The flaws could allow an attacker with privileged access to a guest VM to access the hypervisor on the host.
Tag: virtual machine
Update now: Critical flaw in VMWare Fusion and VMWare Workstation
Four vulnerabilities in virtualisation software have been fixed by VMware, including two which were exploited at the 20223 Pwn2Own contest. Three have…
BlackBasta is the latest ransomware to target ESXi virtual machines on Linux
BlackBasta, an alleged subdivisionof the ransomware group Conti, just began supporting the encryption of VMware’s ESXi virtual machines (VM) installed on…
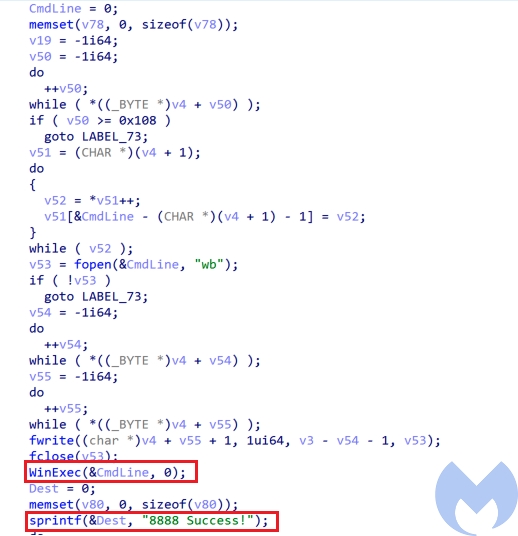
Royal Mail phish deploys evasion tricks to avoid analysis
Royal Mail phish scams are still in circulation, slowly upgrading their capabilities with evasion tools deployed in far more sophisticated malware…
Clop targets execs, ransomware tactics get another new twist
Ransomware peddlers have come up with yet another devious twist on the recent trend for data exfiltration. After interviewing several victims…
RegretLocker, new ransomware, can encrypt Windows virtual hard disks
Cybersecurity researchers discovered a new ransomware last month called RegretLocker that, despite a no-frills package, can do serious damage to virtual…
Technology and the power of moral panic
Moral panic is a fascinating topic, and often finds itself tied up in the cutting edge-technology of the times once it works…
Malware vaccination tricks: blue pills or red pills
First, let me explain what I mean by malware vaccination tricks. Most of you will have heard about some of these….
A Look at Malware with Virtual Machine Detection
It’s not uncommon for the malware of today to include some type of built-in virtual machine detection. Virtual Machines (VMs) are…
Online PC Support Scams: Turning the Tables
You may recall a post I wrote back in April about fake Microsoft phone support calls. I had received a call…