[ Need assistance? Please consult our Help & Resource Page ]
Have you ever received a call from someone with a heavy Indian accent from Microsoft saying your computer had errors or viruses? The purpose of these calls is to get an easy $299 (or whatever amount they choose) by scaring you into thinking there’s something really wrong with your computer and that they can fix it for you.
These telephony scams have been going on for many years and scammers keep robbing innocent people sadly because their success ratio is still worth their time and effort. It happens that I got ‘the call’ while minding my own business on a regular work day. I immediately recognized what this was all about and decided to play the game to see how far this would go.
The caller’s number did not appear on my phone, a sign that they were using some Voice over IP (VoIP) or such technology that both completely hides their identity and costs them nothing for long distance calls.
This scam is a well-oiled machine which starts off with the alleged Microsoft representative asking you to turn on your computer to perform some checks for errors. They essentially make you open different applications which aren’t typically known by regular users.
Step 1: scare tactics
I was instructed to press the “Windows” and “R” as in Robert keys together to get to the Windows Run dialog box. They then made me type a few more keys to open up Window’s Event Viewer:
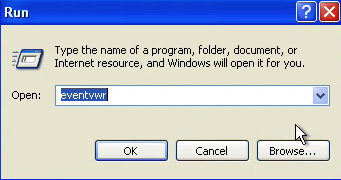
Figure1: Run dialog and command to open Event Viewer
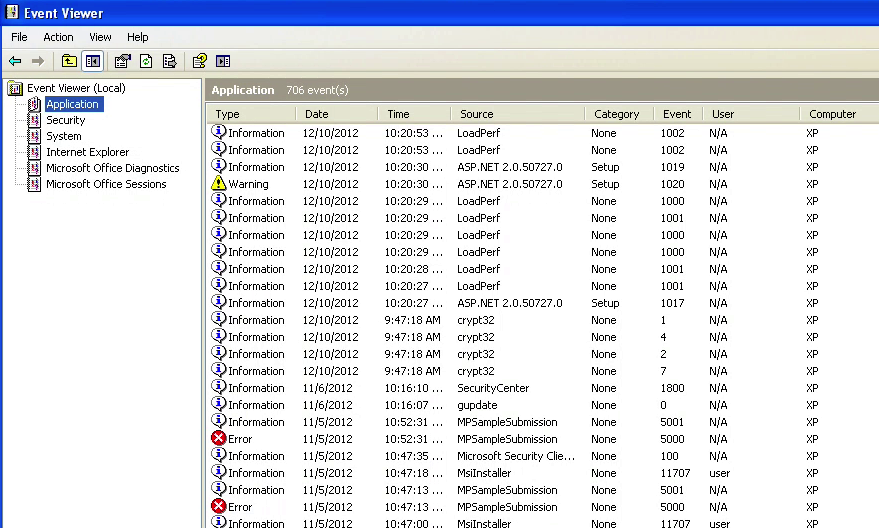
Figure2: Event Viewer showing typical errors
Conveniently, the event viewer will always show some warning or error which the scammer can leverage to instill fear. “You can see it in your own eyes”, she continued before asking me to count how many I could see. While we could have stopped right there, she was intent on pursuing the diagnostic further.
Next stop was Windows Prefetch files:
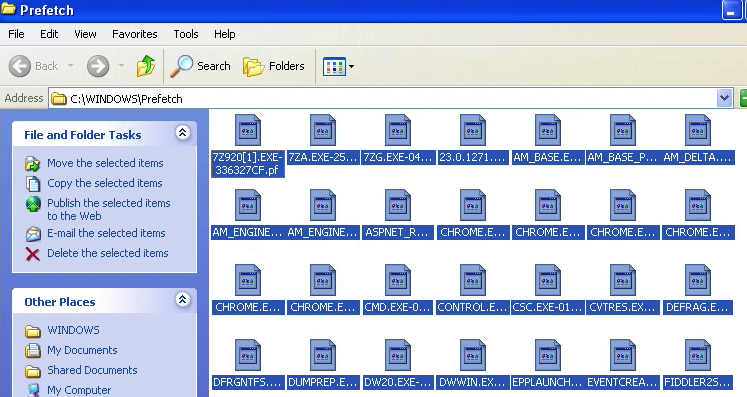
Figure3: Windows Prefetch files
The interesting thing about this is that she called those files spyware and viruses so we went from my computer having some errors to being infected. Yet another lie, as those Prefetch files are simply used by Windows to launch programs faster.
Bad things come in threes, as I was now instructed to open the “System Configuration Utility”, also known as msconfig.
