By Jérôme Segura, Adam Thomas, and S!Ri
We have been closely monitoring the situation involving the continued attacks against users of the popular Electrum Bitcoin wallet. Initially, victims were being tricked to download a fraudulent update that stole their cryptocurrencies. Later on, the threat actors launched a series of Distributed Denial of Service (DDoS) attacks in response to Electrum developers trying to protect their users.
Since our last blog, the amount of stolen funds has increased to USD $4.6 million, and the botnet that is flooding the Electrum infrastructure is rapidly growing. Case in point, on April 24, the number of infected machines in the botnet was just below 100,000 and the next day it reached its highest at 152,000, according to this online tracker. Since then, it has gone up and down and plateaued at around the 100,000 mark.
New loader identified
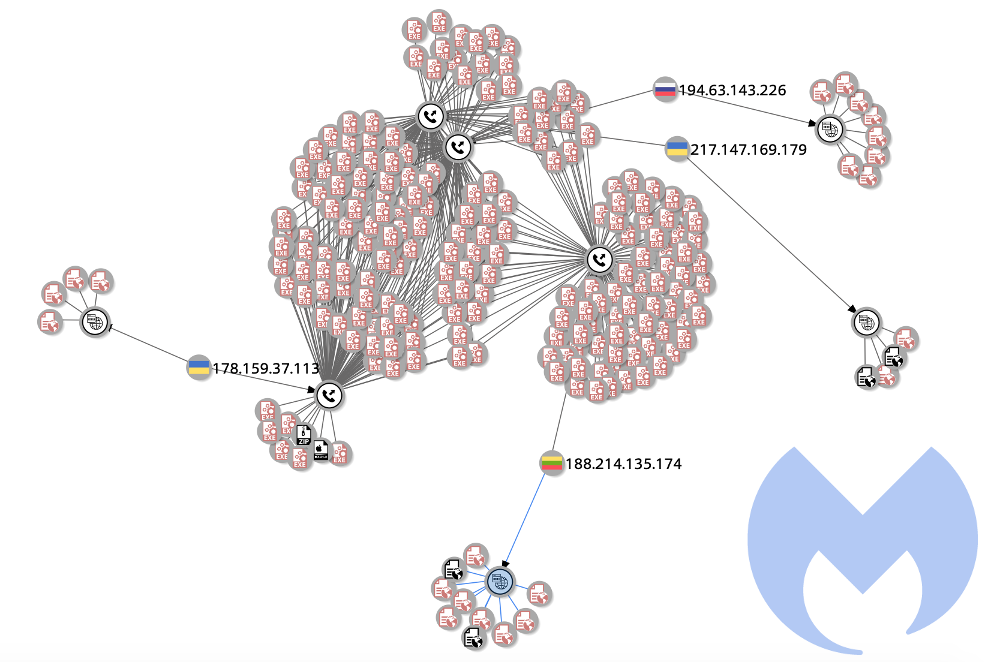
We have been able to correlate two distribution campaigns (RIG exploit kit and Smoke Loader) that are fueling this botnet by dropping malware we detect as ElectrumDoSMiner. Now, we have just identified a previously undocumented loader we call Trojan.BeamWinHTTP that is also involved in downloading ElectrumDoSMiner (transactionservices.exe).
As can be seen in the VirusTotal graphs above and below, there are hundreds of malicious binaries that retrieve the ElectrumDoSMiner. We surmise there are probably many more infection vectors beyond the three we’ve uncovered so far.
An underreported and yet massively fraudulent scheme
Crooks wasted no time in exploiting a vulnerability in Electrum wallets to phish unsuspecting users. What followed next with retribution attacks on Electrum servers was unexpected but logical, considering what is at stake.
While these DDoS attacks have not been publicized much by mainstream media, they have undoubtedly caused millions of dollars in losses over the span of just a few months.
Indicators of Compromise
ElectrumDoSMiner infrastructure
178.159.37.113
194.63.143.226
217.147.169.179
188.214.135.174
Trojan.BeamWinHTTP
48dcb183ff97a05fd3e466f76f385543480abb62c9adcae24d1bdbbfc26f9e5a
Hashes for the binaries tied to the ElectrumDoSMiner infrastructure can be downloaded here.
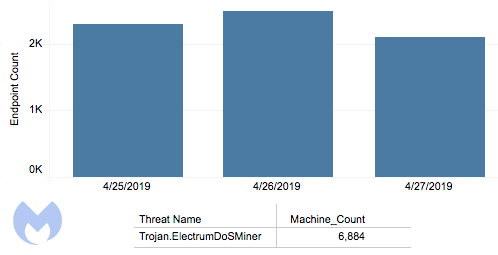
The number of victims that are part of this botnet is constantly changing. We believe as some machines get cleaned up, new ones are getting infected and joining the others to perform DoS attacks. Malwarebytes detects and removes ElectrumDoSMiner infections on more than 2,000 endpoints daily.

