After a troubling week for Google not so long ago, the company is under the spotlight once more for missing another app that, after further investigations by several members of Reddit, was found laden with adware.
This app, which was called “Update WhatsApp Messenger,” used the logo and developer name of the real WhatsApp app—two elements that a user familiar with the app expects to see. However, the developer name for this bogus app had an extra space at the end, so it looked like this:
WhatsApp, Inc.{space}
To aid users in realizing this deception, Redditor Megared17 posted snapshots of a code section belonging to the real WhatsApp and the fake app to compare the two. We have reproduced the shots below for your convenience.
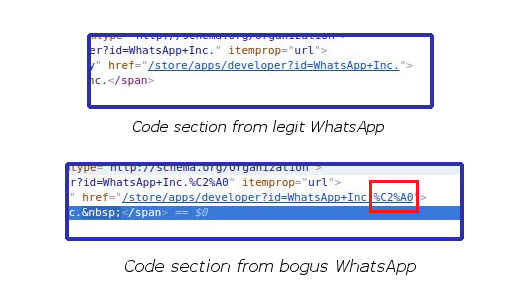
That bit in the box is the percent coding equivalent of a blank space, which translates to U+00A0, the Unicode value of a no-break space. Although this is something our normal eyes may have a difficult time spotting, many decried that Google’s scanner should have quickly picked this up.
Read: Out of character: Homograph attacks explained
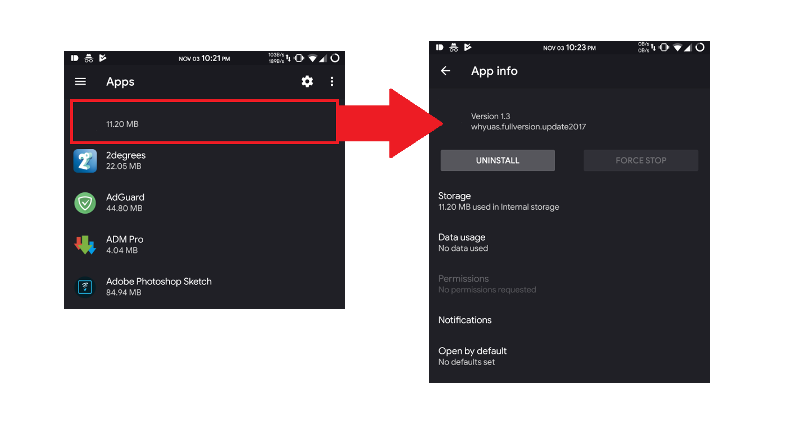
Once downloaded and installed, Redditor Dextersgenius pointed out that “Update WhatsApp Messenger” hid from users by “not having a title and having a blank icon,” which he then supplemented with screenshots that we also reproduced below.
From Dextersgenius’s testing, they also pointed to a piece of code that indicated this bogus app appears to access a hardcoded bit.ly shortened URL that presumably downloads an update APK named whatsapp.apk. Upon closer inspection, however, the bit.ly URL led to another shortened URL—this time Google’s URL shortener, goo.gl—that then led to a Google search result for a WhatsApp Messenger APK file.
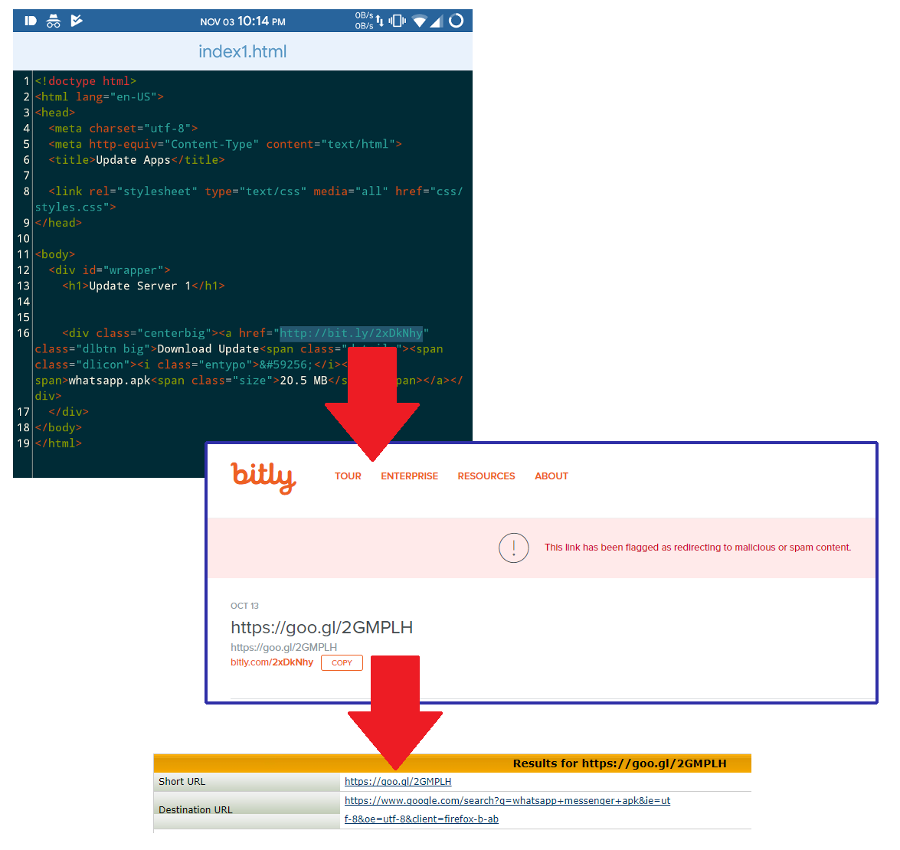
Essentially, users are told to “Look for the APK file from these search results. It’s got to be in one of them!” No updates are sent to the phones at all, so they’re just left with a PUP app.
“Users need to be more vigilant,” advised Armando Orozco, Lead for the Mobile Protection Team at Malwarebytes. “If they want to update WhatsApp, they need to use the update mechanism in the Play Store app, not a secondary app.”
Apart from reading app reviews for any reports of questionable behavior, it also pays for users to check the link to the developer of the app, which might have helped catch “Update WhatsApp Messenger” and possibly lessen the number of affected devices.
Stay safe!
Other related post(s):










