Ransomware continues to show signs of evolution. From a simple screen locker to a highly-sophisticated data locker, ransomware has now become a mainstream name, even if (historically), it has been around far longer than we want to look back.
Although the criminals behind ransomware campaigns are observed to be refining their approaches—from the “spray and pray” tactic to something akin to wide beam laser precision—they are also fine-tuning their targets. They can single out organizations, companies, and industries; and they can also hold cities and towns for ransom.
Ransomware has also stepped up in sophistication. Criminals have begun introducing certain forms of hybridization in their attacks, either the ransomware file itself is given capabilities outside of its type (e.g., VirRansom and Zcrypt variants that can infect files) or the entire campaign involves one or more threat vectors.
The latest in-the-wild ransomware strain discovered by a group of security researchers known as MalwareHunterTeam (MHT, for short) fits the latter.
Ransomware + phishing: a match made in heaven?
Nothing much is known about this ransomware—which some are already dubbing as CryTekk—apart from the way it applies a wily social engineering tactic to its ransom note, potentially to ensure a near 100 percent of affected parties acting on the infection and paying the ransom. The lure? An additional payment option for affected users who want to retrieve their files but don’t have a cryptocurrency wallet.
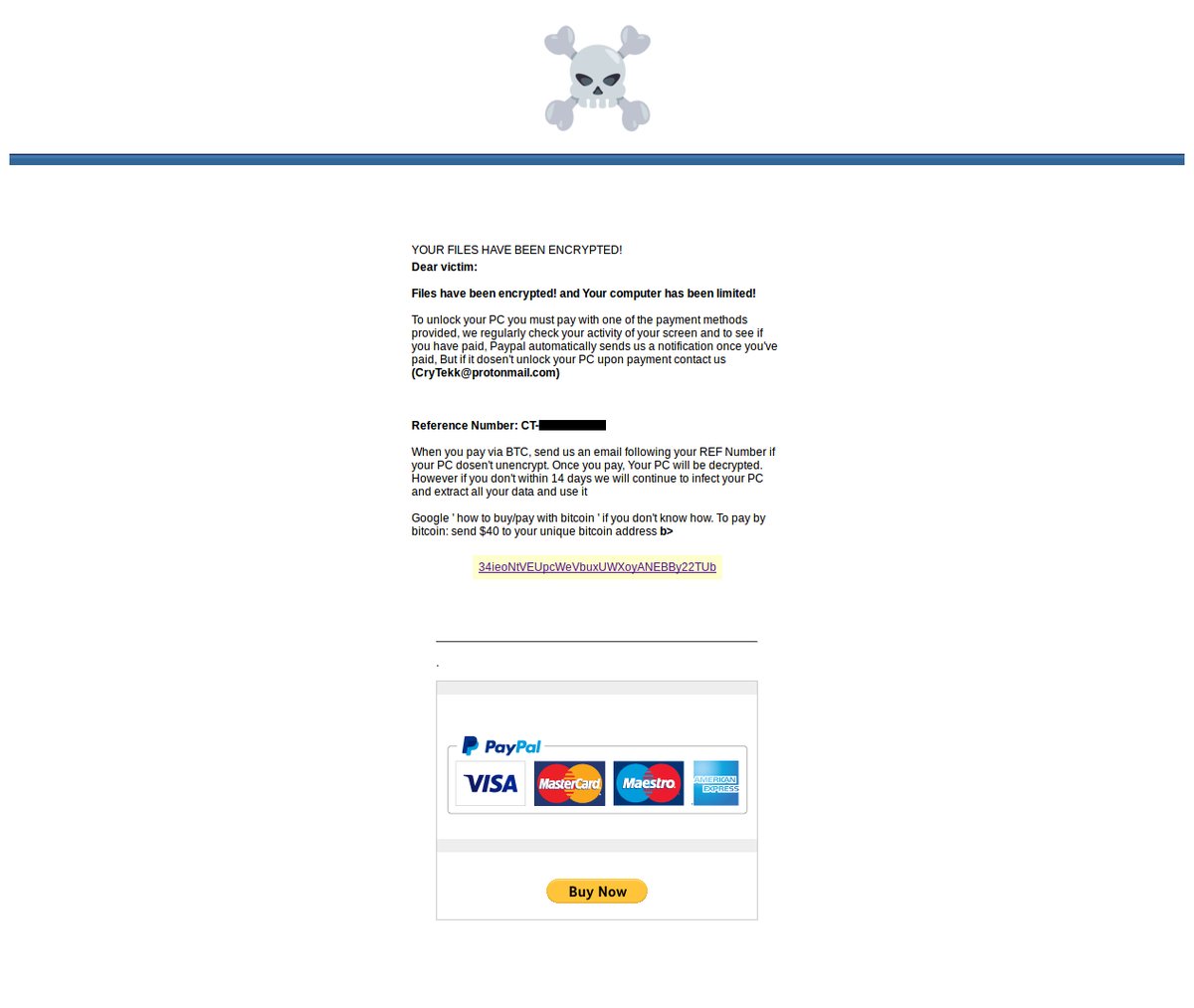
Transcription:
YOUR FILES HAVE BEEN ENCRYPTED!Dear victim:
Files have been encrypted! And Your computer has been limited!
