The FBI has warned businesses of an uptick in reports of criminals applying for remote work using deepfake and stolen PII…
Tag: personally identifiable information
“Have I been pwnd?”– What is it and what to do when you *are* pwned
Adobe. Yahoo!. The US Department of Energy (DoE). The New York Times. What these names have in common is that they…
The many ways you can be scammed on Facebook, part II
In part 1 of this article series, we looked at data mining schemes, scam ad campaigns, concert tickets scams, and PayPal…
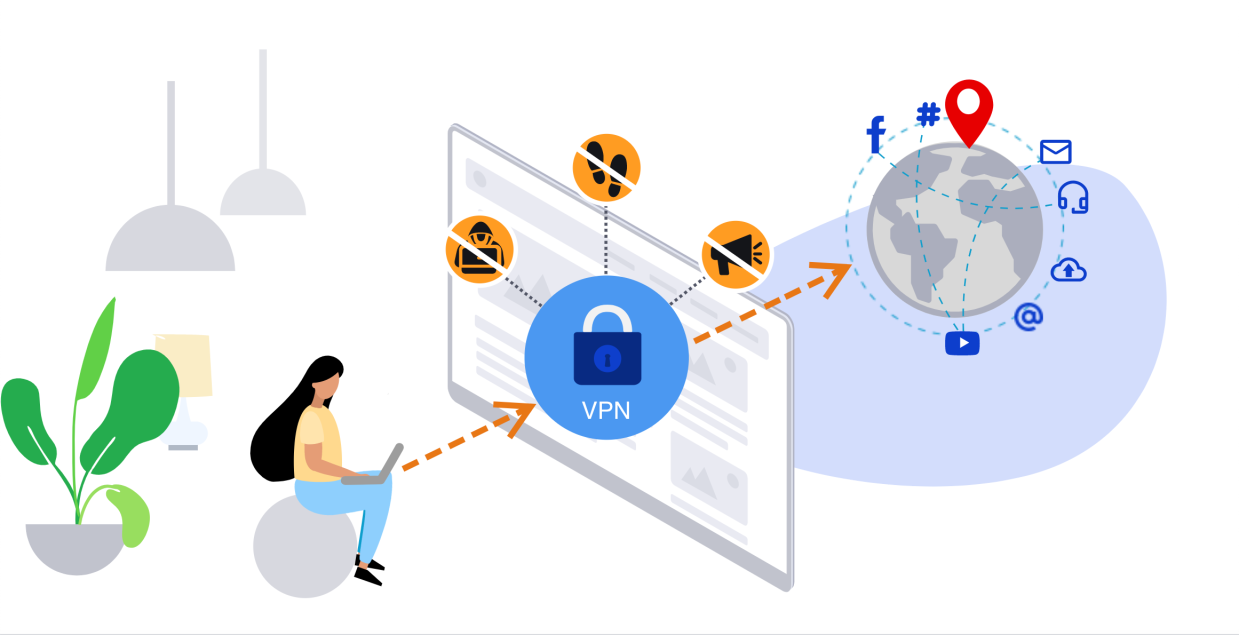
Introducing Malwarebytes Privacy
Here at Malwarebytes, we’re no strangers to using virtual private networks (VPNs) to protect our privacy while browsing online. Regular readers…
Child identity theft, part 2: How to reclaim your child’s identity
In a world where children as young as a single day old can fall prey to fraud, it is more important…
Child identity theft, part 1: On familiar fraud
In 2013, 30-year-old Axton Betz-Hamilton received an angry phone call from her father two weeks after her mother, Pam, died. “What…
Business in the front, party in the back: backdoors in elastic servers expose private data
It seems like every day we read another article about a data breach or leak of cloud storage exposing millions of…
How to protect yourself from doxing
“Abandon hope all ye who enter.” This ominous inscription affixed atop the gates to Hell in Dante’s Divine Comedy applies peculiarly…
What role does data destruction play in cybersecurity?
When organization leaders think about cybersecurity, it’s usually about which tools and practices they need to add to their stack—email protection,…
How much personalization is too much?
This story originally ran in The Parallax on January 25, 2019, and was written by Dan Tynan. In 2012, when Target…