In this series of posts, we will be using the flowchart below to follow the process of determining which adware we are dealing…
Tag: PUP
Adware the series, part 3
In this series of posts, we will be using the flowchart below to follow the process of determining which adware we are dealing…
Adware the series, part 2
In this post, we will be using the flowchart below to follow the process of determining which adware we are dealing with. Our…
System optimizers turning to tech support scams
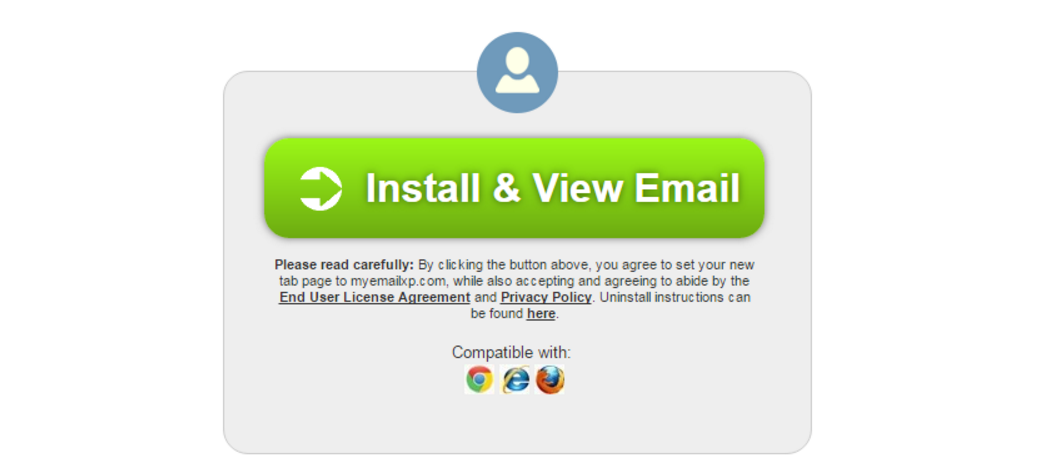
A new trend, which was also pointed out in our Q1 cybercrime report, is the combination of PUPs and Tech Support…
Adware the series, part 1
In this series, we will be using the flowchart below to follow the process of determining which adware we are dealing…
Report: Cybercrime climate shifts dramatically in first quarter
The first quarter of 2017 brought with it some significant changes to the threat landscape and we aren’t talking about heavy…
Chinese PUPs and backdoor drivers: making systems less secure since 2013
PUPs affect systems all across the world and are developed in many countries. A few weeks ago I came across an installer…
Spigot browser hijackers
There is a large family of Spigot browser hijackers that all have a lot in common. So by giving you a…
Why Malwarebytes detects PC Pitstop as Potentially Unwanted
At Malwarebytes, we take great pride in the fact that we’re protecting customers – not just from malware – but from…
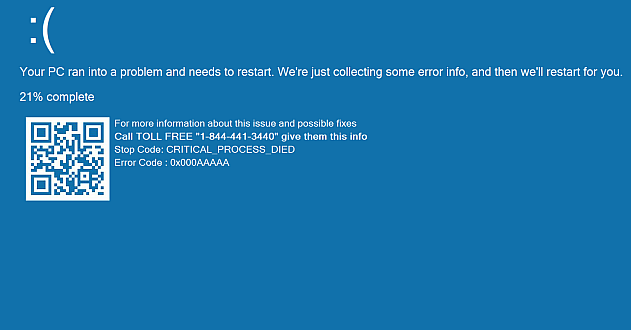
A closer look at a tech support screen locker
In this blog post, we are going to take a closer look at some of the code that the most predominant…