Staying safe online requires more than just avoiding websites that look untrustworthy. These days, you might be infected with malware by the advertisement banner showing on a legitimate website, or have your CPU gobbled up by cryptominers.
To counter these kinds of threats, we at Malwarebytes tend to block entire advertiser networks to prevent our users from being a victim of malicious advertisements, or malvertising. Or we might block domains that allow cryptomining to take place without consent.
The purpose of this blog post is to explain exactly why you might see pop-ups from our website blocking function on a site that you thought you trusted.
Malicious sites vs. sites used for malice
There are many reasons why certain websites are blocked, and we make it clear in our product notification pop-ups why we do so. We block and flag sites for being infected or for containing potentially malicious downloads, such as driverupdate.net, which was found to be spreading malware and potentially unwanted programs (PUPs). We also block sites such as gleeze.com and coinhive.com for harboring phishing websites and engaging in malicious cryptomining activities, respectively.
In some cases, website blocking isn’t permanent. This happens when legitimate websites get compromised. Malwarebytes temporarily divert users away from affected domains until the entire site is completely cleaned up.
In other cases, Malwarebytes merely blocks the bad ads shown on legitimate websites. When a huge Angler malvertising campaign hit big-name online publishers in 2016, Malwarebytes protected users by blocking the domains involved in the attack, consequently blocking malicious ads on The New York Times, the BBC, and Newsweek. More notably, we blocked all exploit attempts with our anti-exploit technology.
Below is a showcase of examples of pop-up notifications (in Malwarebytes for Windows) you will see if you have our malicious website protection module enabled.
Malvertising
One of the main reasons why a legitimate site might be blocked is due to malvertising. Malvertisements are advertisements that look legitimate but contain malicious code to infect systems—often without any user interaction required. Cybercriminals use malvertisements to spread their malware to a greater audience of users by submitting malicious ads to online advertisement networks.
Ad networks then tailor their ads for specific platforms—serving up ads relevant to previous searches and site display settings for PC or Mac operating systems. While this helps cybercriminals determine which type of malware to serve up in their malvertising campaigns, the ad networks are, in fact, usually not aware of the criminal’s ill intent. After submitting and getting their non-malicious ad approved, these criminals then switch out the legitimate, clean ad for the malicious one without the ad network’s knowledge.
The network fails to check modifications made to the advertisements and, therefore, allow the malvertisement to be shown on their customers’ webpages. Furthermore, ad networks also quickly cycle through different advertisements with each view of the customer webpage. The dynamic scrolling of ads makes it difficult not only to flag the existence of a malvertisement circulating on a network but also identifying which advertisement is the culprit!
Read: Truth in malvertising: How to bead bad ads
So now that you know what malvertisements are, you may ask, why doesn’t Malwarebytes’ website blocker just detect the URL of the malicious code rather than the whole ad network? Well, we do—but sometimes that is not enough. This is because malicious ads tend to change often to avoid detection and use different URLs in the operation of their attacks.
We flag and block entire ad networks that are known to host malvertisements (intentionally or unintentionally) because of their failure to conduct regular quality assurance checks on the ads they are circulating. This, in combination with finding numerous malicious ads on their networks and spreading malware, forces us to block not only the malicious advertisements but also the advertisement networks entirely.
Examples of malicious ads
Malvertising is a big-time offender of multiple attacks on sites as prestigious as The New York Times and as low-brow as porn and torrent sites. This attack doesn’t discriminate. Here are a few other examples of malvertising in action:
December 2015: Large number of adult sites distribute malware via AdXpansion malvertising
- Popular adult entertainment sites fell victim to malicious ads served on the AdXpansion network, allowing visitors to be compromised by a Flash Player exploit and other Trojanized payloads.
February 2016: A look behind the Skype malvertising campaign
- Skype and other top publishers were hit by a campaign pushing the exploit kit to install the TeslaCrypt ransomware.
April 2017: Malvertising on iOS pushes eyebrow-raising VPN app
- Users of iOS were also found to be targets of rogue ads when they visited popular torrent sites, ensuing a scareware campaign that pushed a purportedly free VPN app called My Mobile Secure.
As you can see, malvertising happens all the time; and while the effort from the community to fight these attacks has advanced greatly over the last few years, the threat is far from gone.
Cryptomining
The emergence and popularization of cryptocurrency mining, or cryptomining, has redefined how we block certain sites.
