Many of us who read the news daily encounter a regular drum beat of ransomware stories that are both worrying and heartbreaking. And what many of us don’t realize is that they are often interconnected. Some of the gangs behind the ransomware campaigns that we read about have established a relationship among each other that can be described as “being in league with each other”, yet they lack certain elements that might cement their status as a true cartel in the digital underground world.
This is the overall finding of Jon DiMaggio, known cybersecurity luminary and Chief Security Strategist for Analyst1, a threat intelligence company.
In a whitepaper entitled “Ransom Mafia – Analysis of the World’s First Ransomware Cartel”, DiMaggio and his team aimed to provide an analytical assessment on whether there is indeed a ransomware cartel, or if indications there might be was just something the ransomware gangs fabricated to distract researchers and law enforcement.
The ties that bind
Analyst1 has identified two strong connections among the affiliated groups mentioned in its report that establishes how they work together as something like a cartel. They are:
Shared data leak sites
The gangs within the cartel share information about the companies they have attacked, as well as all the data they have exfiltrated. In one example, the researchers saw Twisted Spider posting victim data gathered by the Lockbit gang and Viking Spider. This is on top of these gangs posting company data onto their respective leak sites.
Shared infrastructure
SunCrypt was found using IP addresses and Command and Control infrastructure tied to Twisted Spider to deliver the ransomware payload in its campaigns. This was observed 10 months after Twisted Spider used them in its operations. This kind of resource sharing can only occur if a relationship of trust has already been established.
Analyst1 has also identified other circumstantial and technical ties among the groups that, on their own, aren’t sufficient measures for precise attribution.
Other noteworthy findings
The research includes several other noteworthy findings:
- Victim data is not the only thing these affiliate gangs pass between each other. They were also observed sharing tactics, such as the increasing proliferation and persistence of their malware in the wild by making a Ransomware-as-a-Service (RaaS) package available to other criminals, and command and control (C&C) infrastructure.
- Affiliated gangs appear to be on the move to automate their attacks, in evidence of added automated capabilities found in ransomware payloads. Manually infecting compromised companies is a known hallmark of big game hunting (BGH) ransomware threat actors.
- Some of the groups involved have opened themselves to media interviews in the past. They also issue their own press releases from their own websites and use multiple means to harass victims into paying up.
- Affiliated gangs have claimed to be part of a cartel at some point in the past. Although some of them have already denied their connections, evidence contradicts this.
Who is in the cartel?
Analyst1 grouped affiliated ransomware gangs under the “Ransom Cartel” tag. Note, however, that this collective had named themselves the “Maze Cartel” the same year their cooperative relationship had been established.
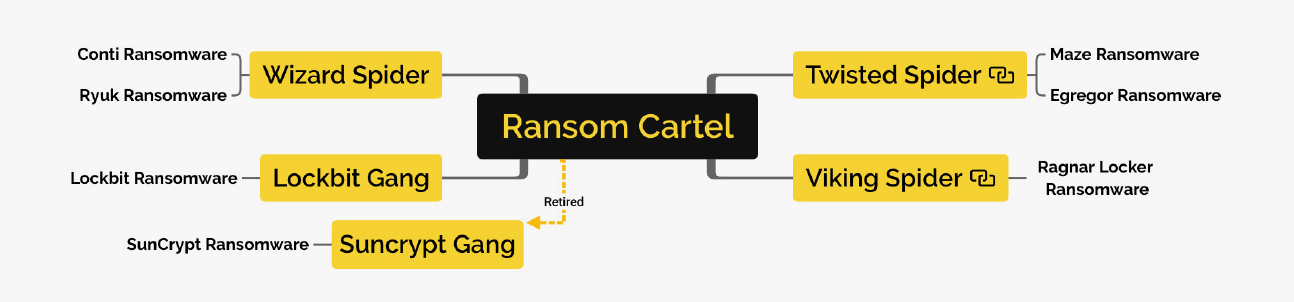
The Ransom Cartel arose in May 2020. Twisted Spider, the gang behind Maze ransomware and others, is said to be the group that initiated its creation. Their primary motivation was financial gain.
Most of these groups are based in Eastern Europe and they primarily speak Russian, an attribute they don’t hide at all. Some of these groups have developed malware other than ransomware; however, all groups made sure that none of them would affect users in Russia and in the Commonwealth of Independent States (CIS).
Below is a brief overview of the individual groups said to make up the Ransom Cartel (Note that not all of them go for an official name. As such, they are named based on the ransomware variant they use):
Twisted Spider
Other alias(es): Maze Team, FIN6
Malware: Maze ransomware (previously known as ChaCha), Egregor ransomware, Qakbot worm, other commodity exploit kits
Malwarebytes detections: Ransom.Maze, Ransom.Sekhmet, Worm.Qakbot, respectively
LockBit gang
Other alias(es): none
Malware: LockBit ransomware, Hakops keylogger
Malwarebytes detection: Ransom.LockBit, Trojan.Keylogger, respectively
Wizard Spider
Other alias(es): Grim Spider (hailed as a subset of Wizard Spider), UNC1878, TEMP.MixMaster
Malware: TrickBot Trojan, Ryuk ransomware, Conti ransomware, MegaCortex ransomware, BazarLoader backdoor
Malwarebytes detection: Trojan.TrickBot, Ransom.Ryuk, Ransom.Conti, Ransom.MegaCortex, Trojan.Bazar, respectively
Viking Spider
Other alias(es): Ragnar group
Malware: Ragnar locker ransomware
Malwarebytes detection: Ransom.Ragnar
SunCrypt Gang
Other alias(es): none
Malware: SunCrypt ransomware
Malwarebytes detection: Ransom.SunCrypt
“What cartel?”
Although there is indeed trust, and sharing of resources and tactics, among these ransomware gangs, Analyst1 has assessed that the Ransomware Cartel is not a true cartel. Its report concludes that the cooperation it witnessed lacked some of the elements needed to reach the level of a cartel, most notably profit-sharing.
You can read more about the report here.










