How threat actors are using SMB vulnerabilities
Some of the most devastating ransomware and Trojan malware variants depend on vulnerabilities in the Windows Server Message Block (SMB) to propagate through an organization’s network. Windows SMB is a protocol used by PCs for file and printer sharing, as well as for access to remote services.
A patch was released by Microsoft for SMB vulnerabilities in March 2017, but many organizations and home users have still not applied it. So now, the unpatched systems allow threats that take advantage of these vulnerabilities inside, helping active malware campaigns spread like Californian wildfire.
SMB vulnerabilities have been so successful for threat actors that they’ve been used in some of the most visible ransomware outbreaks and sophisticated Trojan attacks of the last two years. In fact, our product telemetry has recorded 5,315 detections of Emotet and 6,222 of TrickBot in business networks—two Trojan variants that are using the SMB vulnerabilities—in the last 30 days alone.
What makes them so effective?
What makes some malware so widespread is the way in which it propagates. While massive spam campaigns only render a few victims that actually pay off, a worm-like infection that keeps spreading itself requires little effort for multiplying returns. And that’s exactly what the SMB vulnerabilities allow their payloads to do: spread laterally through connected systems.
For example, WannaCry ransomware (also known as WannaCrypt), which used one of the SMB vulnerabilities, was launched in May 2017, yet the infection continues to expand. Below is the graph that shows our telemetry for Ransom.WannaCrypt for the month of November 2018.
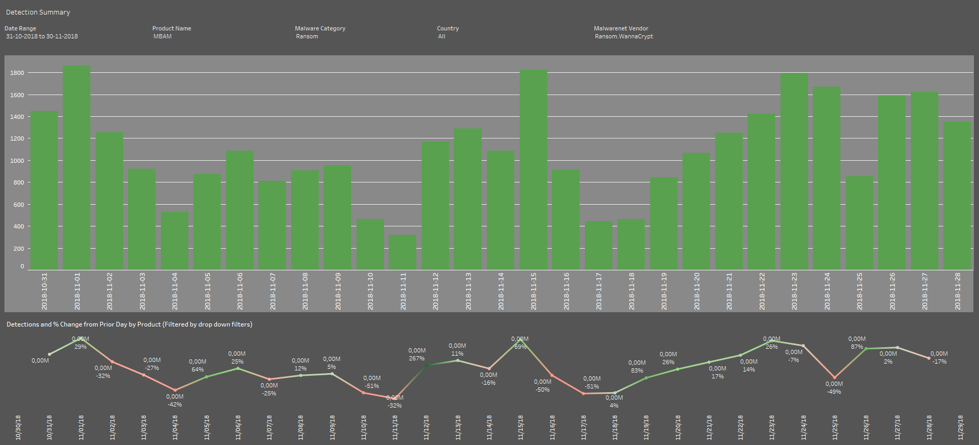
It’s been more than 1.5 years, and WannaCry continues to proliferate, thanks to the sheer number of unpatched machines connected to infected networks.
How did this come about?
At the moment, there are three exploits in the wild that use SMB vulnerabilities. These exploits have been dubbed EternalBlue (used by WannaCry and Emotet), EternalRomance (NotPetya, Bad Rabbit, and TrickBot), and EternalChampion. There is a fourth exploit called EternalSynergy, but we have only seen a Proof of Concept (PoC)—nothing has appeared yet in the wild.
All these exploits were leaked by the ShadowBrokers Group, who allegedly stole them from the NSA. Less then a month after ShadowBrokers published their “findings,” the first fully functional malware that used the EternalBlue exploit, WannaCry, was found in the wild.
Since then, multiple large-scale malware attacks have relied on the SMB vulnerabilities to penetrate organizations’ networks, including the NotPetya and Bad Rabbit ransomware campaigns in 2017, and now the Emotet and TrickBot Trojan attacks, which have been ongoing through the third and fourth quarter of 2018.
Let’s now take a closer, more technical look at each exploit and how they work.
EternalBlue
A bug in the process of converting File Extended Attributes (FEA) from OS2 structure to NT structure by the Windows SMB implementation can lead to a buffer overflow in the non-paged kernel pool. This non-paged pool consists of virtual memory addresses that are guaranteed to reside in physical memory for as long as the corresponding kernel objects are allocated.
A buffer overflow is a programming flaw that lets the data written to a reserved memory area (the buffer) go outside of bounds (overflow), allowing it to write data to adjacent memory locations. This means attackers are able to control the content of certain memory locations that they should not be able to access, which attackers then exploit to their advantage. In the case of EternalBlue, they are able to control the content of a heap that has execution permission, which leads to the Remote Code Execution (RCE) vulnerability, or the ability to execute commands on a target machine over the network.
