Correction, 5/22/19: Previously, we incorrectly stated that Emotet was using an EternalBlue vulnerability in order to spread laterally within a network. However, Emotet only attempts to enumerate network resources and write to share drives, as well as brute force user accounts.
Perhaps what led us (and other researchers) to this conclusion was the fact that TrickBot, a payload we frequently see being loaded by Emotet, makes use of the EternalBlue exploit to spread itself to a domain controller and other Windows clients on the network.
We strongly recommend anyone impacted by Emotet continue to patch for EternalBlue and other related SMB vulnerabilities in order to prevent such lateral malware propagations.
One of the most common and pervasive threats for businesses today is Emotet, a banking Trojan turned downloader that has been on our list of top 10 detections for many months in a row. Emotet, which Malwarebytes detects as Trojan.Emotet, has been leveled at consumers and organizations across the globe, fooling users into infecting endpoints through phishing emails, and then spreading laterally through networks using stolen NSA exploits. Its modular, polymorphic form, and ability to drop multiple, changing payloads have made Emotet a thorn in the side of cybersecurity researchers and IT teams alike.
Emotet first appeared on the scene as a banking Trojan, but its effective combination of persistence and network propagation has turned it into a popular infection mechanism for other forms of malware, such as TrickBot and Ryuk ransomware. It has also earned a reputation as one of the hardest-to-remediate infections once it has infiltrated an organization’s network.
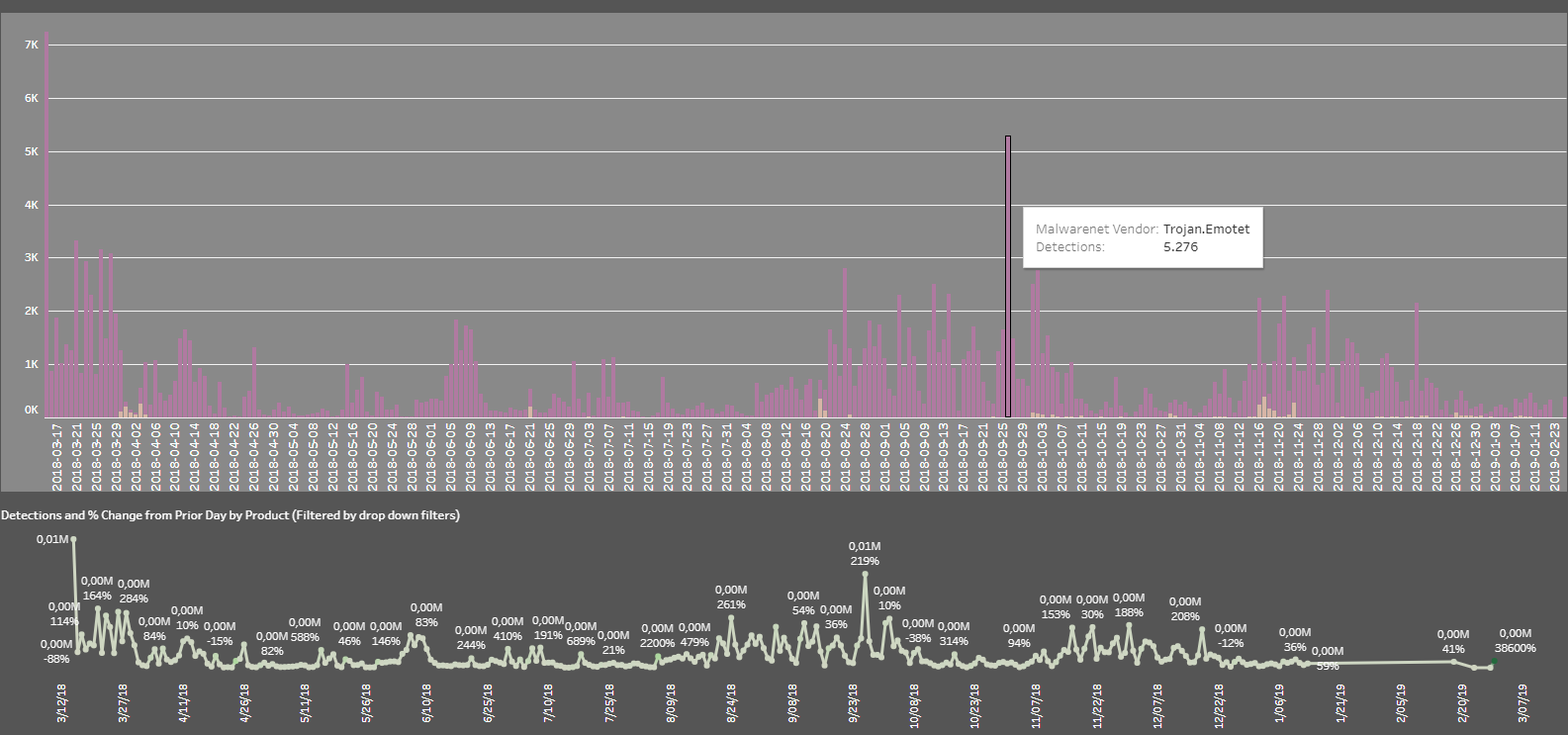
Emotet detections March 12, 2018 – February 23, 2019
In July 2018, the US Department of Homeland Security issued a Technical Alert through CISA (Cyber-Infrastructure) about Emotet, warning that:
“Emotet continues to be among the most costly and destructive malware affecting SLTT governments. Its worm-like features result in rapidly spreading network-wide infection, which are difficult to combat. Emotet infections have cost SLTT governments up to $1 million per incident to remediate.”
From banking Trojan to botnet
Emotet started out in 2014 as an information-stealing banking Trojan that scoured sensitive financial information from infected systems (which is the reason why Malwarebytes detects some components as Spyware.Emotet). However, over time Emotet and its business model evolved, switching from a singular threat leveled at specific targets to a botnet that distributes multiple malware payloads to industry verticals ranging from governments to schools.
