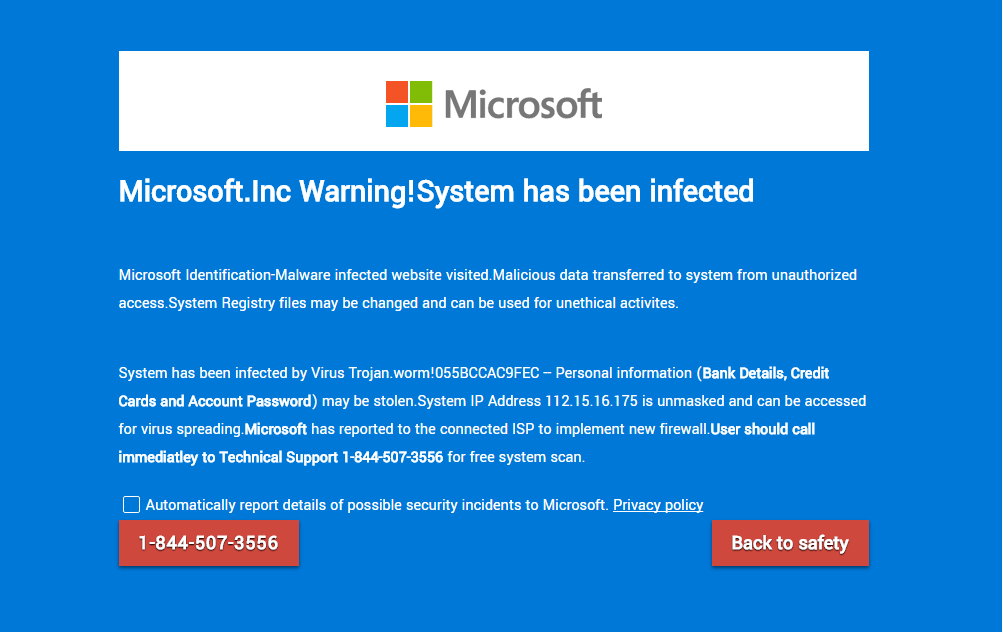
One of the primary vectors for the distribution of tech support scams is malvertising. You’ll simply be browsing the web when all of a sudden your browser shows a scary page claiming your computer is infected. Behind the scenes, an unscrupulous ad network usually lets a malicious actor push a malicious code snippet instead of a regular advert. Now all you see is a page that looks like a Microsoft website and no matter how many times you try to close the annoying popup, it simply won’t go away.
Over time, various tricks have been used to fool browsers and in particular Google Chrome, which is not surprising considering its market share. Typically we have seen JavaScript code to send what seems to be an infinite number of pop ups, which in reality is a simple loop. Of course there have been variations of this and historically browsers have let users down by not being to handle those tricks cleanly. As of matter of fact, one of the easiest ways to get rid of a browser locker is to kill its process using Task Manager or other such tool.
Today we are looking at yet another technique which isn’t new per se, but has finally made its way into tech support scams. Remember the websites that could crash Chrome/Firefox/Safari even on mobile devices? The flaw was originally identified in July 2014 and it is an abuse of the history.pushState() method introduced with HTML5 which according to the documentation, pushes the given data onto the session history stack with the specified title and, if provided, a URL.