To unlock your PC you must pay with one of the payment methods provided, we regularly check your activity of your screen and to see if you have paid. Paypal automatically sends us a notification once you’ve paid, But if it doesn’t unlock your PC upon payment contact us (CryTekk@protonmail.com)
Reference Number: CT-{redacted}
When you pay via BTC, send us an email following your REF Number if your PC doesn’t unencrypt. Once you pay, Your PC will de decrypted. However if you don’t within 14 days we will continue to infect your PC and extract all your data and use it.
Google ‘how to buy/pay with bitcoin’ if you don’t know how. To pay by bitcoin: send $40 to your unique bitcoin address.
34ieoNtVEUpcWeVbuxUWXoyANEBBy22TUb
Clicking the yellow “Buy now” button in the small PayPal option box opens a browser tab to direct users to a phishing page asking for card details:
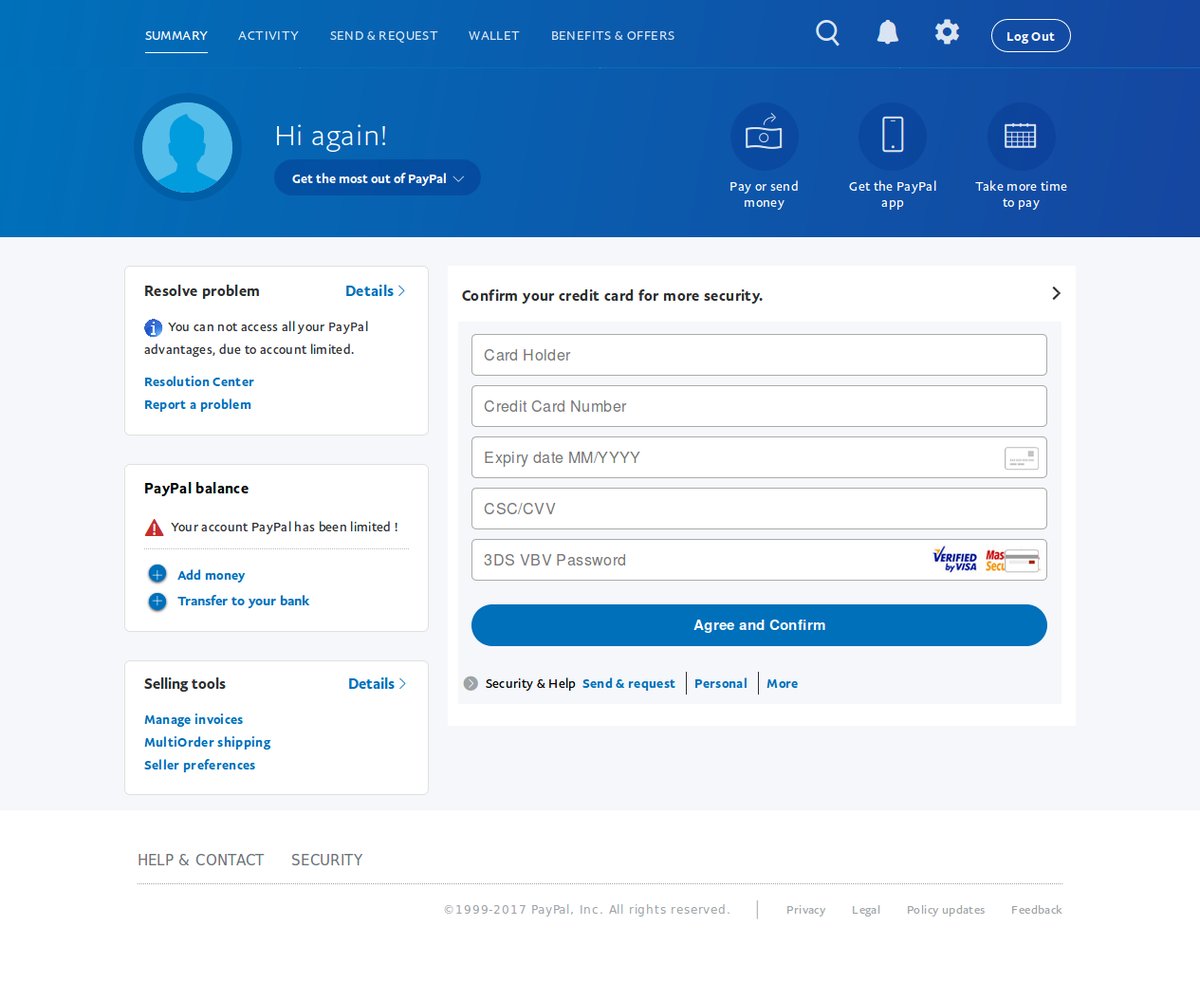
After supplying the information wanted and clicking the “Agree and Confirm” button, users are then directed to another phishing page asking for personal information, which they need to fill in to “confirm” their identities:
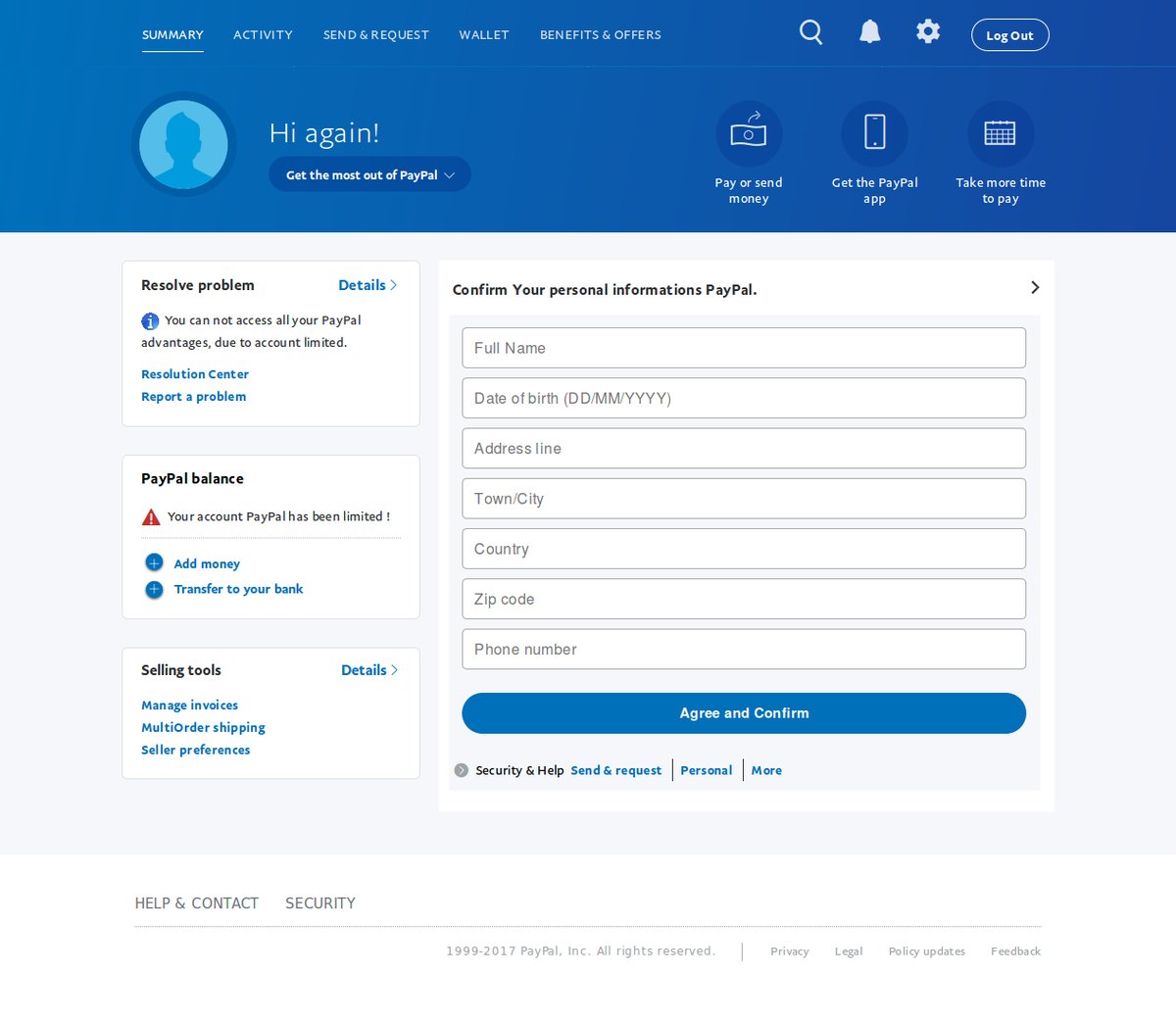
After filling in all information, clicking the “Agree and Confirm” button points users to a fake confirmation that the user’s account access is fully restored, which is odd because, as far as the user knows, they were paying the ransom, not addressing a problem about their PayPal accounts. Now, if the user hadn’t already realized that they had been duped twice, at this point they might.
