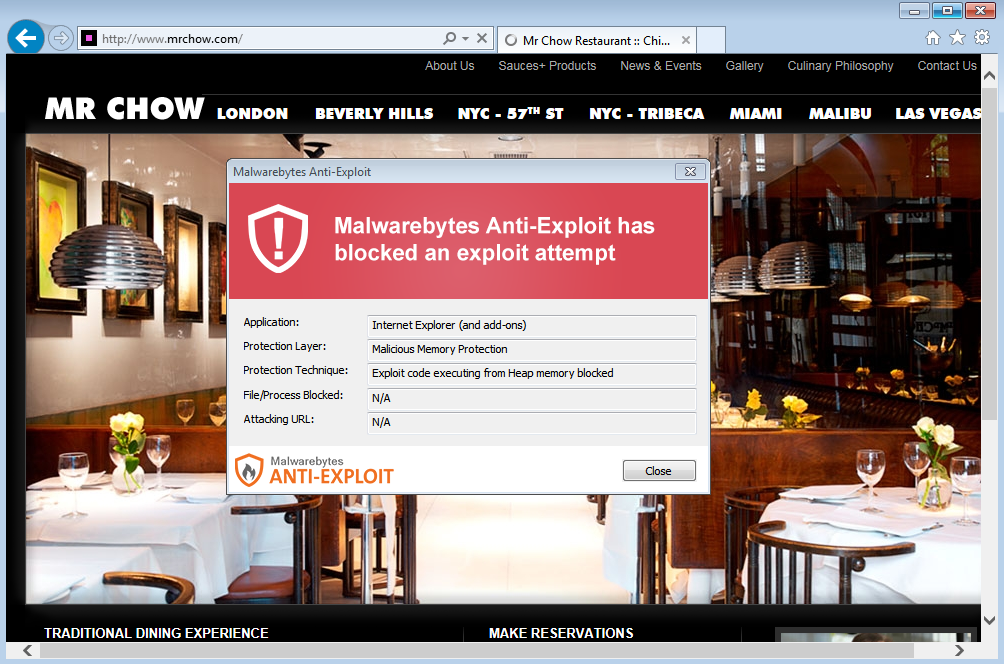
The website for popular fine Chinese cuisine “Mr Chow” restaurants has been hacked and is redirecting visitors to ransomware. This is not the first high profile culinary personality that has been involved in a security incident. Before Michael Chow, British Chef Jamie Oliver experienced several cases of website compromises himself.
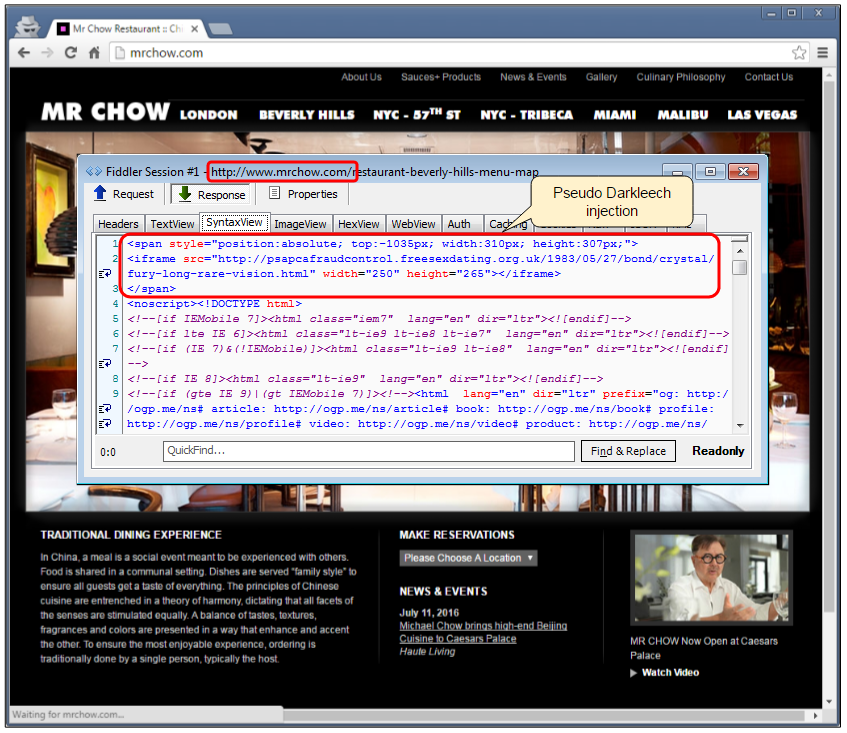
A malicious script (pseudo Darkleech) injected directly into the website’s page is triggering the Neutrino exploit kit and will infect vulnerable systems with ransomware. The majority of website hacks are the result of outdated CMS software (WordPress, Joomla, Drupal, etc). We ran a scan of the site using Sucuri’s SiteCheck and discovered this was the case here as well, with a vulnerable installation of Drupal.
