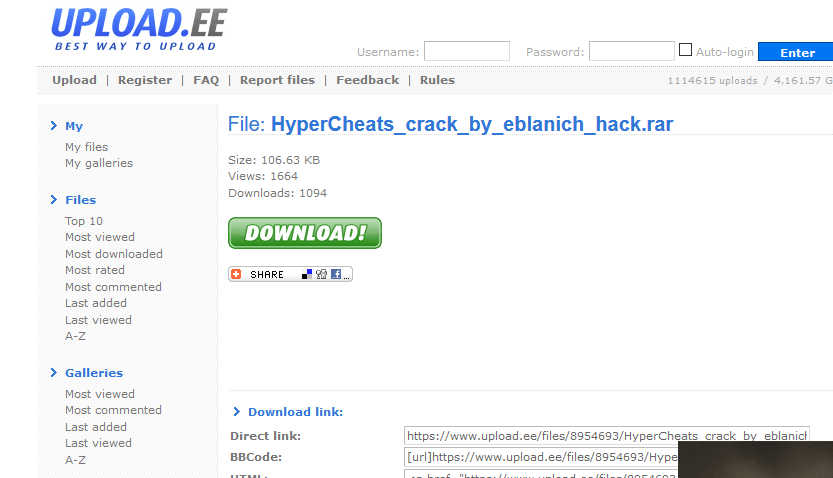
Click to enlarge
As far as the malicious file in question goes, at time of writing, 1,207 downloads had taken place. That’s 1,207 downloads too many.
File information
Malwarebytes detects this file as Trojan.Malpack, a generic detection given to files packed suspiciously. The actual payload could be anything at all, but it will invariably be up to no good. In this case, a little digging showed us the payload is a data stealer.
Once the initial .EXE (which weighs in at just 168KB) runs on the target system, it performs some basic enumeration on details specific to the infected computer. It then attempts to send data via a POST command to an /index.php file in the Russian Federation, courtesy of the IP address 5(dot)101(dot)78(dot)169.
Some of the most notable things it takes an interest in are browser session information, cookies, Bitcoin wallets, and also Steam sessions.
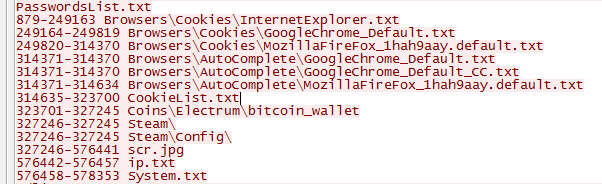
Click to enlarge
Bizarrely, it also wrote this to our test system:
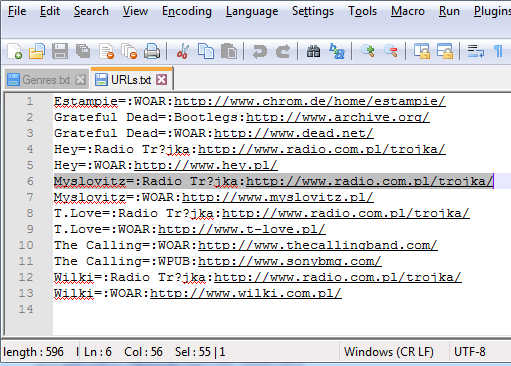
Click to enlarge
…Grateful Dead, anyone?
The IP address up above has been seen many times in relation to similarly named/themed files.
Lots of the files we’ve seen similar to this one are packed in entirely different ways. One of them has a process called “Stealer.exe.” Many more post the stolen information to /gate.php instead of index.php, which is a common sign of Zbot and a few others.
While the subject of this blog probably isn’t that new, it’s still going to do a fair bit of damage to anyone that runs it. Combining it with the current fever for new Fortnite content is a recipe for stolen data and a lot of cleanup required afterward.
As a final note, we should mention the readme file accompanying the stealer advertises being able to purchase additional Fortnite cheats for “$80 Bitcoin.”
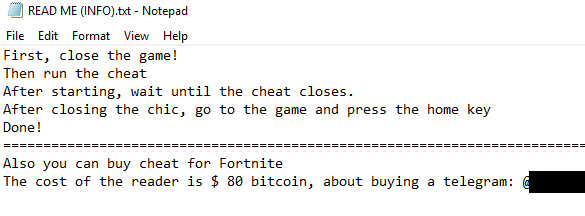
Click to enlarge
Given how things up above panned out, we’d advise anyone tempted to cheat to steer well clear of this one. Winning is great, but it’s absolutely not worth risking a huge slice of personal information to get the job done.