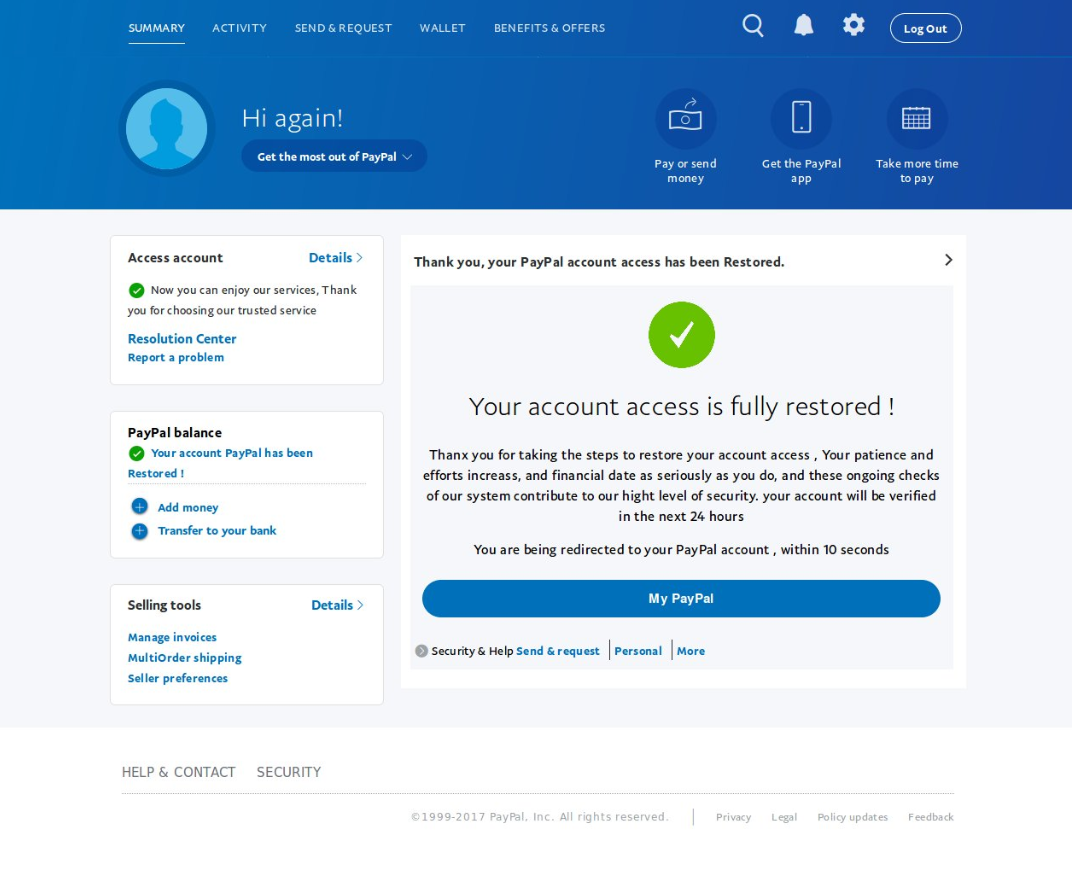
Finally, clicking the “My PayPal” button directs users to the legitimate PayPal login page.
Fool me once, shame on me. Fool me twice…
While ransomware is not as rampant today compared to two years ago, it remains a top threat to consumers and businesses alike. It wouldn’t surprise us at all if the real intent of the criminals behind this campaign is to bank on people’s fear of ransomware to go after their money and credentials.
Files encrypted by this ransomware can be decrypted, as confirmed by MHT’s own Michael Gillespie in a tweet. In fact, within two hours after the initial MHT tweet, Gillespie already offered to decrypt files for possible victims. This confirms what Bleeping Computer stated about the ransomware code being “nothing special.” This also suggests that the criminals put greater effort into the phishing side of the campaign than to the ransomware itself.
Since most, if not all, ransomware attacks ask for cryptocurrency payment, this attack differentiates itself by offering victims an alternative pay first before presenting the Bitcoin payment option. This leads us to speculate that, although they didn’t say it outright, PayPal is their preferred payment method. Also, $40 in Bitcoin in exchange for decrypting files? That’s cheap compared to the amount criminals will be getting from victims once they access their accounts using the swiped credentials.
Regardless of whether we see this as a sophisticated ransomware campaign or a “really dope” attempt at phishing, one thing is clear: They are after your money and credentials, so it pays to know when you’re being phished.
It can be frightening to find oneself face-to-face with a ransomware infection, but let us remain calm and keep our heads together. Remember that criminals want us to feel vulnerable, so be and do the opposite. Scrutinize URLs carefully before you enter your credentials or PII. If you feel that something is amiss, follow your gut and don’t proceed any further. If you think you’re stuck and don’t know what to do next, don’t be afraid to ask for help from someone online or in-person who is savvy enough to guide you.
Stay safe out there!