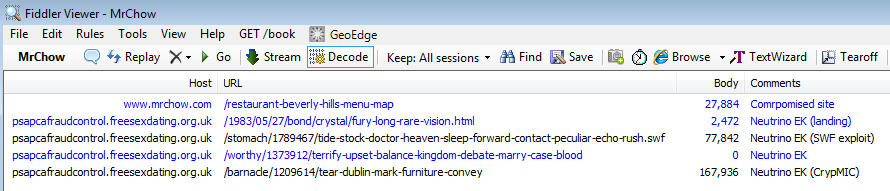
Traffic and exploit overview
There are currently two exploit kits with the lion’s share of compromised websites redirecting to malware: Neutrino EK via the pseudo Darkleech campaign, and RIG EK via the EITest campaign. Here we recognize the pseudo Darkleech pattern, with a simple iframe redirection.
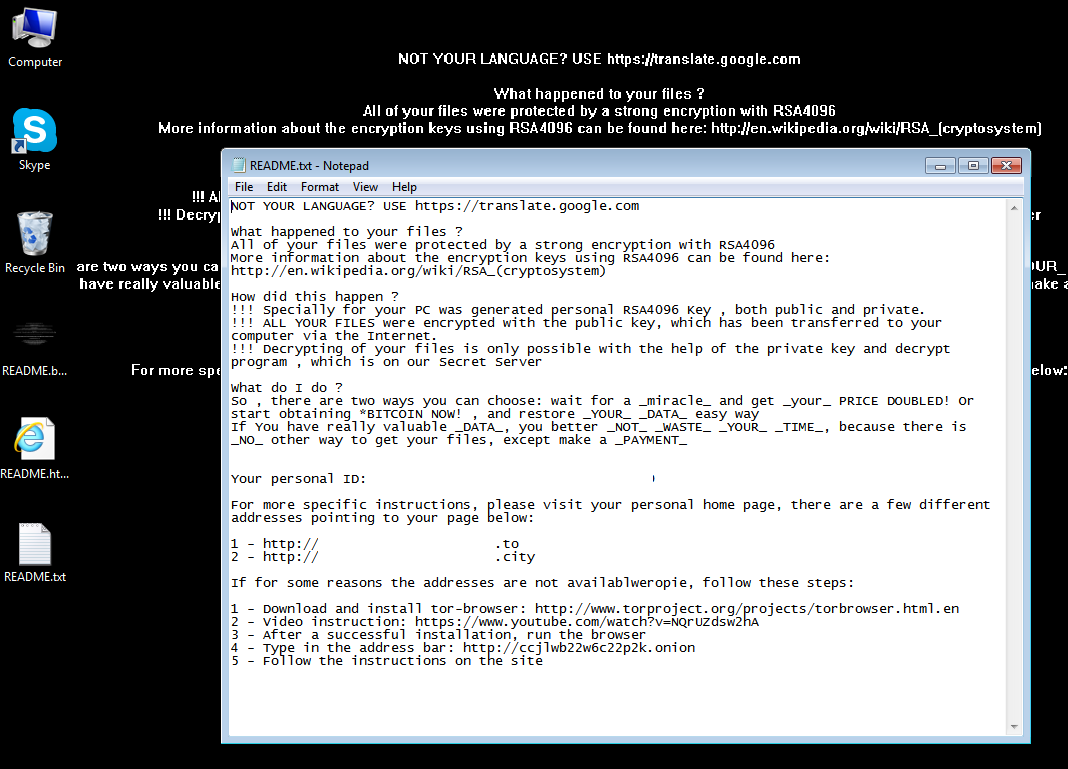
Ransomware
The payload that unsuspecting users will receive is the CrypMIC ransomware which demanded 1.2 BT (roughly $695) at the time of posting.