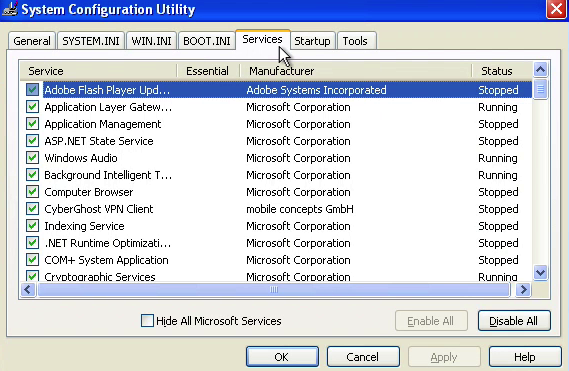
Figure4: Msconfig showing services
She made me focus on the status of each Service and asked me once again to count how many “stopped” ones there were. When I gave her a ball park number, she retorted: “You are just guessing, I want you to count”.
At this point I was ready to beg her to stop and she seemed to think it was enough convincing, that I was ripe enough to move on to the next step. She kindly asked me if I wanted to remediate all these problems and I accepted it. Other than the blatant lies, she had not been too pushy and to her credit gave me the option to decline assistance.
Step 2: the “intervention”
The next part consisted of getting a remote person to fix these “issues” for me. To give them access to my computer I had to download a program called TeamViewer which is totally legitimate software used by many companies and individuals to remote into somebody else’s machine.
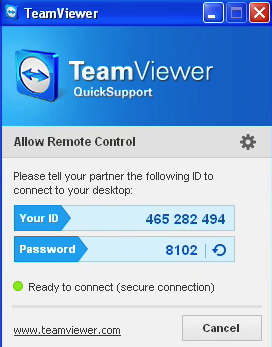
Figure5: TeamViewer, a free program to remote into computers
At this point she asked me for the ID and password before telling me she was going to transfer me to her supervisor. I believe this next person’s role is to process victims and to ensure payment goes through. The man on the phone also had a thick Indian accent and sounded quite professional. He told me a remote technician (which quite likely was also him) was ready to get working on my computer but he could not proceed until I actually instructed him to. I think this might be another technique used to cover themselves, as in I willingly asked them to help me. I felt like asking if I should say “open sesame” but instead I refrained from a cheap joke at their expense and asked what the secret word was. He told me to type “renew my warranty” to the technician.
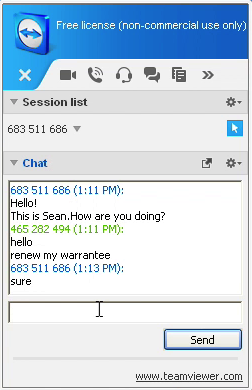
Figure6: Once the magic words have been spoken, it all goes downhill..
‘Sean the technician’ was more than eager to help me but the first thing he did was to open my browser to PayPal’s website so that I could pay the required lifetime fee of $299.
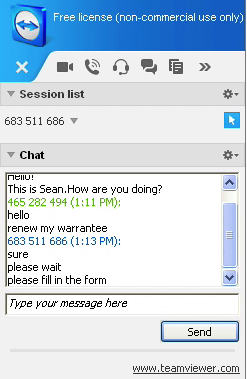
Figure7: A happy scammer ready to go to work
Figure8: they want real money!
At that point, I decided to change my mind and no longer wanted to pay so much money for such a ridiculous scam. So instead I entered a wrong Credit Card number to buy some time.
