Back in October 2014, we wrote an article about a particular malware campaign we nicknamed ‘EITest’.
The actors behind it were using hacked sites and bogus .us.to subdomains to redirect their victims to the Angler Exploit Kit which finished the job and infected vulnerable machines.
Fast forward a few months and we are back to the same modus operandi, except this time the Nuclear Exploit Kit is the weapon of choice.
What is noteworthy is the crooks are using a recently patched Flash Player vulnerability (a variant of CVE-2015-0336) that affects version 16.0.0.305 and older, released on February 5.
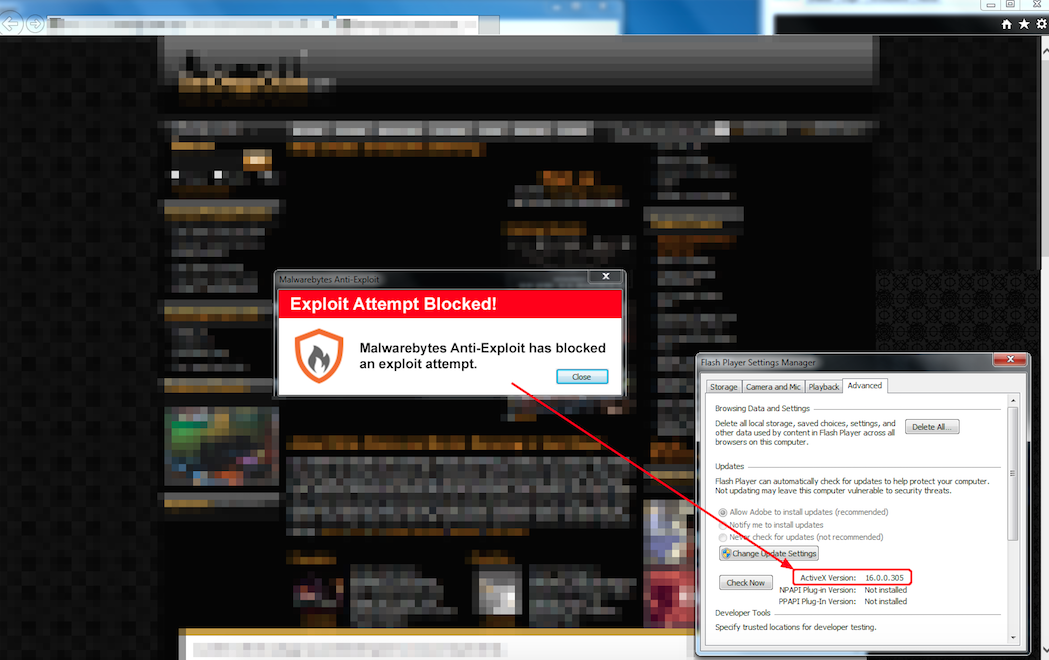
Malwarebytes Anti-Exploit users are already protected against this threat.
The Flash exploit was packed with secureSWF (a legitimate program from Kindi software) to protect it from decompilers and make security researchers’ jobs more interesting. The bad guys simply used the “demo version”, good enough and anonymous.
We immediately reached out to Adobe and they quickly responded:
Adobe has confirmed that a variant of CVE-2015-0336 is being exploited ITW. CVE-2015-0336 was resolved in Flash Player 17.0.0.134 (see APSB15-05).
We updated our Exploit Kit graph to account for CVE-2015-0336 in Nuclear EK:

Network traffic (Nuclear EK)
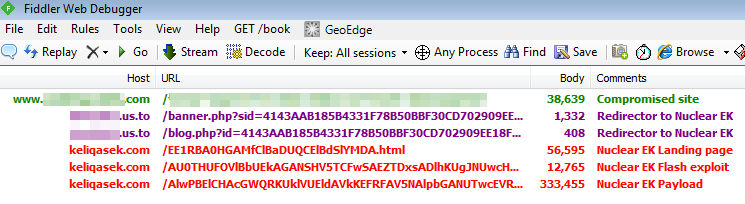
Payload
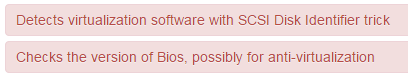
The malware (821c8b01abbb1da4d790aa1bca98c4e4) gets dropped as a .tmp file and performs some anti virtualization detections according to malwr.com
Malwarebytes Anti-Malware detects this threat as Trojan.GenPe3.ED.
This latest adoption of a recently fixed vulnerability is a reminder that patching software should be done on a regular basis.
We know that in some cases consumers but most likely businesses cannot always apply patches right away. Many times they need to do some internal testing to make sure the patch does not break some of their processes.
Such systems should ideally be sandboxed from the rest of the network or be running anti-exploit software designed to block known and unknown exploits.