An underreported and yet massively fraudulent scheme
Crooks wasted no time in exploiting a vulnerability in Electrum wallets to phish unsuspecting users. What followed next with retribution attacks on Electrum servers was unexpected but logical, considering what is at stake.
While these DDoS attacks have not been publicized much by mainstream media, they have undoubtedly caused millions of dollars in losses over the span of just a few months.
Indicators of Compromise
ElectrumDoSMiner infrastructure
178.159.37.113
194.63.143.226
217.147.169.179
188.214.135.174
Trojan.BeamWinHTTP
48dcb183ff97a05fd3e466f76f385543480abb62c9adcae24d1bdbbfc26f9e5a
Hashes for the binaries tied to the ElectrumDoSMiner infrastructure can be downloaded here.
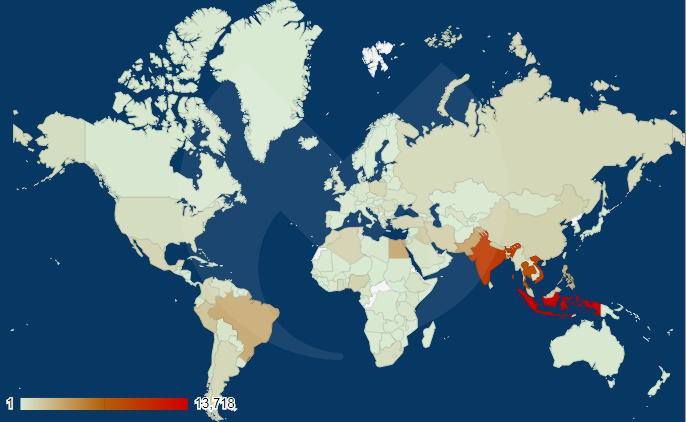
Botnet geographic distribution
By analyzing the IP addresses and mapping them to a country, we are able to have a better idea of where the bots are located. We find the largest concentration in the Asia Pacific region (APAC). For the Americas, most bots are located in Brazil and Peru.

The number of victims that are part of this botnet is constantly changing. We believe as some machines get cleaned up, new ones are getting infected and joining the others to perform DoS attacks. Malwarebytes detects and removes ElectrumDoSMiner infections on more than 2,000 endpoints daily.

An underreported and yet massively fraudulent scheme
Crooks wasted no time in exploiting a vulnerability in Electrum wallets to phish unsuspecting users. What followed next with retribution attacks on Electrum servers was unexpected but logical, considering what is at stake.
While these DDoS attacks have not been publicized much by mainstream media, they have undoubtedly caused millions of dollars in losses over the span of just a few months.
Indicators of Compromise
ElectrumDoSMiner infrastructure
178.159.37.113
194.63.143.226
217.147.169.179
188.214.135.174
Trojan.BeamWinHTTP
48dcb183ff97a05fd3e466f76f385543480abb62c9adcae24d1bdbbfc26f9e5a
Hashes for the binaries tied to the ElectrumDoSMiner infrastructure can be downloaded here.










