Spam which claims your account has been locked out and needs to be fixed are common. They drive people to phishing campaigns on a daily basis.
The mail below follows the same pattern with one key difference. It looks like a phish, but goes somewhere else entirely.
No, your Apple ID has not been locked
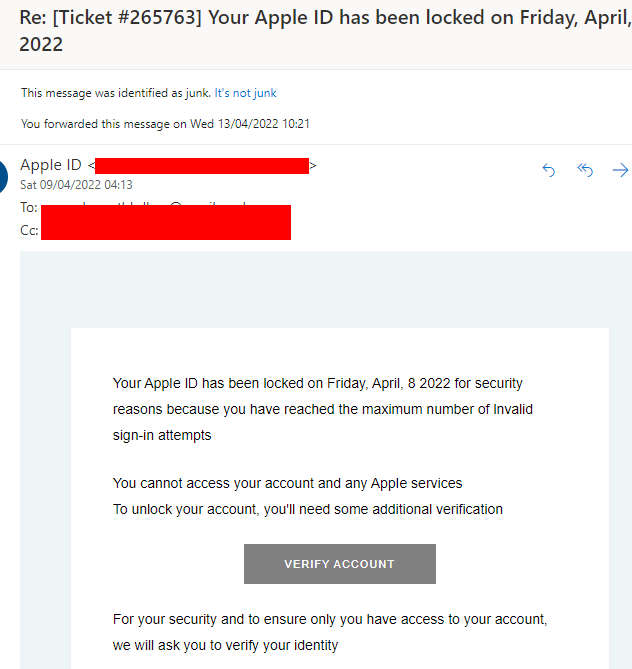
The mail claims to be from Apple, and is titled
Re: [Ticket #265763] Your Apple ІD has been locked on [date]
It reads as follows:
Your AppIe lD has been locked on [date] 2022 for security reasons because you have reached the maximum number of lnvalid sign-in attempts
You cannot access your account and any AppIe services
To unlock your account, you’ll need some additional verification
For your security and to ensure only you have access to your account.We will ask you to verify your identity.
From phish to website spam
Clicking the big grey “verify account” button should, in theory, lead you to an Apple phishing page. However, that’s not the case here.
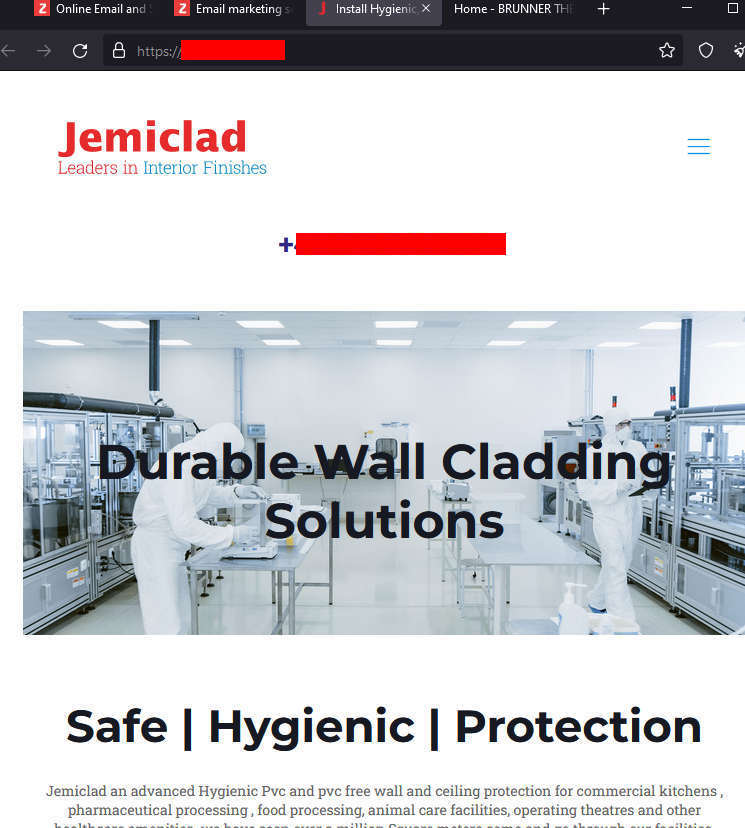
The link directs people to completely random domains. Some of them appear to be advertisements. Others run the full range of everything from wall cladding services and polytechnics to hotels.
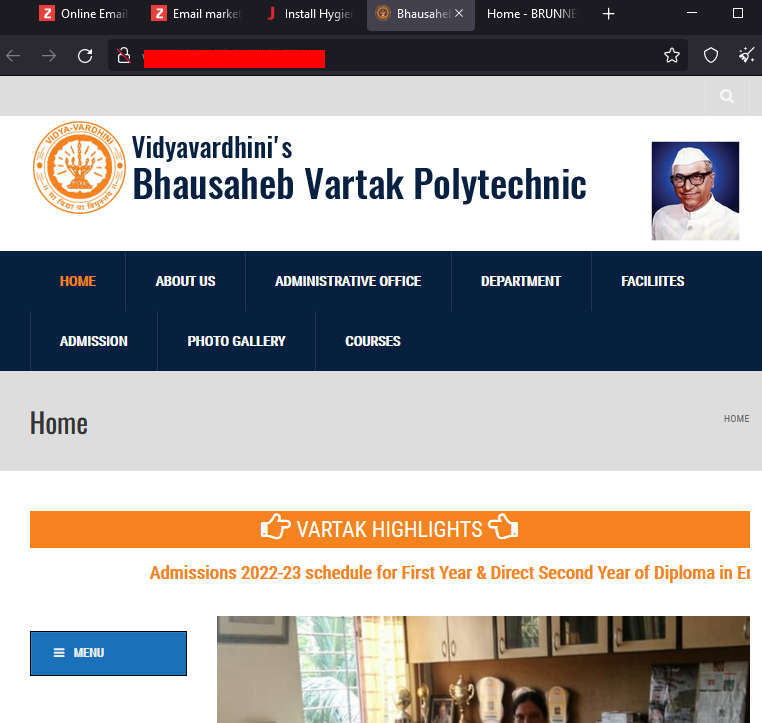
There appears to be no rhyme or reason to the URLs being served up. Clicking the link could pretty much drop you anywhere without warning.