While Malwarebytes normally looks for (1) malicious sites harboring malware, PUPs, and phishing kits, and (2) domains associated with malvertising attacks in order to block sites, we now also block many domains that mine for cryptocurrency. Why? While the intentions behind cryptomining may not be malicious—some site owners want to replace traditional advertising with cryptomining in order to create revenue—using the CPU and GPU of website visitors without their knowledge is, in our opinion, malicious behavior.
Visitors who have their CPU and GPU mined without their knowledge might experience dramatic lags, mega-slow downs of Internet service, and fans working overtime to cool down hard-working processors. If mined enough, they may also see some increases in their electricity bills. While this is minor damage compared to having data stolen, it’s still taking advantage of users without consent and disrupting their online experience. Worse, it “could seriously disrupt business or infrastructure critical processes by overloading systems to the point where they become unresponsive and shut down,” as Malwarebytes researcher Jérôme Segura said in our State of Malicious Cryptomining report.
CoinHive.com, a service provider of cryptocurrency miners, was the first domain we blocked due to the fact that the site owners who used this service weren’t asking for users’ permission to run the miners on their systems. Even as CoinHive amended their practices to include a request for user consent, we blocked the “legitimate” program because it would often crank CPU resources up to 100, taking advantage of the full power of victim computers, which can result in a shorter shelf life for the processor itself.
Read: How to protect your computer from malicious cryptomining
Examples of illegal cryptomining
Although cryptomining is fairly new, our researchers have already documented a number of incidents where miners were caught red-handed gobbling up user resources without their knowledge. Below is a list of the latest:
February 2018: New Deepfakes forum goes mining with CoinHive
- Those after the technology behind swapping faces of adult entertainers to celebrities of their choice (or friends they secretly admire) were prime targets of malicious cryptomining set up by an unknown admin of a then-minted Deepfakes forum after its exodus from reddit.
February 2018: Deepfakes FakeApp tool (briefly) includes cryptominer
- A user-friendly version of a face-swapping software that can be used for a Deepfake movie was found to contain code used to silently mine cryptocurrency. After its discovery, a clean version was made available.
March 2018: Malicious cryptomining and the blacklist conundrum
- Proponents of cryptomining have incorporated an evasion technique, which is normally seen in malware, to their miners to avoid getting detected and removed.
What you would see
So now that we’ve shown you the difference between a site that is explicitly malicious and one that is being used malicious purposes such ascryptomining or malvertising, let’s look at an example of our blocking process in action for the latter.
How and when might you come across a website that would be blocked for malicious advertisements? First, if you have been using Malwarebytes for a while, then you might have seen a notice appear, like the one below, while you were surfing what you believed to be a legitimate website. If you were confused or frightened by the notice, don’t worry: It doesn’t necessarily mean that the website you were on is malicious; rather, the advertisements inserted into the webpage might have been.

Take for example:
- You navigate to your favorite website CoolStuffFeed.com to check out the latest news.
- When your page loads up, you see a notice from Malwarebytes for Windows informing you that it is blocking a potentially malicious website.
- You freak out and never visit CoolStuffFeed.com again.
What actually happened here is that while you navigated to CoolStuffFeed.com, Malwarebytes blocked the advertisement provider used by CoolStuffFeed.com due to its association with malvertising. Malicious ads distributed by ad networks (knowingly or not) might include malicious code in pop-ups or advertisement banners that unleash exploit kits, which find vulnerabilities in people’s computers and drop malware—all without a click from the user.
That’s why, when the banners attempt to load or pop-ups attempts to pop, we block them before they have a chance to cause any damage to your system.
Back to our example. Malwarebytes detected the IP address of the ad network, which for our purposes we’ll call “BadAd Network,” as being involved with the distribution of malicious ads. To better track how BadAd Network’s involvement with your favorite website resulted in a block from Malwarebytes, let’s review our example again, this time with more of the story:
- CoolStuffFeed.com hires BadAd Network to provide advertisements to its main site, likely unaware of the ad network’s relationship with malvertising. (Sites like CoolStuffFeed.com use ad networks to bring in possible revenue from every visit.)
- BadAd Network is known by Malwarebytes to host malicious advertisements, so our website blocking feature stops their advertisement traffic from appearing in our users’ browsers.
- You, the customer, will see a notice from us saying that CoolStuffFeed.com is a “Site detected as malicious.” Malwarebytes flags sites affected by malvertising as such.
