Security firm FireEye released a report on June 23 about targeted attacks leveraging a Flash Player zero-day vulnerability (CVE-2015-3113) in Adobe Flash Player up to version 18.0.0.160. The firm stated that some users would receive a phishing email containing a link to a site hosting the zero-day exploit.
The announcement went out around the same time as Adobe’s security bulletin and a fix for the flaw.
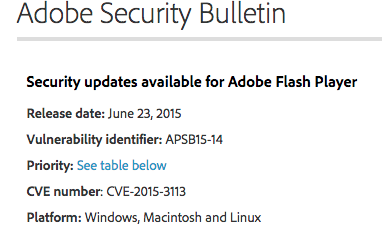
Adobe associated a Priority 1 rating to this patch:
This update resolves vulnerabilities being targeted, or which have a higher risk of being targeted, by exploit(s) in the wild for a given product version and platform. Adobe recommends administrators install the update as soon as possible. (for example, within 72 hours).
That severity level was well justified as threat actors wasted no time in studying and incorporating this new ammo into their arsenal. Indeed, only four days after the announcement (spotted by MalwareDontNeedCoffee), the vulnerability was already active in a popular exploit kit dubbed Magnitude.
For many users this is cutting it really short to be able to patch their software in due time. Without a doubt, this new exploit is going to wreak havoc on a large number of vulnerable machines.
Malwarebytes Anti-Exploit users were already protected against this threat, even if they were late on patching:
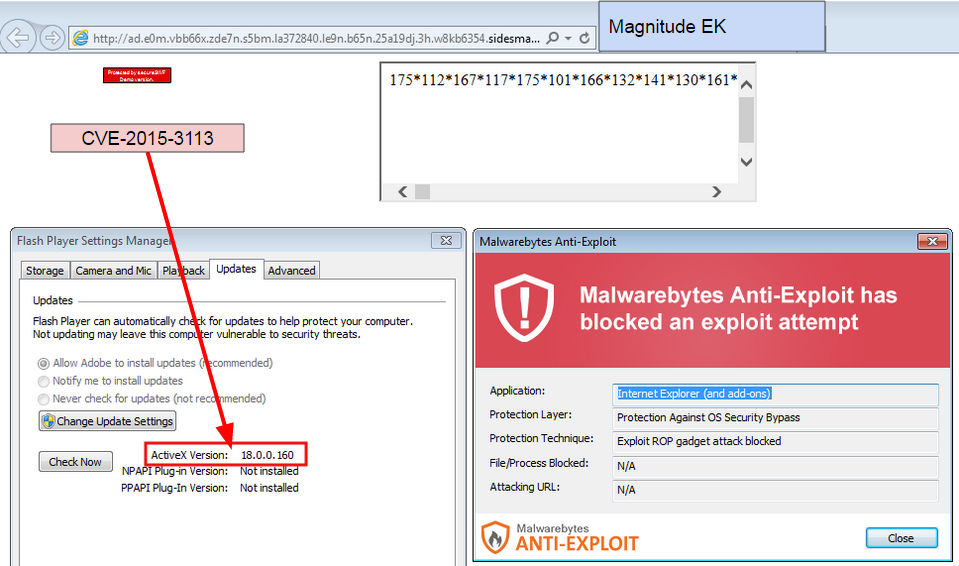
Magnitude EK uses the usual booby trapped SWF, followed by a malicious FLV (Flash Video) file.