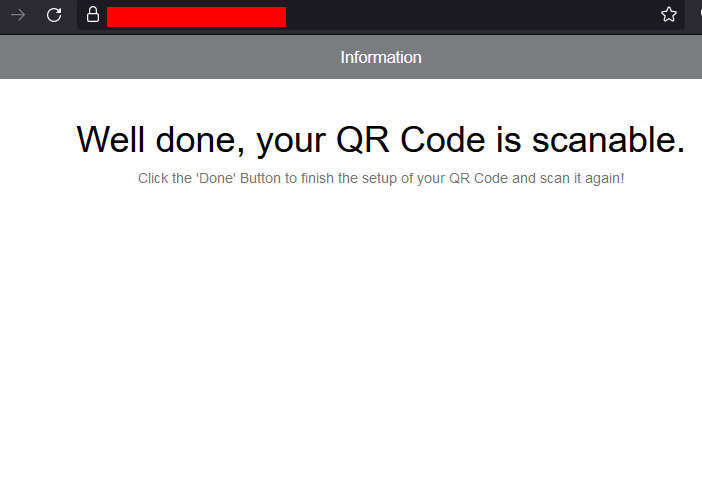
It currently leads to what appears to be a half-finished page about QR code generation.
Why is this happening?
At this point, we’ve established that there’s no phish here. It’s using phishing as a panic-ruse to have you click through to multiple URLs via email campaigns. In this case, it appears someone has signed up to the below service, and is using this to spam.
Navigating to the URL included in the mail with the campign component stripped out leads us to the below message:
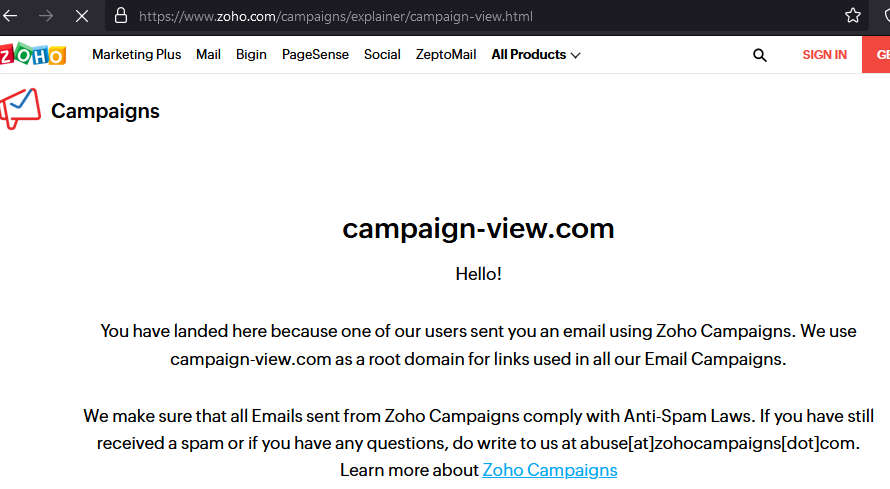
Mail blasting for fun and profit
Mail spammers will try and abuse legitimate services in order to drop as many missives in your mailbox as possible. Even with countermeasures in place, they’ll slip through the net of even the most careful service provider.
Regardless of how the spam gets through, get through it will. If you provide mail marketing services, it’s important to have a reporting feature in place. The ability to tie valid registrant details to campaign URLs is also crucial.
If it’s possible to highlight in mails sent out in some way that it’s via your tool or app, so much the better.
Keeping yourself safe from mail spam
For recipients, much of the typical spam mail advice applies here:
- Always report spam, especially if it’s going beyond the usual “please buy this t-shirt” missive. If it’s a phish, a social engineering trick of some kind, or even something malware related, block and report. It’ll help keep bad content away from others that little bit quicker.
- If you are redirected to a phish, you’re perilously close to handing over logins to a scammer. Websites asking for details without the HTTPs are a massive red flag. However, as we often point out, scammers often make use of HTTPs certificates so this is no guarantee of safety from phishing. Rather, ask yourself if you typically receive emails from Facebook or Google or anyone else asking you to visit links and enter personal details. The answer should almost certainly be no.
- You can try the “strip out the campaign portion of the URL and see where you end up” tactic. However, you won’t know in advance if the URL on display is from a genuine marketer or just another rogue website. Search engines may assist here, but it’s a bit of a shot in the dark and potentially risky.
- One final reminder: spammers reuse bogus mails all the time. While this one appears to redirect to random websites, the next identical message in your mailbox may well drive you to a phishing domain. Keep these fraudsters at arm’s length with a metaphorical return to sender.
We’ve reported the above mail campaign to the organisation above and hopefully it’ll be shut down soon.