- In reality, we are blocking advertisements from BadAd Network that are trying to show up in your browser when you visit CoolStuffFeed.com.
Am I protected?
We are strict and prudent about when we decide to blacklist a certain website, so that our users are protected without blocking their access to the Internet. That being said, our product’s web protection capabilities will block sites being used for malicious purposes. If you are one of the many users of Malwarebytes for Windows, then you are likely already safe.
To double-check if you are, simply right-click the Malwarebytes icon in your notification icon bar (opposite from your Start Menu button) and see if Web Protection is On.
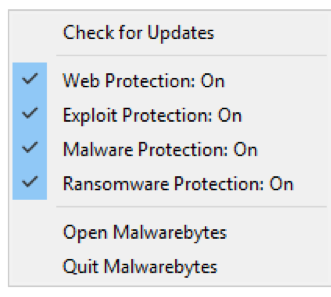
If it is, you are good to go. If not, we highly recommend that you enable it to activate this feature. In addition, exploit protection helps to stop attacks when malvertising attempts to drop malware payloads via exploit kit.
Malwarebytes for Mac doesn’t have its own module for website blocking at the moment, so we advise our Apple users to download and install our Malwarebytes Browser Extension (in BETA) for Chrome and Firefox, which they can download from the Google Play Store and the Firefox Add-ons page, respectively.
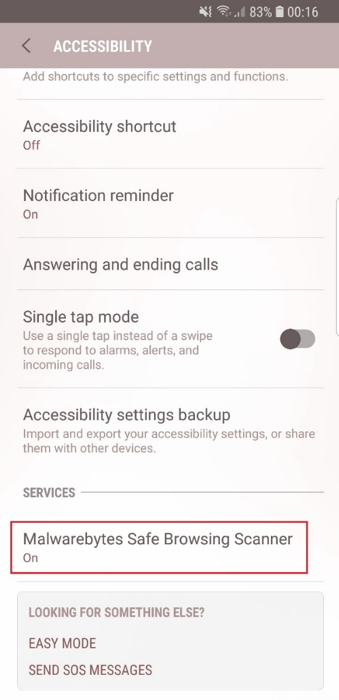
Malwarebytes for Android users can take full advantage of the Safe Browsing Scanner feature, which blocks phishing and malware-related URLs. This is disabled by default, but our app gives you the option to enable it the first time you run the program. If you completely missed this part and want to enable it, or you want to double-check that you have it enabled, go to Settings > Accessibility. Then under Services > Malwarebytes Safe Browsing Scanner. See if it’s set to On. If not, tap it and swipe the slider to enable.
Read: Solutions corner: Malwarebytes for Android
Extra protection
Even if you do not use Malwarebytes and, therefore, are not receiving the benefit of our web blocking protection, there are other ways to keep you safe from sites being used for malicious purposes. One of these is to use ad-blocking software for your browser. This type of app will ensure that no advertisements reach you, regardless of where they come from. This is a great way to not only fend off potential malvertising attacks, but also help you avoid clicking things like fake download buttons or “special offers.” These types of scams exist en mass and are generally delivered to the user through ads and pop-ups.
Another means of defense is simply adopting a cautious, always-suspicious approach to surfing the web. If an email is sent requesting you click on a link, hover over it to see if the URL is, in fact, what it says it is. (And when in doubt, go directly to the website yourself instead of clicking on a link sent via email or text.) If you’re conducting a financial transaction online, always look for the green padlock to the left of the browser (as well as the “https” pre-fix). And when in doubt, remember: If an offer seems too good to be true—it’s likely not legit.
Now you see it, now you don’t
Malicious advertisements, though no longer in high rotation, are still one of the most dangerous threats online, mainly because you can follow every step for safe online hygiene and still become infected. Cryptomining, like bad ads, can remain undetected by users until it’s too late.
The best defense is always to arm yourself with as much protection as you can. Updating Java (or disabling Java in your browser), Flash, your browser, and operating system are all great ways to stay ahead of the curve. However, using anti-malware software with a complete suite of protection features can keep you well protected against malicious websites so you can breathe easy knowing your online experience will be protected.
If you’d like to know which domains and IP addresses Malwarebytes blocks, the Labs team is now maintaining a running list on our Threat Center page.
Thanks for reading, and stay safe!











