Update [10/30/2014 1:06PM GMT]: We found the website called ebola(dot)events, which appears similar to ebolawarnings(dot)com. Upon visiting the dot events site, however, it plays a warning siren. Testing shows that the executable file hosted on the said site doesn’t install the same way the previous sample we saw and tested had: For one thing, the file only installs properly on systems located in the US. It also no longer exhibited the symptoms we’ve observed and documented in the original post below. What it does is access a site registered to an ad monetizing company before it auto-downloads the file for the user. Once the file is executed, the below interface appears, which allows the users to also specify their location (US states only) and ZIP code.
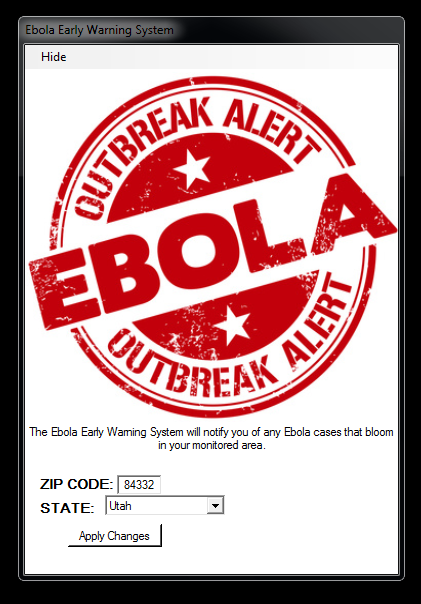
Users can also choose to hide this interface by pressing “Hide” at the top-left side. Doing so minimizes the window at the bottom-left side of the desktop, showing only the title of the program.
Original post:
Craig Spencer, a doctor from New York City, is the fourth and latest person diagnosed with Ebola in the U.S after arriving from Guinea.
More news of infection outside Africa such as this could further fuel the ever-increasing fear and anxiety for one’s own life and well-being, especially in terms of how one interacts with the outside world.
People are trying to be more careful in their dealings than usual, always wanting to be on the know about the latest happenings.
This is why web threats banking on perennial hot topics like Ebola could be effective lures against users, especially in the long run.
Not so long ago, spam posing as an email from the World Health Organization (WHO), discovered by our friends at Trustwave, to carry a document containing information on how one can be safe from the deadly disease, which turns out to be a DarkComet RAT malware.
Recently, we found ebolawarnings(dot)com, a domain claiming to offer an early warning system tool that can alert the user of any Ebola outbreaks near their area.
