There is a relatively old method that might be gaining traction to follow users around on the world wide web.
Most Internet users are aware of the fact that they are being tracked in several ways. (And awareness is a good start.) In a state of awareness, you can adjust your behavior accordingly, and if you feel it’s necessary, you can take countermeasures.
Which is why we want to bring the practice of link auditing to your attention: to make you aware of its existence, if you weren’t already. For those already in the know, you might be surprised to learn that browsers are taking away your option to disable hyperlink auditing.
What is hyperlink auditing?
Hyperlink auditing is a method for website builders to track which links on their site have been clicked on by visitors, and where these links point to. Hyperlink auditing is sometimes referred to as “pings.” This is because “ping” is the name of the link attribute hyperlink auditing uses to do the tracking.
From a technical perspective, hyperlink auditing is an HTML standard that allows the creation of special links that ping back to a specified URL when they are clicked on. These pings are done in the form of a POST request to the specified web page that can then examine the request headers to see what page the link was clicked on.
The syntax of this HTML5 feature is easy. A website builder can use this syntax to use hyperlink auditing:
Under normal circumstances, the second URL will point to some kind of script that will sort and store the received information to help generate tracking and usage information for the site. This can be done on the same domain, but it can also point to another domain or IP where the data can be processed.
What’s the difference between this and normal tracking?
Some of you might argue that there are other ways to track where we go and what we click. And you would be right. But these other methods use Javascripts, and browser users can choose whether they allow scripts to run or not. Hyperlink auditing does not give users this choice. If the browser allows it, it will work.
Which browsers allow link auditing?
Almost every browser allows hyperlink tracking, but until now they offered an option to disable it. However, now major browsers are removing the option for their users to disallow hyperlink auditing.
As of presstime, Chrome, Edge, Opera, and Safari already allow link auditing by default and offer no option to disable it. Firefox has plans to follow suit in the near future, which is surprising as Firefox is one of the few browsers that has it disabled by default. Firefox users can check the setting for hyperlink auditing under about:config > browser.send_pings.
How can I stop link auditing?
You can’t detect the presence of the “ping” attribute by hovering over a link, so you would have to examine the code of the site to check whether a link has that attribute or not. Or, for more novice users, there are some dedicated browser extensions that block link auditing. For Chrome users, there is an extension called Ping Blocker available in the webstore.
Or you can resort to using a browser that is more privacy focused.
Please read: How to tighten security and increase privacy on your browser
Test if your browser allows hyperlink auditing
The link I posted below is harmless and pings the test IP that we have created especially to check whether the Malwarebytes web protection module is working without actually sending you to a malicious site. So this test will show a warning prompt if the following conditions are met:
- Malwarebytes Web Protection module is enabled
- You are allowing Malwarebytes notifications (Settings > Notifications)
- Your browser allows link auditing
Create a textfile with the code posted below in it and save it as a html file. Rightclick the html file and choose to open it with the browser you want to test. If the browser allows link auditing, then you should see the warning shown below when you click this link:
The ping in this link will be blocked by MBAM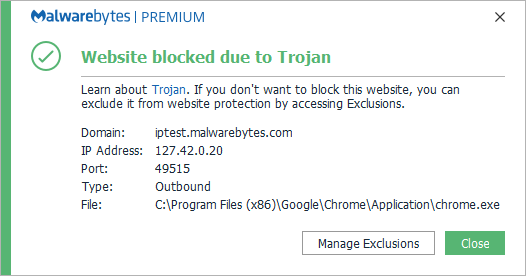
Malwarebytes and hyperlink auditing
As demonstrated above, Malwarebytes will protect you if either one of the URLs in a link leads to a known malicious domain or IP. There are no immediate plans to integrate anti-ping functionality in our browser extensions, but it is under consideration. Should the need arise for this functionality to be integrated in any of our products, we will lend a listening ear to our customers.
Abuse of hyperlink auditing
Hyperlink auditing has reportedly been used in a DDoS attack. The attack involved users that visited a crafted web page with two external JavaScript files. One of these included an array containing URLs: the targets of the DDoS attack. The second JavaScript randomly selected a URL from the array, created the tag with a ping attribute, and programmatically clicked the link every second.
Skimmers could use hyperlink auditing if they figure out how to send form field information to a site under their control. If they would be able to plant a script on a site, like they usually do, but in this case use it to “ping” the data to their own site, this would be a method that is hard to block or notice by the visitors of the site.
Countermeasures
At the moment, there doesn’t seem to be an urgent need to block hyperlink auditing for the average Internet user. The only real problem here is that it takes third-party software to disable hyperlink auditing when browsers should be offering us that option in their settings. For the more careful Internet users that had disabled hyperlink auditing earlier, it is recommended to check whether that setting is still effectively working on the browser. The option could be removed after every update and you could have missed that this happened.
Stay safe everyone!