EternalRomance
Eternal Romance is an RCE attack that exploits CVE-2017-0145 against the legacy SMBv1 file-sharing protocol. Please note that file sharing over SMB is normally used only on local networks, and the SMB ports are typically blocked from the Internet by a firewall. However, if an attacker has access to a vulnerable endpoint running SMB, the ability to run arbitrary code in kernel context from a remote location is a serious compromise.
At the core of this exploit is a type confusion vulnerability. Type confusion vulnerabilities are programming flaws that happen when a piece of code doesn’t verify the type of object that is passed to it before using it. Type confusion can allow an attacker to feed function pointers or data into the wrong piece of code. In some cases, this can lead to code execution.
In other cases, type confusion vulnerability leads to an arbitrary heap write, or heap spray. Heap spraying is a method typically used in exploits that places large amounts of code in a memory location that the attacker expects to be read. Usually, these bits of code point to the start of the actual code that the exploit wants to run in order to compromise the system that is under attack.
After the spray has finished, the exploit uses an info leak in a TRANS_PEEK_NMPIPE transaction. It uses the info leak to determine whether the target is running a 32- or 64-bit version of Windows and to get kernel pointers for various SMB objects.
EternalChampion
The issue exploited by EternalChampion is a race condition in how SMBv1 handles transactions. A race condition, or race hazard, is the behavior of a system where the output depends on the sequence or timing of other uncontrollable events. It becomes a bug when events do not happen in the order the programmer intended. Sometimes these bugs can be exploited when the outcome is predictable and works to the attackers’ advantage.
Meanwhile, a transaction is a type of request that can potentially span multiple packets. For example, if a request is too large to fit in a single server message block (SMB), a transaction of the appropriate size can be created, and this will store the data as it is received from multiple SMBs.
This vulnerability is exploited in two ways: first for an information leak, and second for remote code execution. The bug is first exploited to leak pool information via an out-of-bounds read. To do this, a single packet containing multiple SMBs is sent to the server. This packet contains three relevant pieces:
- A primary transaction request that will immediately be executed.
- A secondary transaction request that triggers the bug caused by the race condition.
- Sets of primary transactions that heap spray the pool with the intention to place a transaction structure immediately behind the one that tracks the first primary transaction request.
First, a transaction is created that contains the shellcode. This does not start the exploit, it just contains the second stage payload. Next, a packet is sent that contains multiple SMBs. The packet contains all expected transaction data and immediately begins execution.
The secondary transaction handler copies the secondary transaction request’s data if it fits in the buffer. Except due to the race condition, the pointer now points to the stack of the primary transaction request handlers’ thread (as opposed to the expected pool buffer). This allows an attacker to write their data directly to the stack of another thread.
The attacker has control over the displacement, so they can choose the amount of data to copy and then copy it. This allows them to precisely overwrite a return address stored on the stack of the primary transaction request handler’s thread, and results in the ability for Remote Code Execution.
EternalSynergy
The Proof of Concept for EternalSynergy shows that incoming SMB messages are copied by an initial handler into the corresponding transaction buffer. But the handler automatically assumes that the provided address is the beginning of the buffer. However, during a write transaction, the same address is automatically assumed to be the end of the existing data, and the address pointing to the beginning of the buffer is updated accordingly.
This means that an attacker can construct a secondary message in the transaction to point beyond the start of the buffer, resulting in a buffer overflow during the copy action.
EternalRocks
Looking for information about these SMB exploits, you may also run into an exploit called EternalRocks. EternalRocks was not included in the ShadowBrokers release, but was instead constructed and discovered later. EternalRocks uses seven NSA tools where, for example, WannaCry only used two (EternalBlue and another called DoublePulsar).
Prevention and remediation
Despite the significant power SMB vulnerabilities afford to attackers, there is one simple remedy to prevent them from ever becoming problematic.
Patch your systems.
The Windows Operating Systems vulnerable to the attacks found in the wild all predate Windows 10. Most attacks work only on Windows 7 and earlier, and Microsoft released patches for the vulnerabilities that were leaked under the Microsoft Security Bulletin MS17-010. This leaves little-to-no reason for networks to be vulnerable to these attacks, yet the number of current victims is overwhelming.
By applying the patch released by Microsoft in 2017, all your eternal headaches can magically disappear. And for extra measure, we also recommend you patch and update all systems, browsers, and software as soon as possible to shore up any other potential vulnerabilities in the network.
In addition, many cybersecurity solutions, including ThreatDown Endpoint Protection, offer innovative anti-exploit technology that can block threats such as EternalBlue from ever dropping their payloads and infecting systems.
It is for good reason that most cybersecurity guides advise users to patch quickly and keep systems updated. So many of the infections seen today could be avoided with consistent monitoring and basic computer maintenance. Unfortunately, a lot of businesses believe they do not have the time or manpower to follow this advice. But when companies leave their networks unprotected, they compromise the integrity of all of our online experiences—especially when SMB vulnerabilities allow infections to spread so quickly.
Don’t be one of those companies. Get protected and stay updated!