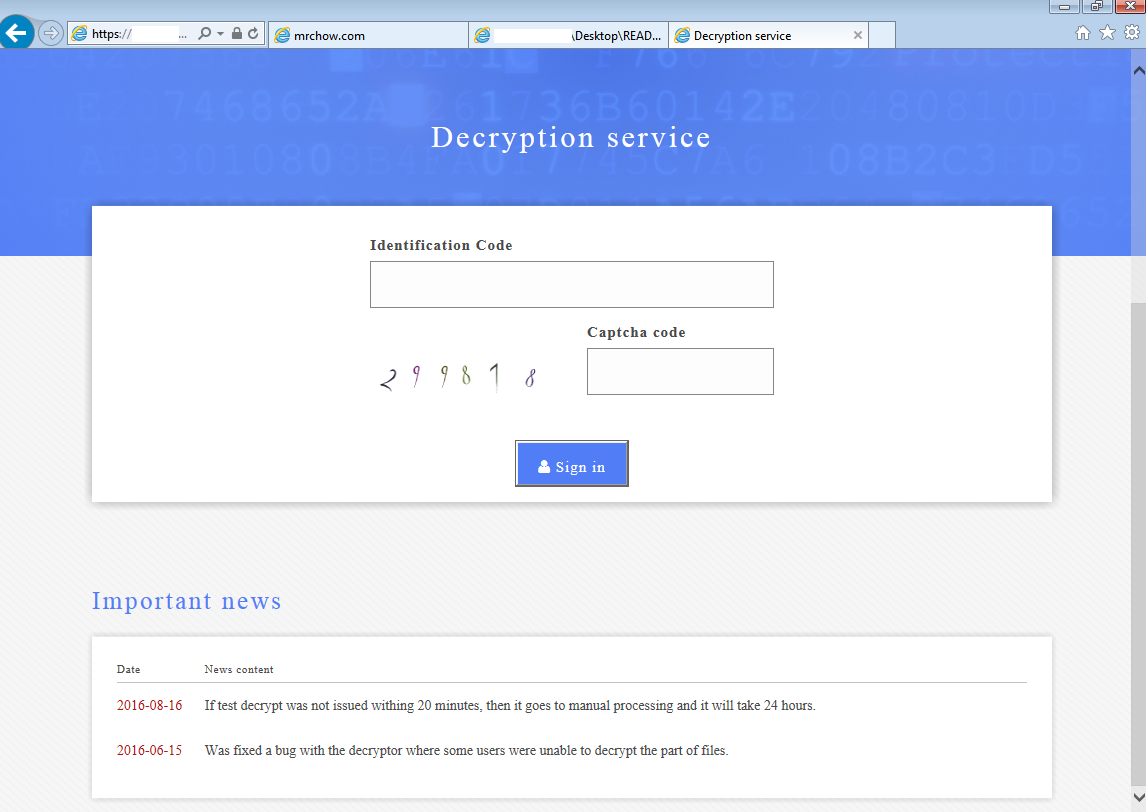
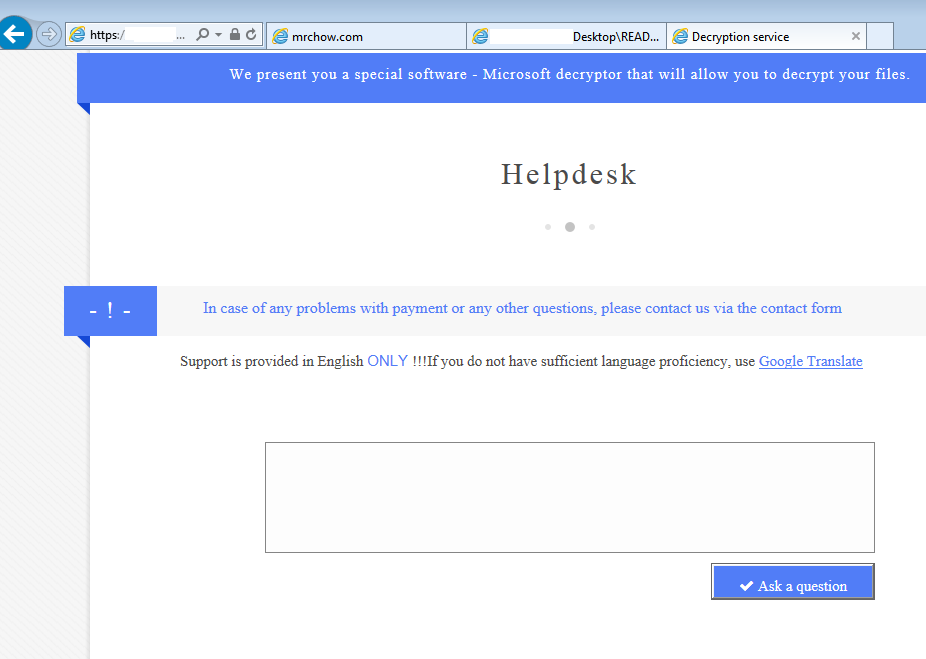
Ransomware authors have been adding new features to make it more robust or more “user-friendly”. Below, we see a CAPTCHA users must enter in order to access their account page with further instructions, and even a “Help Desk” section where you can ask the criminals some questions (or get some feelings off your chest):
Malwarebytes Anti-Exploit users are protected against this attack before the ransomware component is even downloaded.
We have contacted the owner of the website about this incident and will update this article if we receive any response.