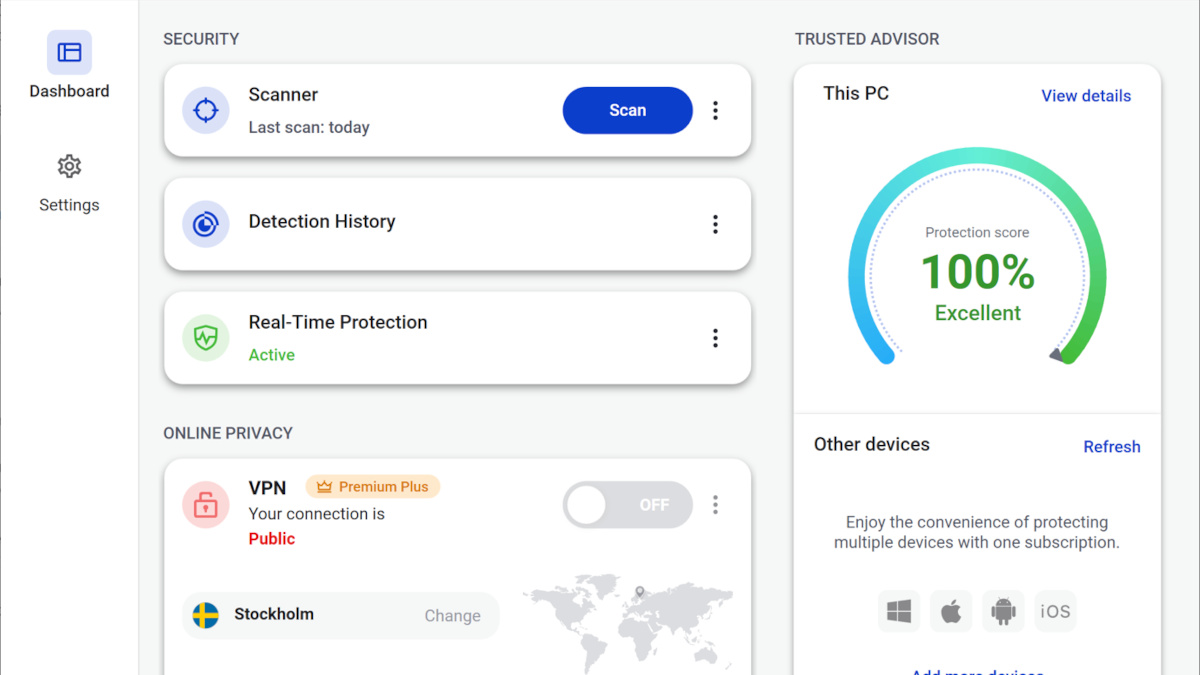
Our Trusted Advisor dashboard provides an easy-to-understand assessment of your device’s security.
Tag: iOS
GoldPickaxe Trojan steals your face!
A group of cybercriminals is committing bank fraud by convincing victims to scan their IDs and faces.
Apple warns of “privacy and security threats” after EU requires it to allow sideloading
To comply with the EU’s Digital Markets Act, Apple will allow European iPhone owners to install apps obtained from outside the official App store.
Update now! Apple patches vulnerabilities on iPhone and iPad
Apple has released iOS 17.0.3, an emergency update fixing two vulnerabilities, one of which has already been exploited by cybercriminals. The update is…
[Updated] Apple issues Rapid Security Response for zero-day vulnerability
Apple has issued an update for a vulnerability which it says may have been actively exploited. In the security content for…
Apple releases first Rapid Security Response update for iOS, iPadOS, and macOS users
On Monday, Apple released its first batch of Rapid Security Response (RSR) patches, iOS 16.4.1 (a), iPadOS 16.4.1 (a), and macOS 13.3.1 (a),…
Update now! Apple fixes actively exploited vulnerability and introduces new features
Apple has released security updates for several products. Most notably one of the updates fixes an actively exploited vulnerability in the…
iPhone calendar spam: What it is, and how to remove it
If you open up your iPhone and see a variety of messages claiming that you’ve been hacked, your phone is not…
Update now! Apple patches vulnerabilities in MacOS and iOS
Apple has released information about the new security content of macOS Ventura 13.2.1 and of iOS 16.3.1 and iPadOS 16.3.1. Most…
VASTFLUX ad fraud massively affected millions of iOS devices, dismantled
Researchers have successfully dismantled a massive ad fraud campaign they stumbled upon by accident. The Satori Threat Intelligence and Research Team dubbed…


![[Updated] Apple issues Rapid Security Response for zero-day vulnerability](https://www.malwarebytes.com/wp-content/uploads/sites/2/2023/07/asset_upload_file33364_272592.png?w=736)