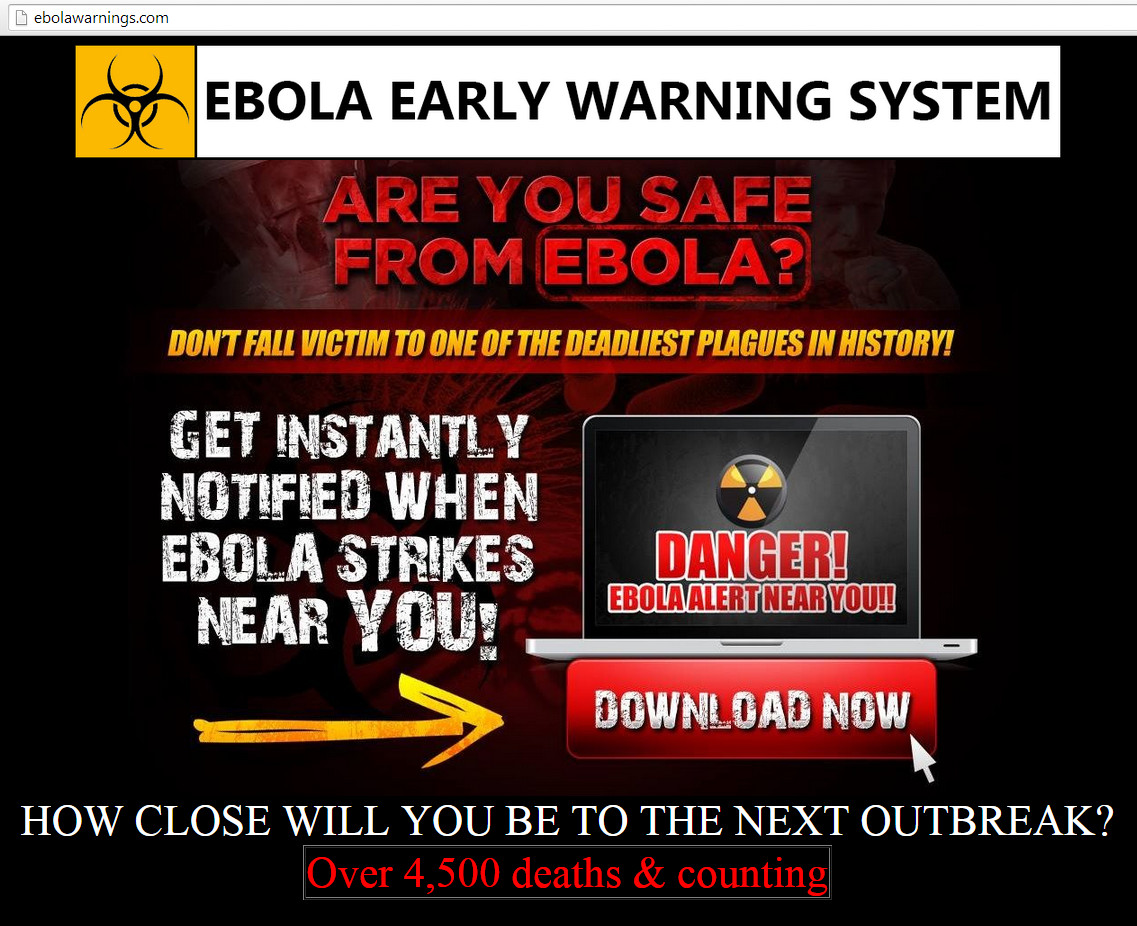
click to enlarge
Upon initial visit to the page, users are presented with the following prompt at the top-middle part of the screen:
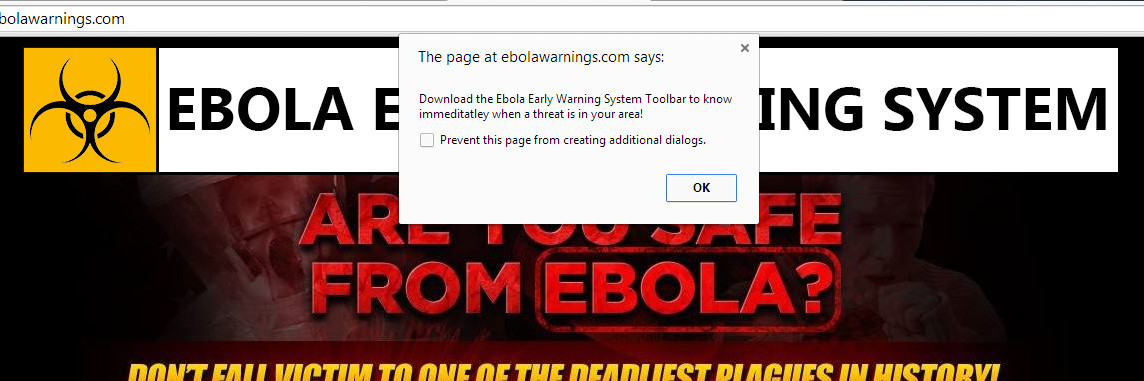
Download the Ebola Early Warning System Toolbar to know immediate when a threat is in your area.
Below is a screenshot of the downloaded file with an overview of its details:
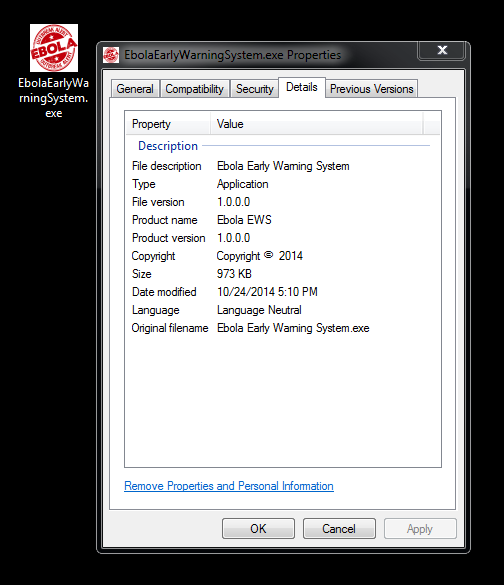
EbolaEarlyWarningSystem.exe has a low detection rate as of this writing—four vendors detect it out of 53. Thankfully, Malwarebytes Anti-Malware users are protected from this file, which we detect as Trojan.MSIL.
Upon execution, however, it displays a user interface prompting users to install the ONLY Search toolbar with links to its EULA and Privacy Policy pages.
Once users click the “Agree” button, they are again presented with other offers to download, such as a program called Block-n-Surf (a supposed tool used to protect children from adult-related content, System Optimizer Pro (a tool that purportedly optimizes the user’s system), oneSOFTperday (a tool that gives users access to free apps), and a remote access tool among others:
Once programs are installed, the following have been observed from affected systems:
- All browser default search pages are changed to ONLY Search
- Once users open a new browser tab, affiliate sites are loaded up (e.g. a site offering insurance)

- Browser windows open to prompt user to install more programs

- System Optimizer Pro executes
- Affected machine slows down
- Shortcut files are created on the desktop
During testing, we haven’t seen any installation of the Ebola Early Warning System toolbar or evidence of warning alerts.
We implore users not to be easily swayed with software solutions banking on the Ebola scare. They may be more about enticing internet users into downloading programs that may potentially do harm on their systems, instead of helping them be aware of the current situation.
Jovi Umawing