Emotet was designed to be modular, with each module having a designated task. One of its modules is a Trojan downloader that downloads and runs additional malware. At first, Emotet started delivering other banking Trojans on the side. However, its modular design made it easier for its authors—a group called Mealybug—to adapt the malware or swap functionality between variants. Later versions began dropping newer and more sophisticated payloads that held files for ransom, stole personally identifiable information (PII), spammed other users with phishing emails, and even cleaned out cryptocurrency wallets. All of these sidekicks were happy and eager to make use of the stubborn nature of this threat.
Infection mechanism
We have discussed some of the structure and flow of Emotet’s infection vectors in detail here and here by decoding an example. What most Emotet variants have in common is that the initial infection mechanism is malspam. At first, infections were initiated from Javascript files attached to emails; later, (and still true today) it was via infected Word documents that downloaded and executed the payload.
A considerable portion of Emotet malspam is generated by the malware’s own spam module that sends out malicious emails to the contacts it finds on an infected system. This makes the emails appear as though they’re coming from a known sender. Recipients of email from a known contact are more likely to open the attachment and become the next victim—a classic social engineering technique.
Besides spamming other endpoints, Emotet also propagates through the popular EternalBlue vulnerability stolen from the NSA and released by the ShadowBrokers Group. This functionality allows the infection to spread laterally across a network of unpatched systems, which makes it even more dangerous to businesses that have hundreds or thousands of endpoints linked together.
Difficult to detect and remove
Emotet has several methods for maintaining persistence, including auto-start registry keys and services, and it uses modular Dynamic Link Libraries (DLLs) to continuously evolve. Because Emotet is polymorphic and modular, it can evade typical signature-based detection.
In fact, not only is Emotet difficult to detect, but also to remediate.