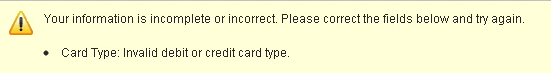
Figure9: (Un)fortunately, I can’t seem to type my Credit Card number right
After a few other failed attempts I could see the guys were starting to lose patience and then, out of the blue, something very bad happened. Without saying a word, the “remote Microsoft Technician” minimized the PayPal window and took on a mission to destroy all my personal files:
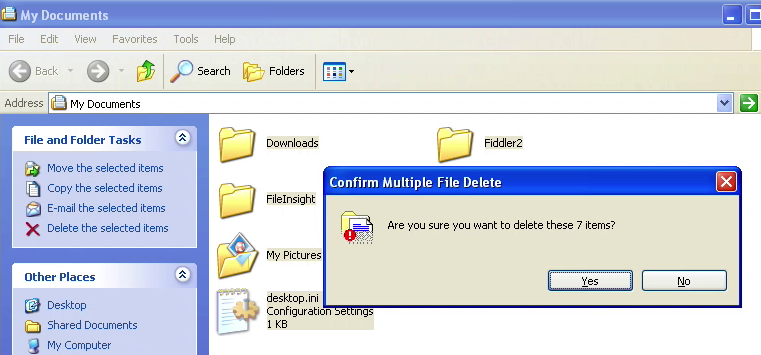
Figure10: Scammer crosses the line big time, deletes all my pictures, documents, music
I could not believe my eyes. He went on exploring directories in search of other things to remove as fast as he could. When he could not find anything else worthy he could delete, he typed his last message:
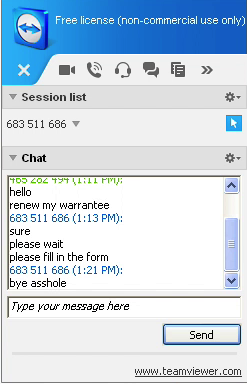
Figure11: They seem upset that I wasted their time
Before completely disappearing he did do one last thing, which was to remove the driver for my ethernet card. This achieved the expected result of completing cutting out my Internet connection.
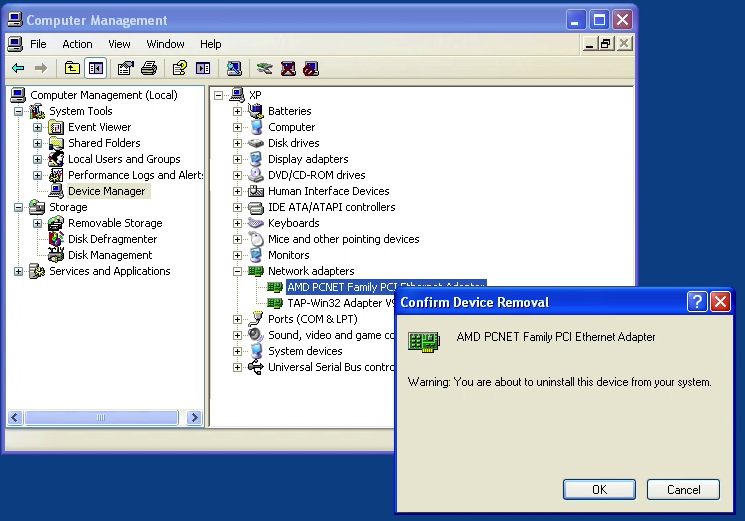
Figure12: Cutting me off, the hard way
As this happened, I was still on the line with the “supervisor”, one of the scammer’s identity, to whom I recounted what had just happened. I’m not sure whether it was the language barrier between I (a French man) and him but he solemnly said: “if the technician says something, it must be right. The technician is always correct”. Shortly after, the line was dead.
Unlike many other people (who turn the tables against the scammers by wasting their time) I had entered this phone call with a nice and open state of mind. I wasn’t going to play tricks on them or make fun of them. I just wanted to see for myself how the scam was conducted and learn more about it.
Having seen my fair share of deceptive marketing practices and software over the years, I can say a personal phone call is probably one of the cruelest tricks to play on an innocent victim. It is far too easy to fool someone by showing them “errors” and label them as extremely severe. With a sales clerk in a computer store one day trying to teach me what viruses were and why I so badly needed to purchase an antivirus, this experience ranks high up there in the “you don’t have a clue who you are talking to” category.
While they may legally be walking a fine line with all their sweet talking and magic passphrases, they crossed that line when they deleted documents on my computer and sabotaged the Internet connection. This is destruction of private property plain and simple. At the end of the day, I haven’t really lost any documents since this was a Virtual Machine and not an actual computer. One thing I lost though, was my faith in mankind, not that there was much of it left anyway.
Since these scammers use all sorts of tricks and fake identities, one of the best ways to ruin their business is simply to make it unworthy by spreading the message around so people don’t fall for these scams. Easier said than done because it is touching on things like human nature, social engineering, fear and scare tactics: basically things that have worked for thousands of years. But even if we can make a dent in their profits, let’s do it!
I’ve recorded this scam and uploaded it to YouTube. A minute into the call, I fired up a VM, put the phone on speaker mode and captured everything that was happening.
Update (10/15/13):

We have created a resource page with all the information you need about tech support scams.
We document the most common tricks fake Microsoft technicians will use against you and how to protect yourself if you have received such a call.
For those interested in fighting back, we also link to multiple resources where you can report the information you may have obtained from the scammers (i.e TeamViewer ID, phone numbers, etc).
Thanks for reading and helping us in the fight against fraud!