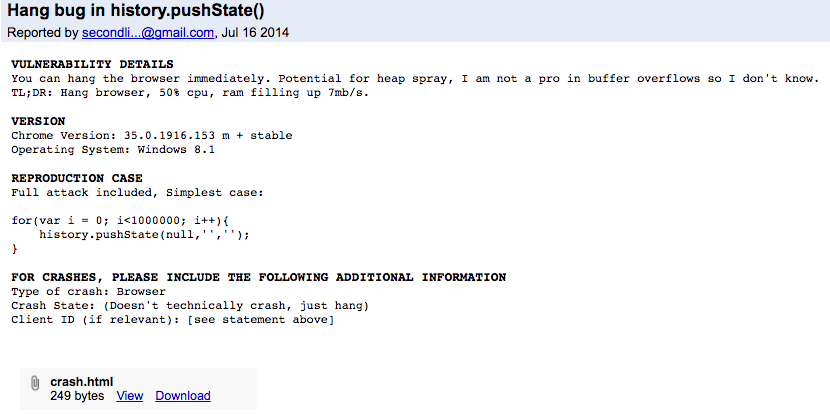
One important thing you may notice from the bug report above is the “Doesn’t technically crash, just hang” part. This is so important because as you will see below, scammers really want their victims to see the instructions on screen, and in particular the phone number to call to fix their computer:
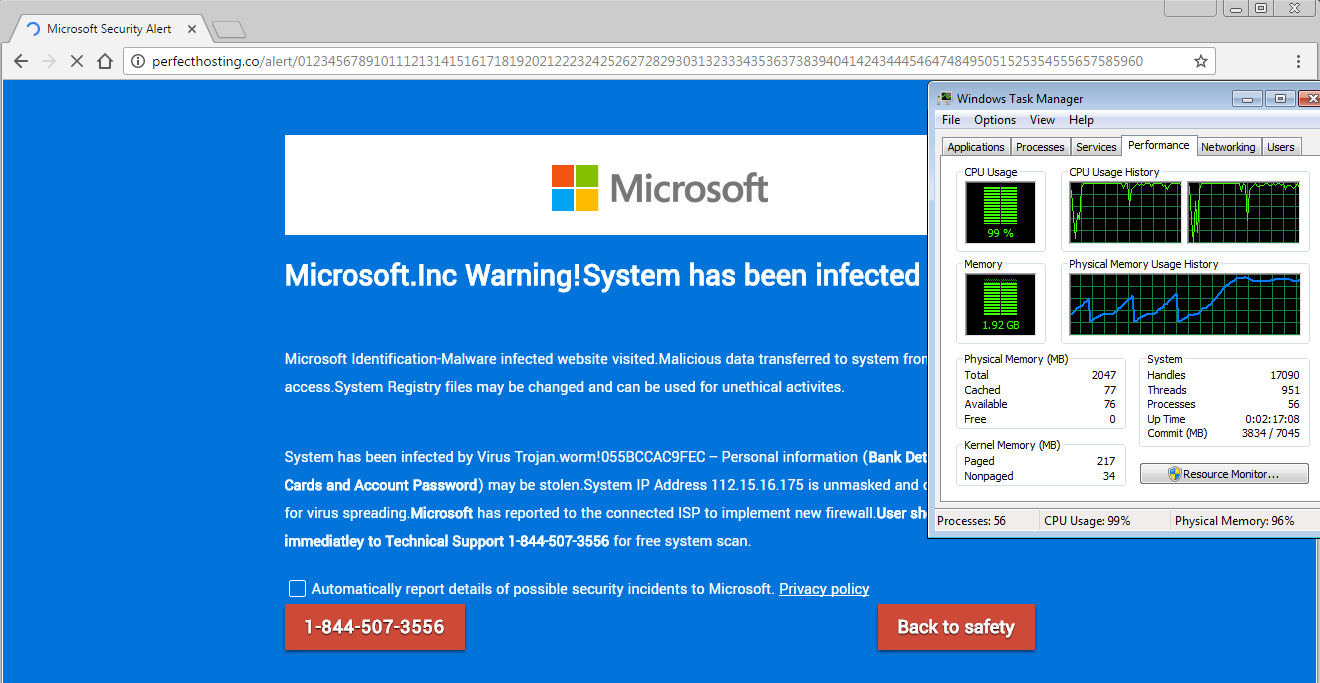
This is a clever use of this bug because the computer that visited this site is essentially stuck with the CPU and memory maxed out while the page is not responding. All of this is done by using a few lines of code:
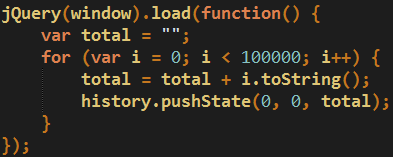
Depending on your computer’s specifications you may or may not be able to launch Task Manager to kill the browser process. Otherwise your system will be brought to its knees and a hard reboot may be the only option left. Whatever you do, please do not call the phone number for support because it is not Microsoft’s but rather a group of scammers waiting to rob you of hundreds of dollars under false pretenses.
We reported this particular scam to the Google Safebrowsing team even though the bug existed before, because the fact it is used in the wild to trick people makes it more urgent to be looked at and fixed.
Hat tip to @TheWack0lian for sharing this new browlock scam with us.
IOCs
- 1-844-507-3556
- perfecthosting[.]co/alert/
- perfecthosting.co/alert/123.mp3
- 79.170.44.106
Microsoft Identification-Malware infected website visited.Malicious data transferred to system from unauthorized access.System Registry files may be changed and can be used for unethical activites.
System has been infected by Virus Trojan.worm!055BCCAC9FEC — Personal information (Bank Details, Credit Cards and Account Password) may be stolen.System IP Address 112.15.16.175 is unmasked and can be accessed for virus spreading.Microsoft has reported to the connected ISP to implement new firewall.User should call immediatley to Technical Support 1-844-507-3556 for free system scan.