February 2024 is likely to be remembered as one of the most turbulent months in ransomware history.
Tag: ransomware
Stopping a targeted attack on a Managed Service Provider (MSP) with ThreatDown MDR
Detecting and disrupting a months-long malware campaign on an MSP.
Change Healthcare outages reportedly caused by ransomware
The cyberattack on Change Healthcare that has been causing a lot of disruptions is likely the work of the BlackCat/ALPHV ransomware gang.
Why ransomware gangs love using RMM tools—and how to stop them
More and more ransomware gangs are using RMM tools in their attacks.
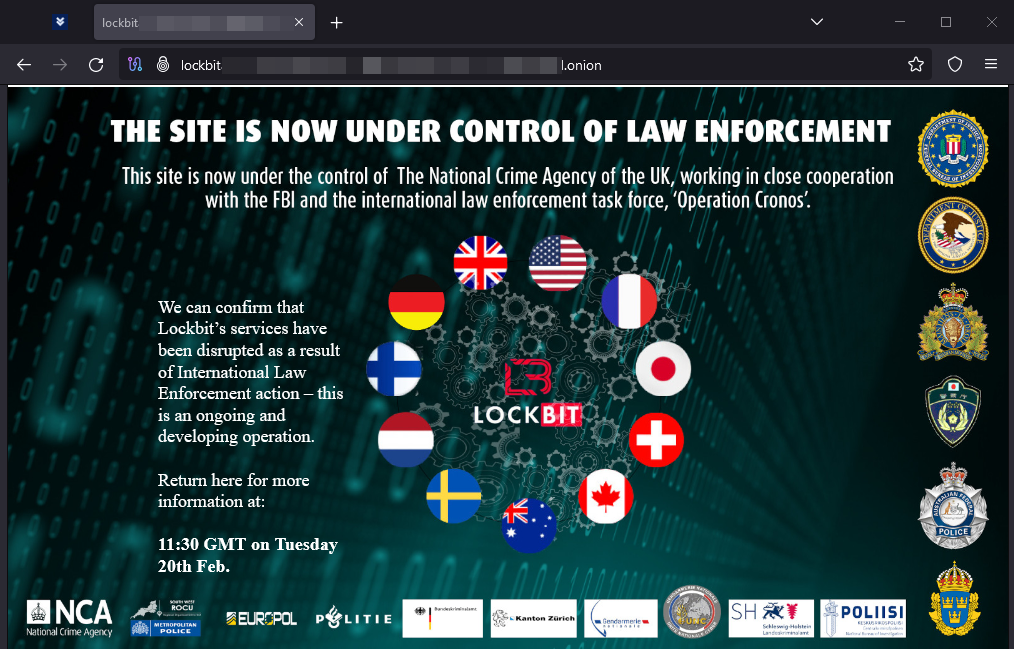
Law enforcement trolls LockBit, reveals massive takedown
Law enforcement has humiliated the humiliators.
A week in security (February 12 – February 18)
A list of topics we covered in the week of February 12 to February 18 of 2024
Ransomware review: February 2024
In January, we recorded a total of 261 ransomware victims.
Known ransomware attacks up 68% in 2023
Big Game ransomware is just one of six threats resource-constrained IT teams need to pay attention to in 2024.
Malwarebytes wins every MRG Effitas award for 2 years in a row
ThreatDown has earned 37/37 awards over nine consecutive quarters.
2024 State of Ransomware in Education: 92% spike in K-12 attacks
2023 was the worst ransomware year on record for Education.