A major factor that frustrates remediation is the aforementioned lateral movement via EternalBlue. This particular exploit requires admins follow a strict policy of isolating infected endpoints from the network, patching, disabling Administrative Shares, and ultimately removing the Trojan before reconnecting to the network—otherwise, face the certainty that cleaned endpoints will become re-infected over and over by infected peers.
Add to that mix an ongoing development of new capabilities, including the ability to be VM-aware, avoid spam filters, or uninstall security programs, and you’ll begin to understand why Emotet is every networks administrators’ worst nightmare.
Recommended remediation steps
An effective, though time-consuming method for disinfecting networked systems has been established. The recommended steps for remediation are as follows:
- Identify the infected systems by looking for Indicators of Compromise (IOCs)
- Disconnect the infected endpoints from the network. Treat systems where you have even the slightest doubt as infected.
- Patch the system for EternalBlue. Patches for many Windows versions can be found through this Microsoft Security Bulletin about MS17-010.
- Disable administrative shares, because Emotet also spreads itself over the network through default admin shares. TrickBot, one of Emotet’s trusty sidekicks, also uses the Admin$ shares once it has brute forced the local administrator password. A file share server has an IPC$ share that TrickBot queries to get a list of all endpoints that connect to it.
- Scan the system and clean the Emotet infection.
- Change account credentials, including all local and domain administrator passwords, as well as passwords for email accounts to stop the system from being accessible to the Trojan.
Prevention
Obviously, it’s preferable for businesses to avoid Emotet infections in the first place, as remediation is often costly and time-consuming. Here are some things you can do to prevent getting infected with Emotet:
- Educate users: Make sure end users are aware of the dangers of Emotet and know how to recognize malspam—its primary infection vector. Train users on how to detect phishing attempts, especially those that are spoofed or more sophisticated than, say, the Nigerian Prince.
- Update software regularly: Applying the latest updates and patches reduces the chances of Emotet infections spreading laterally through networks via EternalBlue vulnerabilities. If not already implemented, consider automating those updates.
- Limit administrative shares: to the absolute minimum for Emotet damage control.
- Use safe passwords: Yes, it really is that important to use unique, strong passwords for each online account. Investigate, adopt, and role out a single password manager for all of the organization’s users.
- Back up files: Some variants of Emotet also download ransomware, which can hold now-encrypted files hostage, rendering them useless unless a ransom is paid. Since we and the FBI recommend never paying the ransom—as it simply finances future attacks and paints a target on an organization’s back—having recent and easy-to-deploy backups is always a good idea.
IOCs
Persistence
C:WindowsSystem32randomnumber C:WindowsSystem32tasksrandomname C:Windows[randomname] C:users[myusers]appdataroaming[random] %appdata%RoamingMicrosoftWindowsStart MenuProgramsStartup [Randomname].LNK. file in the startup folder
Registry keys
HKEY_LOCAL_MACHINESystemCurrentControlSetServices {Random Hexadecimal Numbers} HKEY_CURRENT_USERSOFTWAREMicrosoftWindowsCurrentVersionRun {Random Names} with value c:usersadminappdataroaming{Random}{Legitimate Filename}.exe
Filename examples
PlayingonaHash.exe certapp.exe CleanToast.exe CciAllow.exe RulerRuler.exe connectmrm.exe
Strings
C:email.doc C:123email.doc C:123email.docx C:afoobar.bmp X:Symbolsa C:loaddll.exe C:email.htm C:take_screenshot.ps1 C:afoobar.gif C:afoobar.doc
Subject Filters
“UPS Ship Notification, Tracking Number” “UPS Express Domestic” “Tracking Number *”
Trick to check whether a UPS tracking number is real: a legitimate UPS tracking number contains eighteen alpha-numeric characters and starts with ‘1Z’ and ends with a check digit.
A number matching this format may still be false, but one that doesn’t match is certainly not real.