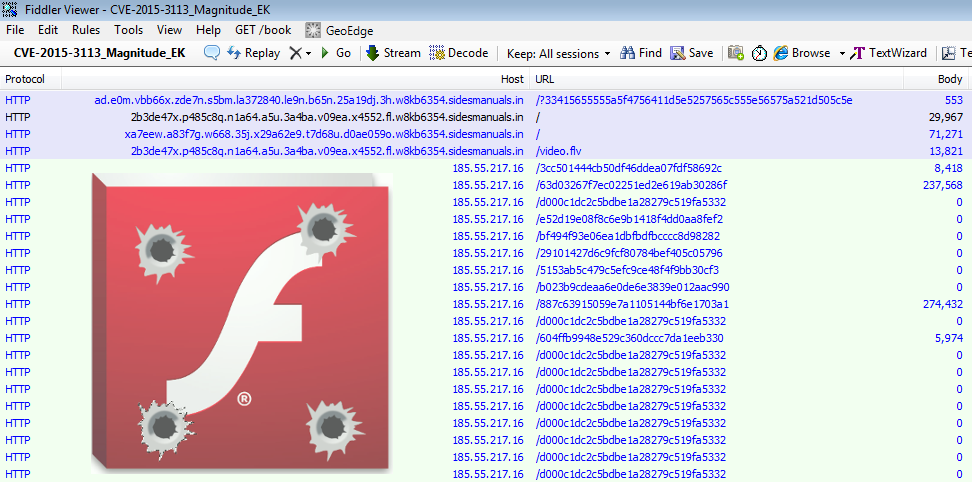
SWF file:
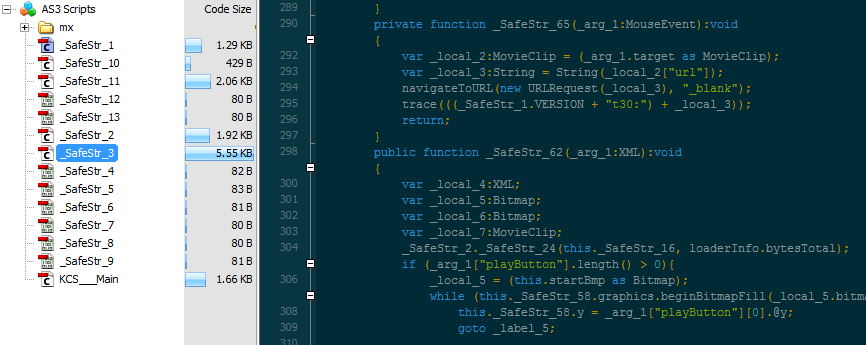
FLV file (metadata):
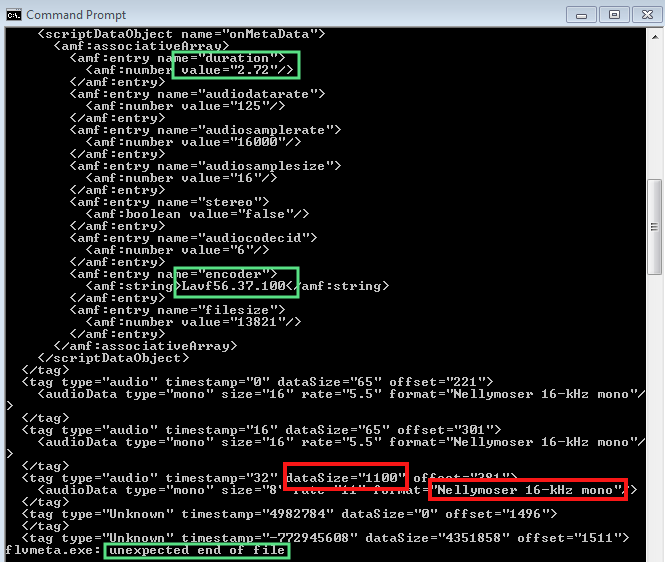
The Flash Video File exploits a heap buffer overflow vulnerability in the Nellymoser audio codec by exceeding its maximum length. This bug was also used previously in CVE-2015-3043 (Trend Micro details it here).
The plugin is a hacker’s favorite due to its huge user base and reusable security flaws. Indeed, attackers have the advantage as they can refactor an exploit to bypass a previous patch that didn’t completely address an insecure or complex coding implementation.
To keep or not to keep?
We can expect other exploit kits to follow suit very soon and start delivering this latest vulnerability. Without a doubt, this is the year of Flash zero-days and many are already suggesting to take drastic measures such as completely uninstalling the plugin.
For those not sure about this ‘all or nothing’ approach, a nice compromise can be reached by enabling “click-to-play”, a feature in all browsers that puts you in control to run the aforementioned plugin. A how-to guide is available here.
Regardless, we still urge everyone to update the Flash Player as soon as possible and employ a defense in depth strategy starting with anti-exploit technology to proactively mitigate weaponized vulnerabilities.










